Akamai Unveils New VPN Post-Exploitation Techniques: Major Vulnerabilities Discovered in Ivanti and FortiGate VPNs

Akamai researchers have exposed a series of vulnerabilities and techniques that could allow threat actors to further escalate their attacks after compromising a Virtual Private Network (VPN) server. The analysis focuses on vulnerabilities found in two popular VPN products: Ivanti Connect Secure and FortiGate VPNs. These findings highlight the potential for VPN servers, once compromised, to serve as gateways to critical network assets, threatening the overall security of an organization’s infrastructure.
VPN servers have long been a target for cybercriminals due to their internet accessibility and the significant attack surface they present. Historically, attackers have primarily exploited VPN servers to gain initial access to an internal network. However, Akamai’s latest research challenges the conventional view of VPN exploitation by exploring the untapped potential for post-exploitation techniques.
According to the report, attackers who successfully compromise a VPN server can use various methods to escalate their privileges, maintain persistence, and pivot to other critical network assets. These techniques, collectively referred to as “living off the VPN,” enable attackers to exploit the existing functionality of VPN servers without relying on complex custom implants, making these methods accessible to a broader range of threat actors.
Akamai’s researchers identified two critical vulnerabilities affecting Ivanti Connect Secure and FortiGate VPNs. The vulnerabilities have been assigned CVEs (Common Vulnerabilities and Exposures) by the vendors:
- CVE-2024-37374: A hard-coded encryption key issue in Ivanti Connect Secure that could allow attackers to decrypt sensitive information stored in VPN configuration files.
- CVE-2024-37375: A vulnerability in Ivanti’s Mobile Device Management (MDM) cleartext password handling, which could be exploited to capture credentials.
In addition to these CVEs, the researchers discovered a set of no-fix techniques that could be used to compromise credentials, capture sensitive data, and escalate privileges without requiring full remote code execution (RCE) on the VPN server.
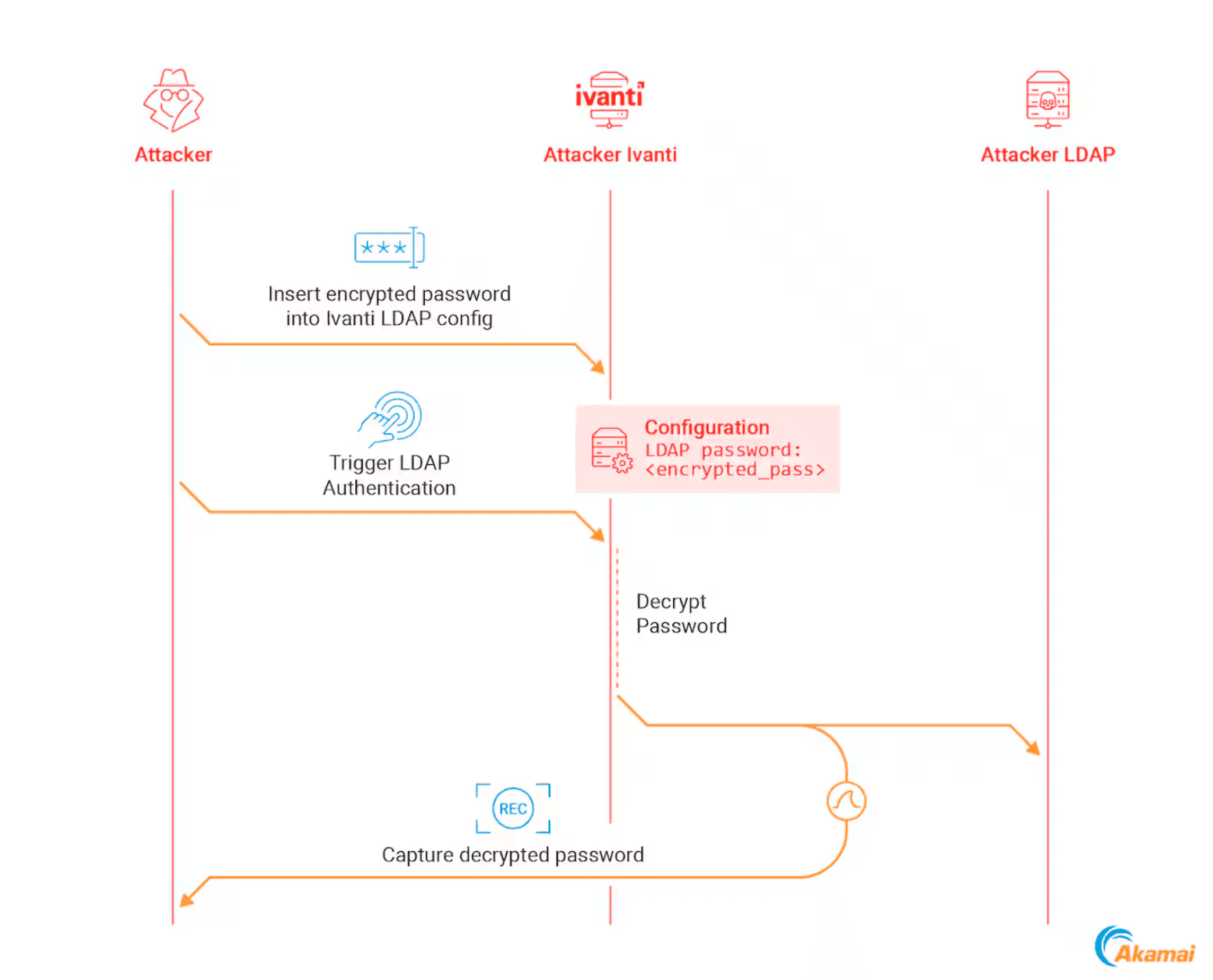
The decryption process of an Ivanti password in an attacker lab environment | Image: Akamai
While Ivanti acknowledged the vulnerabilities and assigned CVEs, Fortinet initially concluded that the described issues did not require a fix. However, following additional consideration, Fortinet decided not to address the custom encryption key bypass, claiming that it “does not cross a security boundary.”
One of the key insights from the report is the ability of attackers to exploit VPN management interfaces to achieve their objectives. By gaining access to the management interface through methods such as authentication bypass vulnerabilities or phishing attacks, threat actors can manipulate the VPN server’s configuration to capture credentials and perform other malicious actions.
For instance, the report highlights how attackers could intercept Lightweight Directory Access Protocol (LDAP) credentials by downgrading secure configurations to plaintext communication, allowing them to capture cleartext passwords. Additionally, attackers could register rogue authentication servers to capture any credentials submitted by users or administrators, effectively hijacking the authentication process.
Perhaps the most concerning finding in Akamai’s research involves the decryption of secrets stored in VPN configuration files. Both Ivanti and FortiGate VPNs were found to store sensitive information, such as user passwords and service account credentials, in an encrypted form within their configuration files. However, the encryption methods employed by these devices were found to be flawed.
For FortiGate, researchers discovered that all secrets are encrypted using a single hard-coded key, which is shared across all FortiGate appliances. Despite a fix being implemented in response to a previous CVE (CVE-2019-6693), many FortiGate devices still use the default key, leaving them vulnerable to decryption attacks. Even in cases where administrators have changed the key, attackers with control over the VPN server can revert the encryption back to the default key, making it easy to extract sensitive data.
The findings from Akamai’s report underscore the importance of robust security practices when deploying and managing VPN servers. Organizations must assume that their VPN servers are attractive targets for attackers and take proactive steps to mitigate the risks associated with post-exploitation techniques.





