Alert: “Brokewell” Malware – New Threat Targets Bank Users with Remote Device Takeover

ThreatFabric has unveiled a sophisticated new Android malware strain named “Brokewell.” This potent threat combines extensive data theft capabilities with remote device control, allowing attackers to hijack infected phones for fraudulent financial transactions. The malware’s origins and rapid development signify a growing threat in the mobile banking sector.
Discovery of Brokewell
ThreatFabric’s analysts stumbled upon Brokewell through what appeared to be an innocuous browser update page. This method, a common tactic among cybercriminals, camouflages the malware download as a routine software update. Upon deeper analysis, it was revealed that this was no ordinary update but the deployment mechanism for a previously unseen mobile malware targeting Android devices.
Infiltration Tactics

Brokewell’s infiltration begins with a fake browser update page that downloads the malware onto the user’s device. The approach is designed to be unsuspecting and natural, lowering the victim’s guard as they believe they are simply updating their browser for enhanced performance.
Brokewell’s Capabilities
Once installed, Brokewell unleashes a range of functionalities that pose severe risks to the victim’s financial and personal data:
Data Theft
Brokewell is capable of performing overlay attacks, a prevalent tactic in Android banking malware, where it displays a bogus screen over legitimate banking apps to capture user credentials. Furthermore, it employs its own WebView to intercept cookies by overriding the onPageFinished method, thus capturing session cookies as soon as the user logs in.
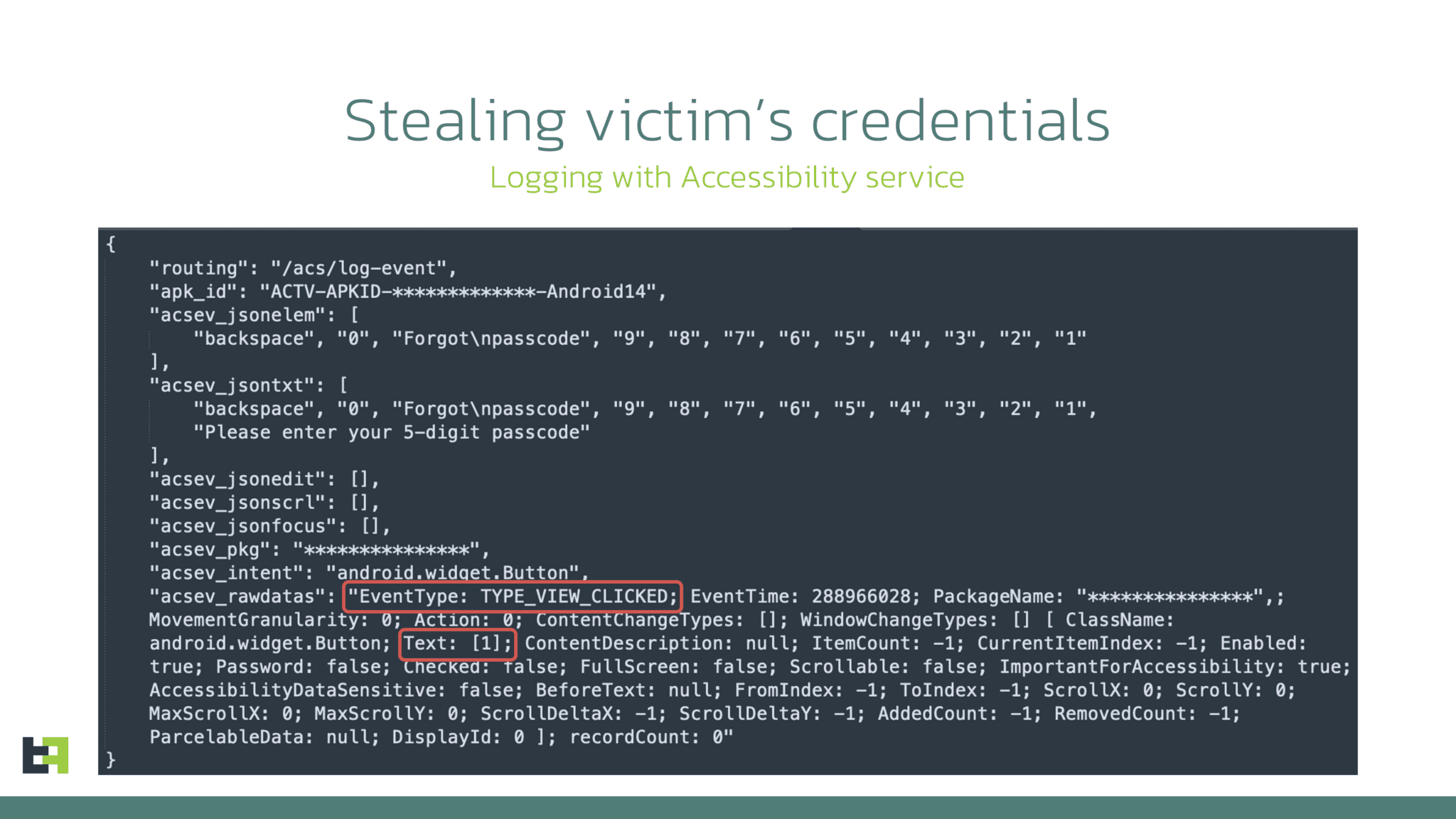
Accessibility Logging
Perhaps more alarming is Brokewell’s use of “accessibility logging” to capture every interaction on the device—be it touches, swipes, or keystrokes. This functionality allows it to log sensitive information from any app on the device, dramatically broadening the scope of data compromise.
Spyware Features
Brokewell extends its espionage capabilities by gathering information about the device, call history, and geolocation, and can even record audio, turning the victim’s device into a comprehensive spying tool.
Remote Control and Device Takeover
The ultimate threat posed by Brokewell comes from its remote control capabilities. After stealing credentials, the malware allows cybercriminals to perform actions on the device remotely, mimicking the user’s behavior. This includes screen streaming and executing touches, swipes, and clicks, enabling fraudsters to bypass traditional security measures like two-factor authentication.
The Actor Behind Brokewell
During their investigation, ThreatFabric identified a new actor in the mobile malware arena—dubbed “Baron Samedit.” This actor was linked to a repository named “Brokewell Cyber Labs,” which not only hosts the malware but also offers tools designed to bypass Android 13+ restrictions. This development is concerning as it lowers the entry barrier for new cybercriminals, potentially leading to a surge in mobile malware incidents.
A Call to Action
Brokewell stands as a potent reminder that banking malware is reaching new levels of sophistication. Proactive steps from end-users, financial institutions, and the broader security community are essential to protect sensitive data and financial assets in the face of this rapidly changing threat environment.