abuse-ssl-bypass-waf: Bypassing WAF by abusing SSL/TLS Ciphers
abuse-ssl-bypass-waf
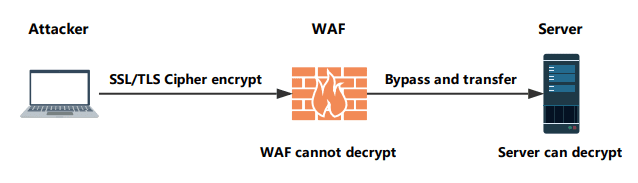
Helping you find the SSL/TLS Cipher that WAF cannot decrypt and Server can decrypt same time
Idea
Download
git clone https://github.com/LandGrey/abuse-ssl-bypass-waf.git
Usage
python abuse-ssl-bypass-waf.py --help
If you can find keyword or regex when hit the WAF page, you can use:
python abuse-ssl-bypass-waf.py -regex "regex" -target https://target.com
or you cannot find keyword or regex when filter by WAF, you can use:
python abuse-ssl-bypass-waf.py -thread 4 -target https://target.com
Notice: If you are worried about WAF drop the connection, you have better not use -thread option.
Third-party
curl
sslcan
Notice: If your operating system is not Windows, you should be modify config.py ,adjust curl and sslscan path & command values.
Running
If you don’t know what the type of the WAF, you can compare the html response content length and try to find the bypassing WAF cyphers
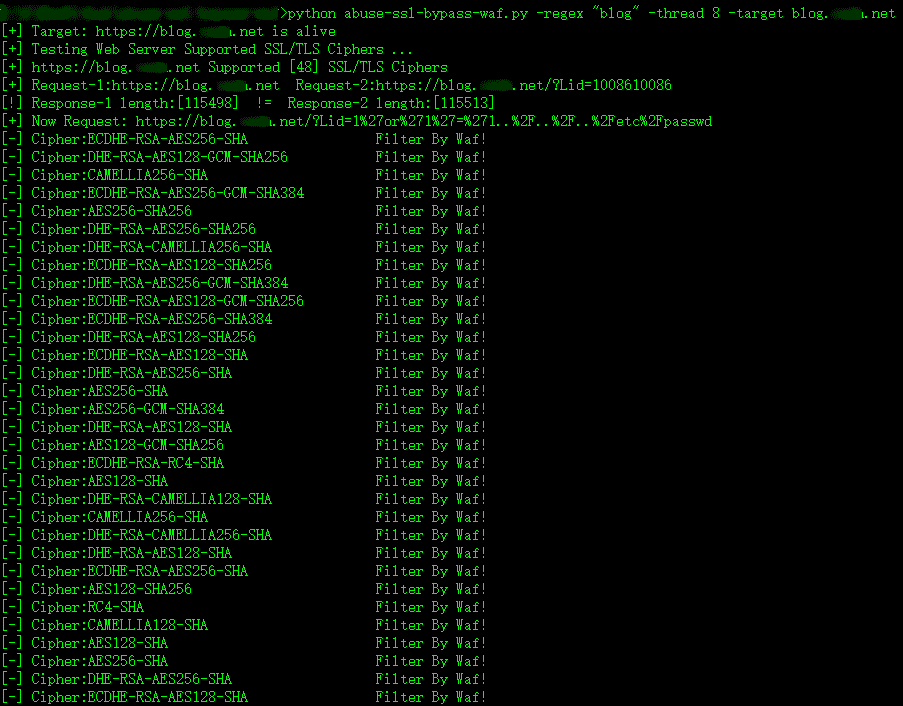
knowing the hit WAF page keyword or regex:

When using some SSL/TLS cyphers request the payload URL, If WAF keyword or regex not in an html page, there is a way of bypassing WAF using Cipher!
Source: https://github.com/LandGrey/