Ant Media Server Flaw Grants Local Users Root Access (CVE-2024-32656)

A serious security vulnerability in Ant Media Server, a popular streaming solution used by thousands of organizations, has been uncovered by the Praetorian red team. This vulnerability, designated CVE-2024-32656, stems from a misconfiguration that allows any unprivileged local user on the system to escalate their privileges to root – the highest level of access.
Understanding Ant Media Server

Ant Media Server is a potent tool for organizations needing high-quality, low-latency video streaming, used by over 2000 enterprises globally. It supports a wide range of features and is trusted by businesses of all sizes. This vulnerability, however, highlights a potential weak point in its deployment.
The JMX Problem
At the root cause of the CVE-2024-32656 flaw lies Ant Media Server’s use of Java Management Extensions (JMX). JMX is designed for remote management and monitoring of Java applications. While powerful, it can introduce serious risks if not secured properly.
In this case, researchers found that:
- The Ant Media Server installation started a JMX service with remote access enabled.
- Critically, no authentication was required to connect to this service.
- The service was only bound to localhost, limiting direct remote attacks.
The Attack Path
Despite the localhost limitation, unprivileged users on the same system could exploit this vulnerability chain:
- Find the JMX Service: Scanning the system would reveal the open JMX port.
- Connect Without Credentials: Attackers could connect to the JMX service without providing any username or password.
- Load Malicious Code: Using specialized tools and techniques, attackers could inject a malicious “MBean” into the JMX process. This code would run with the same privileges as the Ant Media Server itself.
- Exploit to Root: Attackers could exploit the Ant Media Server process’s existing permissions, often including the ability to run privileged scripts, to gain full root access.
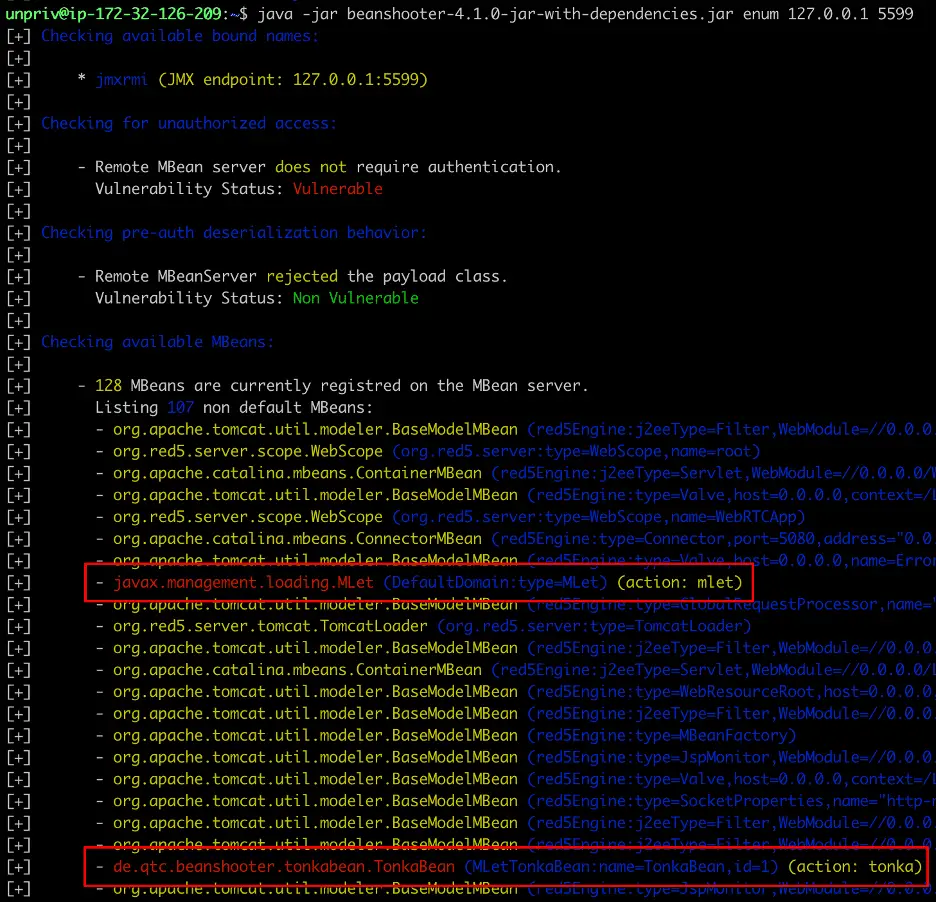
Successfully leveraged the MLet MBean to load malicious TinkaBean MBean into the victim Java process | Image: Praetorian
Consequences
With root access, an attacker has virtually unhindered control over the system:
- Data Theft: Stealing sensitive video streams, user data, or other confidential information.
- Sabotage: Disrupting streaming services or deleting important files.
- Lateral Movement: Using the compromised server as a base to attack other systems on the network.
Protect Your Systems
- Patch Ant Media Server: If you use Ant Media Server, the vendor has likely released an update to address this vulnerability. Apply it immediately.
- Audit JMX Use: Identify any other software using JMX within your environment and ensure they are properly secured.
- Follow Security Best Practices: Regular penetration testing and vulnerability scanning can help catch these types of issues before attackers exploit them.





