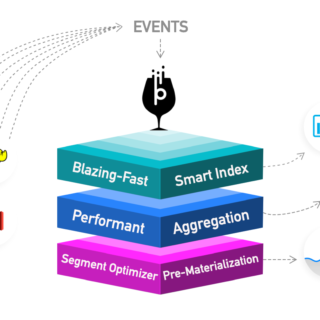
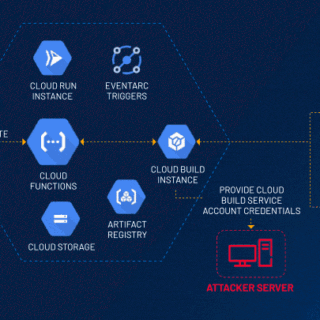
CVE-2024-39676: Apache Pinot Flaw Exposes Sensitive Data, Urgent Upgrade Needed
Apache Pinot, a real-time analytics open-source platform for lightning-fast insights, effortless scaling, and cost-effective data-driven decisions, has recently disclosed a serious security vulnerability (CVE-2024-39676). This flaw could allow unauthorized actors to access sensitive system...