Agrigento: identify privacy leaks in Android apps
Agrigento
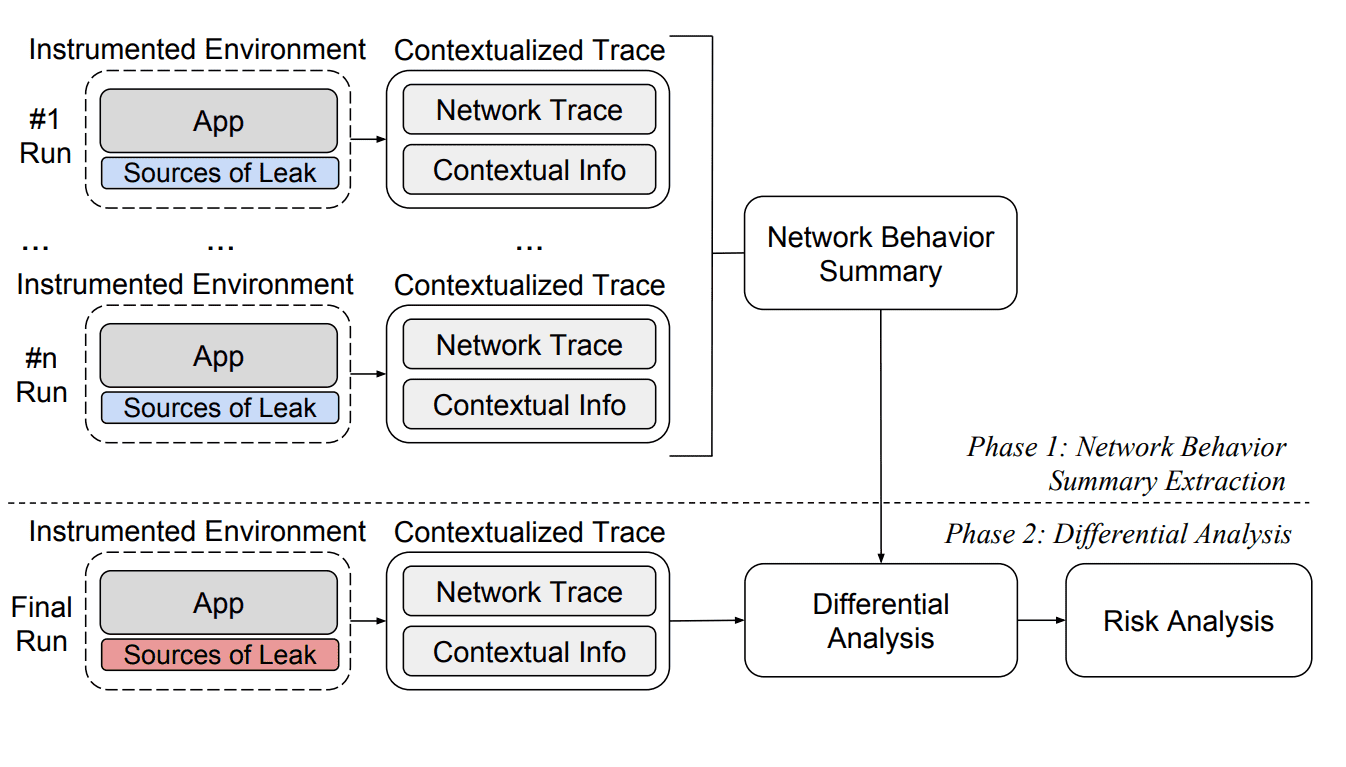
Agrigento is based on black-box differential analysis, and it works in two steps: first, it establishes a baseline of the network behavior of an app; then, it modifies sources of private information, such as the device ID and location, and detects privacy leaks by observing deviations in the resulting network traffic. The basic concept of black-box differential analysis is not novel, but, unfortunately, it is not practical enough to precisely analyze modern mobile apps. In fact, their network traffic contains many sources of non-determinism, such as random identifiers, timestamps, and server-assigned session identifiers, which, when not handled properly, cause too much noise to correlate output changes with input changes. The main contribution of this work is to make black-box differential analysis practical when applied to modern Android apps.

Agrigento is able to eliminate the different sources of non-determinism by intercepting calls from the app to certain Android API calls and recording their return values, and in some cases replacing them (either by replaying previously seen values or by returning constant values).
- Agrigento records the timestamps generated during the first run of each app and replays the same values in the further runs.
- It records the random identifiers (UUID) generated by the app.
- It records the plaintext and ciphertext values whenever the app performs encryption.
- The instrumented environment sets a fixed seed for all random number generation functions.
- It replaces the values of system-related performance measures (e.g., free memory, available storage space) with a set of constants.
Install
git clone https://github.com/ucsb-seclab/agrigento.git
cd agrigento/src
./install.sh
Agrigento requires other modules to be installed on the Android device:
- [Xposed].
- [CryptoHooker] – Collect contentextual information.
- [Changer] – Modify the values of private information sources.
- [JustTrustMe] – Handle certificate pinning.
- [Android Mock-location] – Allow to set mock location through ADB.
Also, Agrigento requires the permissions/capabilities to set iptables.
Config
general_config.py
RUNS_PER_APP: Number of times each app is executed.
FLOWS_FOLDER: Folder where to store the collected flows.
CRYPTOHOOKER_LOGS_FOLDER: Folder where to store the CryptoHooker logs.
WHITE_TREES_FOLDER: Folder where to store the results of the differential analysis.
values.py
Set the values of private information sources.
proxy_config.py
Set PROXY_IP, PROXY_PORT, and IFACE.
Run
Runs an APK multiple times on the given device, collects flows and CryptoHooker logs in the destination folders. Then changes all the values of private information sources, runs the APK again and performs the differential analysis. If any difference is detected, runs again the APK by changing one information source at the time.
python analyze-app.py <device_name> <apk_path>
Performs the differential analysis of all the collected data for a given app.
python analyze-leaks.py <app_name> [<num_runs> <flows_folder> <cryptohooker_logs_folder> <white_trees_folder>]
Runs the app multiples times without altering the values of private information sources.
python analyze-app-fps.py <device_name> <apk_path>
Performs the differential analysis without leveraging contextual information.
python analyze-randomness.py <app_name> [<num_runs>]
Performs the differential analysis step by step until convergence.
python simulate-convergence.py <app_name> <flows_folder> <cryptohooker_logs_folder> <white_trees_folder> [<convergence_threshold>]
Copyright (C) 2017 conand
Source: https://github.com/ucsb-seclab/





