Addressing Microsoft Exchange Server’s Critical Vulnerability: A Step-by-Step Guide
When it comes to corporate email solutions, Microsoft Exchange Server is a dominant player. It handles countless vital communications daily, making its security paramount. Unfortunately, like many complex pieces of software, vulnerabilities arise. The recent revelation of CVE-2023-21709 put many administrators on high alert, and Microsoft’s response offers a path to securing servers.

Before we dive into the mitigation process, it’s crucial to comprehend the nature of this vulnerability. CVE-2023-21709 (CVSS score of 9.8) exposes Exchange servers to privilege escalation attacks. In layman’s terms, it means that an unauthenticated attacker, with the right tools and approach, can up their privileges on vulnerable Exchange servers, without requiring any user intervention.
The vulnerability creates an avenue for network-based attackers to brute force user account passwords. The significant takeaway here is that once successful, these attackers can gain access as that user, causing potential harm.
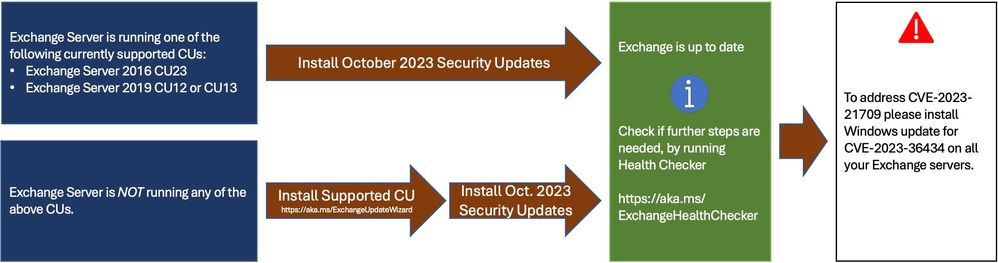
Microsoft was swift in its efforts to address the vulnerability. An initial patch was released in August. However, as with all evolving threats, a more effective fix has now been made available. Exchange administrators need to take manual actions for optimal security.
Step-by-Step Remediation Guide
1. Did Nothing Yet? Here’s What to Do:
Install the update for CVE-2023-36434 on all Exchange Servers.
2. Acted on Microsoft’s August 2023 Recommendation?
If you disabled the Token Cache module (either by the provided command or using Microsoft’s script) or have performance concerns since the module’s deactivation, here’s your action plan:
Step 1: Install the update for CVE-2023-36434 on all your Exchange Servers.
Step 2: Reactivate the IIS Token Cache module. Choose one of the two methods:
For an Individual Server:
New-WebGlobalModule -Name “TokenCacheModule” -Image “%windir%\System32\inetsrv\cachtokn.dll”
For All Servers in the Organization:
After installing the Windows Updates, run the CVE-2023-21709.ps1 script as an Administrator in the Exchange Management Shell (EMS) using:
.\CVE-2023-21709.ps1 -Rollback
Microsoft has issued a more effective patch for the severe Microsoft Exchange Server vulnerability CVE-2023-21709. Organizations should install the patch as soon as possible to protect themselves from this vulnerability.