2% of Amazon S3 public buckets are unprotected, lead to data corruption attacks, malware spreading, and ransomware attacks
The latest research released by French network security vendor HTTPCS on February 26, 2018, shows that 5.8% of all Amazon S3 buckets are publicly accessible and even 2% are publicly writable, so anyone can add, edit or delete the data in it, or even dump victim’s data for ransom.
The latest study, conducted by the French cybersecurity firm HTTPCS, is intended to conduct a status survey of each Amazon S3 bucket created prior to the September 2017 update.
In 2017, experts think a large number of publicly readable buckets is the main reason for the spike in data breaches.
The HTTPCS survey scanned over 100,000 S3 buckets and also searched for buckets that were made publicly available for anyone to add data to. Such buckets may be used to implement data ransomware attacks.

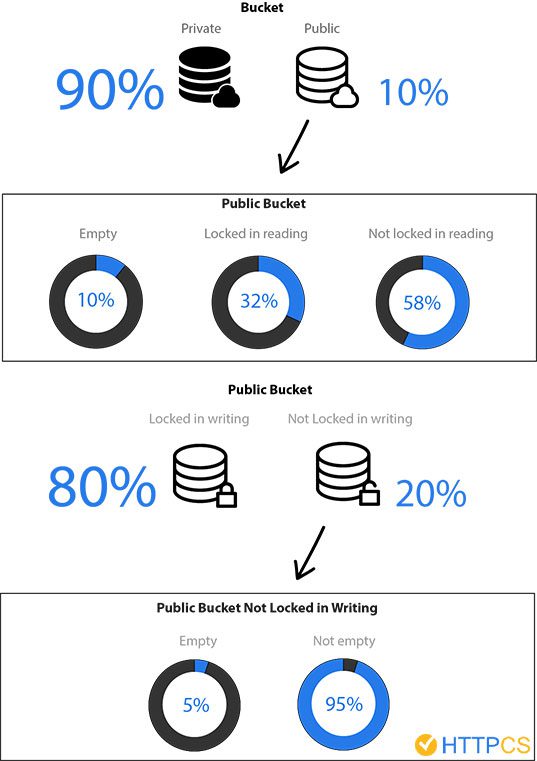
Image: httpcs
HTTPCS company’s experts found:
- 90% of Buckets are not public, therefore there is no risk of data leaks or corruption ;
- 58% of public Buckets (i.e. 5.8% of the total) contain readable files, what might allow data leakage ;
- 20% of public Buckets (i.e. 2% of the total) aren’t write-protected, what might lead to data corruption attacks, malware spreading, and even to ransomware attacks, as we could see in 2017 on poorly configured MongoDB databases ;
- only 5% of the Buckets which aren’t write-protected (i.e. 0.1% of the total) don’t contain any file, therefore the possibilities of large-scale attacks are quite real.
Source: httpcs