Android/Xamalicious Malware Hijacks 327K+ Android Devices
In the ever-evolving world of cyber threats, a new player has emerged in the Android ecosystem, known as “Android/Xamalicious.” This backdoor, discovered by the McAfee Mobile Research Team, represents a new wave of sophisticated cyber threats targeting Android devices.
Android/Xamalicious, developed using the open-source Xamarin framework, showcases an alarming level of sophistication. It initially seeks to gain accessibility privileges through social engineering. Once these privileges are secured, the backdoor establishes communication with a command-and-control server. This connection determines whether to download a second-stage payload, dynamically injected as an assembly DLL, enabling full control over the infected device.
“Count Easy Calorie Calculator” was available on Google Play on August 2022 and carries Android/Xamalicious | Image: McAfee Mobile Research Team
The second-stage payload of Android/Xamalicious is where its true danger lies. With the ability to fully control the infected device, this malware can perform a range of fraudulent actions such as ad-clicking, app installation, and more, all without the user’s consent. This behavior not only compromises user security but also fuels financially motivated ad-fraud schemes.
The use of Xamarin for building Android/Xamalicious has allowed the malware authors to remain undetected for extended periods. They have effectively utilized the framework’s build process to hide the malicious code. Further, the incorporation of obfuscation techniques and custom encryption makes detection and analysis even more challenging.

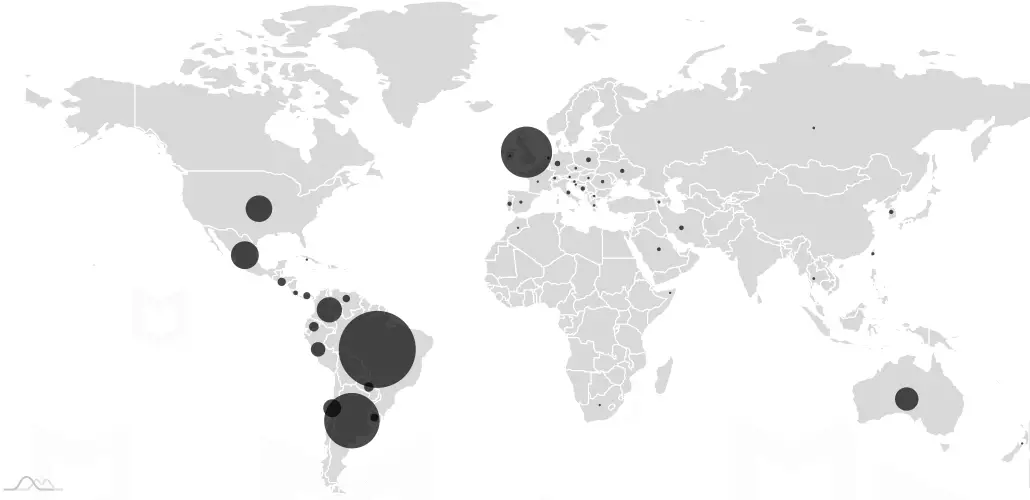
McAfee detections Android/Xamalicious around the world | Image: McAfee Mobile Research Team
Android/Xamalicious has been embedded in about 25 different apps, some of which were distributed on Google Play since mid-2020. These apps have been proactively removed, but the extent of the infection is significant. It’s estimated that at least 327,000 devices have been compromised, highlighting the widespread impact of this threat.
The emergence of Android/Xamalicious underscores the need for continuous vigilance in the digital space. Users are advised to be cautious of apps requiring unnecessary permissions and to install reputable security software to safeguard against such threats.






