A New Wave of SHTML Phishing Attacks Exploits User Curiosity
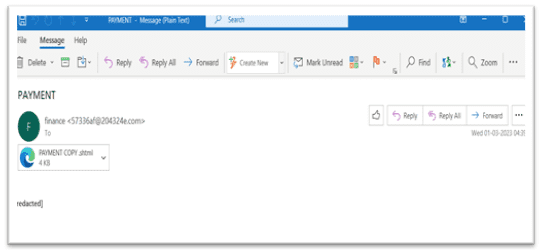
McAfee Labs has recently discovered a new series of phishing attacks that leverage server-parsed HTML (SHTML) files to redirect users to malicious websites or harvest their sensitive information through phishing forms. These SHTML files are often distributed as email attachments, with attackers exploiting various sentiments such as payment confirmations, invoices, or shipping notifications to trick recipients into opening them. In some cases, these emails include a small message thread to pique the user’s curiosity further.

Email with SHTML attachment | Image: McAfee
When the SHTML attachment is clicked, it opens a blurred fake document accompanied by a login page in the browser. To access the document, the user is prompted to enter their credentials, with the email address sometimes prefilled. Attackers typically employ JavaScript within the SHTML attachments to create the phishing form, redirect users, or conceal malicious URLs and activities.
The blurred background images used in these attacks are often sourced from legitimate websites like isc.sans.edu and i.gyazo.com. In addition, phishing attacks abuse static form service providers such as Formspree and Formspark to steal sensitive user information.
Formspree.io is a back-end service that allows developers to add forms to their websites without writing server-side code. It handles form processing and storage and sends submitted information to an email address. Attackers utilize the Formspree.io URL as an action URL, defining where the submitted data will be sent. Once a user enters their credentials and clicks “submit,” the information is sent to Formspree.io, which then forwards it to the attacker’s specified email address.
To block known malicious forms and prevent data from being sent to attackers, some form submission services have implemented safeguards. If a user is successfully phished, the attacker may redirect their browser to an unrelated error page associated with a legitimate website to avoid raising suspicion.
Phishing remains a significant and pervasive problem in the realm of cybersecurity. Although these blurry image phishing scams employ basic HTML and JavaScript code, their simplicity can still effectively trick many users. To stay protected, users should keep their systems updated and avoid clicking links or opening SHTML attachments from untrusted email sources.