Akira Ransomware Exploit CVE-2024-40766 in SonicWall SonicOS
The notorious Akira ransomware group continues to adapt and refine its methods, solidifying its position as one of the most significant threats in the cyber landscape. According to a recent report from Cisco Talos, Akira’s success lies in its constant evolution and tactical shifts, as the group moves beyond traditional ransomware techniques to remain a potent force in the realm of cybercrime.
A key highlight from the Cisco Talos report is the observation of Akira’s novel iteration targeting both Windows and Linux hosts. “Akira continues to cement its position as one of the most prevalent ransomware operations in the threat landscape,” the report states. The group has demonstrated agility, deploying new versions of its ransomware encryptor throughout 2024. Earlier in the year, Akira developed a Rust variant of their ESXi encryptor, abandoning C++ in favor of more efficient programming techniques.
This evolution marks a pivotal shift in the group’s technical approach, with significant updates in their encryption and exfiltration strategies. The new encryptor, particularly the Rust-based variant, highlights Akira’s drive for stability and efficiency, underscoring the adaptability of their affiliate operations. However, Cisco Talos recently observed a potential shift back to previous encryption methods alongside data theft extortion tactics.
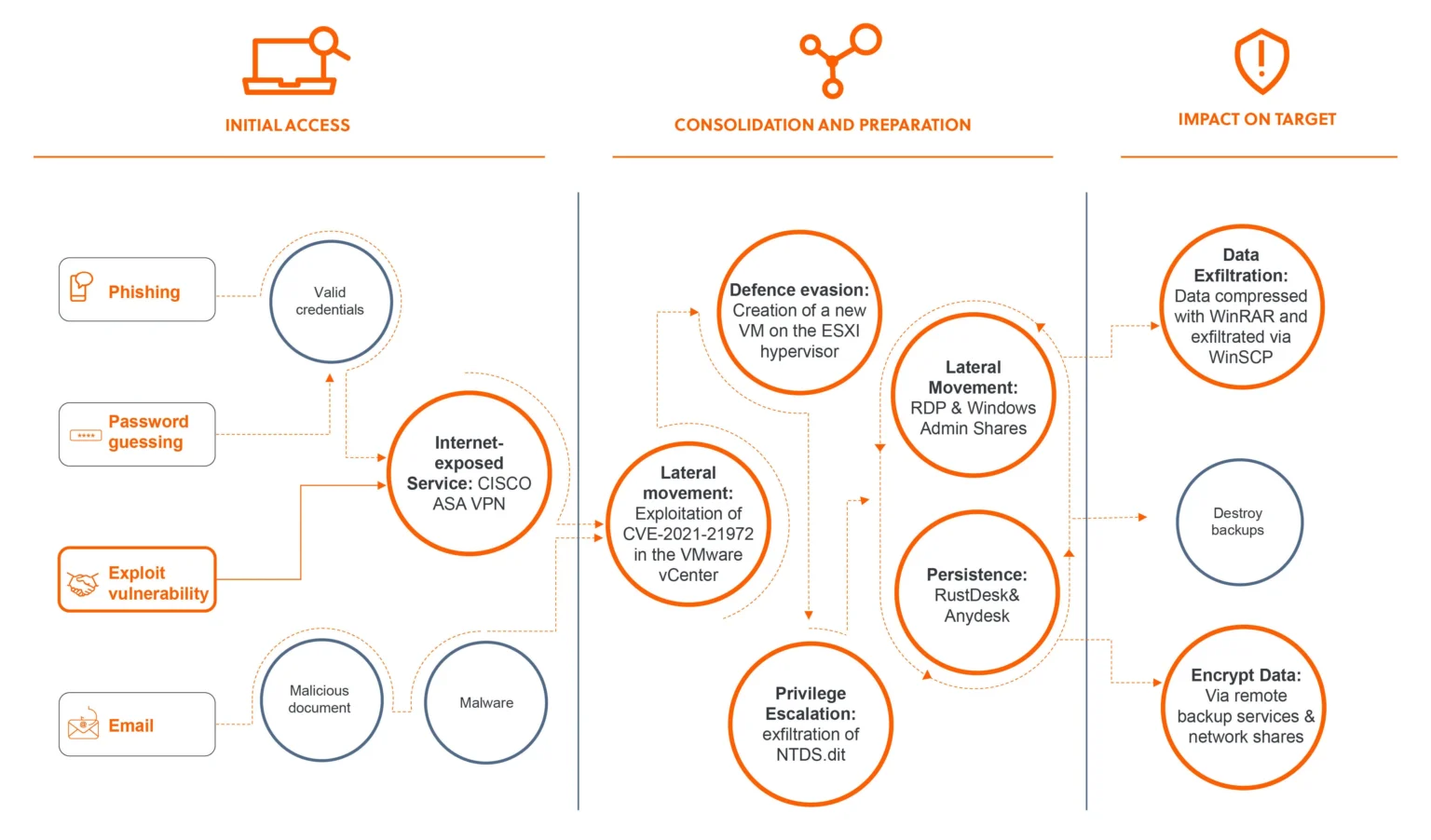
Affiliates of the Akira ransomware group have capitalized on exposed vulnerabilities, swiftly adapting to newly disclosed CVEs for initial access and privilege escalation within compromised environments. Most recently, Akira ransomware affiliates targeted vulnerable network appliances using CVE-2024-40766, an exploit found in SonicWall SonicOS, which facilitated remote code execution on affected devices. Other critical vulnerabilities abused by Akira affiliates include CVE-2020-3259 in Cisco Adaptive Security Appliances and CVE-2023-48788 in FortiClientEMS.
These tactics enable rapid deployment of ransomware and the exfiltration of victim data, a crucial step in Akira’s double extortion model. This method not only encrypts the victim’s files but also threatens to leak sensitive data if the ransom demands are not met, providing Akira with substantial leverage over its victims.
Cisco Talos reports that the group may be transitioning from the Rust-based Akira v2 variant back to earlier Windows and Linux encryptors written in C++. This tactical pivot suggests a refocus on time-tested techniques, allowing the ransomware to maintain operational stability while continuing to target multiple operating systems.
Akira’s evolving approach to encryption includes the use of the ChaCha8 stream cipher in newer variants, prioritizing efficiency and speed during ransomware attacks. The swift encryption and exfiltration operations allow the ransomware group to maximize damage in a short timeframe, as demonstrated in their recent attacks on manufacturing and technical services sectors.
The Cisco Talos report warns that Akira is likely to continue its campaign of exploiting high-impact vulnerabilities, especially in enterprise environments such as VMware ESXi and Linux servers. These platforms, which host critical infrastructure and high-value data, are attractive targets for ransomware operators seeking to inflict widespread disruption with minimal lateral movement. “We anticipate Akira will continue refining its tactics, techniques, and procedures (TTPs), developing its attack chain, adapting to shifts in the threat landscape, and striving for greater effectiveness in its RaaS operations,” the report concludes.





