243 organizations worldwide were affected by Qrypter RAT
A security company Forcepoint found that in the past two years, a hacking organization claiming to be “QUA R&D” has been busy developing and improving a similar Malware-as-a-Service (MaaS) platform. In fact, QUA R&D developed malware products that have been sold under the name “Qrypter” but are often mistaken for Adwind by the security community.
Qrypter, first introduced in March 2016, is also known as Qarallax, Quaverse, QRAT or Qontroller. It is a remote-controlled Trojan that is based on Java development and uses a command and control (C&C) server based on onion (TOR) network.
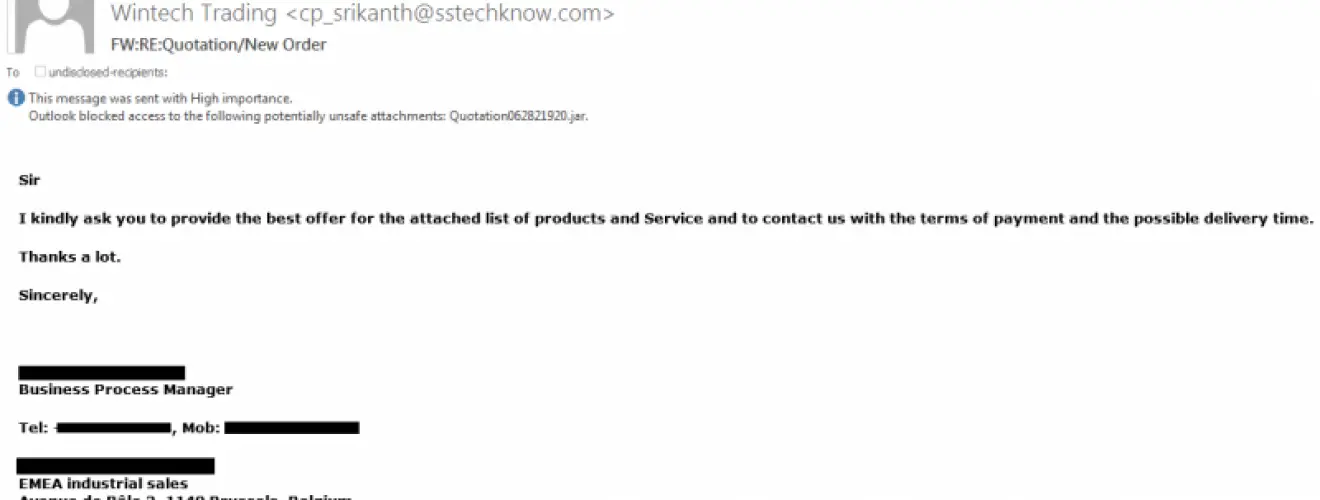
Qrypter was first disclosed in June 2016 and was being used to attack individuals who applied for a US visa in Switzerland. Now Forcepoint’s investigation confirms that Qrypter is still active and has been upgraded, and is usually spread through malicious e-mail distribution activities.

The malicious e-mail distribution activities used to spread Qrypter are usually represented by small-scale attacks, where attackers send only a few hundred e-mails at a time. However, the size of the scale does not determine the level of damage. It turns out that many organizations around the world have been affected by these attacks.
According to Forcepoint’s security research team, they discovered a total of three Qrypter-related malicious attacks in February of this year, and at least 243 organizations were affected.
 When executed on a victim system, Qrypter first places and runs two VBS script files in the %Temp% folder, with random file names designed to collect information on firewalls and anti-virus products installed on the computer.
When executed on a victim system, Qrypter first places and runs two VBS script files in the %Temp% folder, with random file names designed to collect information on firewalls and anti-virus products installed on the computer.
Qrypter then places and runs a .REG file in the %Temp% folder, which also uses a random file name. This file is used to reduce the overall security settings of the system and to block the execution of forensics and security-related processes contained in its preset list.
In addition, Qrypter will also delete a copy of itself and create the following registry as an automatic startup mechanism.
Researchers said that Qrypter is a plug-in-based backdoor that provides attackers with a variety of malicious operating functions: remote desktop connections, camera access, file system operations, additional file installations, and task manager controls.
Like Adwind, Qrypter also has a well-established business model. It rents for $80 a month and allows customers to make payments using PerfectMoney, Bitcoin-Cash or Bitcoin. In addition, customers can also receive discounts by paying a one-time fee of three months or one year.
It is understood that one of the bitcoin wallet addresses used by QUA R&D has received a total of 1.69 bitcoins, worth approximately $16,500. Of course, QUA R&D cannot use only one cryptocurrency purse, and the total income it receives will certainly be higher.
 In order to provide support to customers, QUA R&D has also launched a forum called “Black & White Guys” to discuss anything related to Qrypter MaaS. According to the information displayed by the forum, the forum currently has more than 2,325 registered members.
In order to provide support to customers, QUA R&D has also launched a forum called “Black & White Guys” to discuss anything related to Qrypter MaaS. According to the information displayed by the forum, the forum currently has more than 2,325 registered members.

It is worth noting that cracking competitors’ products seem to be an integral part of QUA R&D’s sales strategy. Forcepoint said that QUA R&D’s approach will enable anyone to obtain free and effective malware, which will greatly increase the utilization of malware and the incidence of cybercrime.
Source, Image: forcepoint






