Researcher released the technical details for CVE-2022-32898 in iOS 16

Security researcher Mohamed Ghannam (@_simo36) has published the exploit code for a vulnerability in the iOS kernel that could help an attacker execute arbitrary code with kernel privileges.
Tracked as CVE-2022-32898 (CVSS score of 7.8), the security defect was identified while reverse-engineering the process by which the Apple Neural Engine loads a model in the kernel level, with a patch available since the release of iOS 15.7 and iPadOS 15.7, iOS 16, macOS Ventura 13, watchOS 9.
Successful exploitation of the vulnerability would allow the attacker to be able to execute arbitrary code with kernel privileges on the target system.

Ghannam released the technical details for the security flaw and explained how to find a flaw in the Apple Neural Engine component.
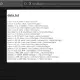
“The ZinComputeProgramGetNamesFromMultiPlaneLinear() and ZinComputeProgramGetNamesFromMultiPlaneTiledCompressed() functions are both responsible for parsing the procedure input and output, or more precisely, the LC_THREAD command with thread flavor 2 (ane_bind_state) whose binding_type_info value is 4 and 5.” Ghannam wrote.
“Due to the lack of validation of how many planes a model can supply, kernel pointers could be written outside the bounds of the planes array, potentially leading to a many interesting memory corruption scenarios.”
Apple addressed CVE-2022-32898 in iOS 16 by introducing some validation checks in both vulnerable functions, limiting the supplied plane count to four entries.
Users are recommended to update to the latest version as soon as possible to mitigate possible threats.