Argo CD Users Beware: CVE-2024-28175 (CVSS 9.0) – Critical XSS Vulnerability Exposed
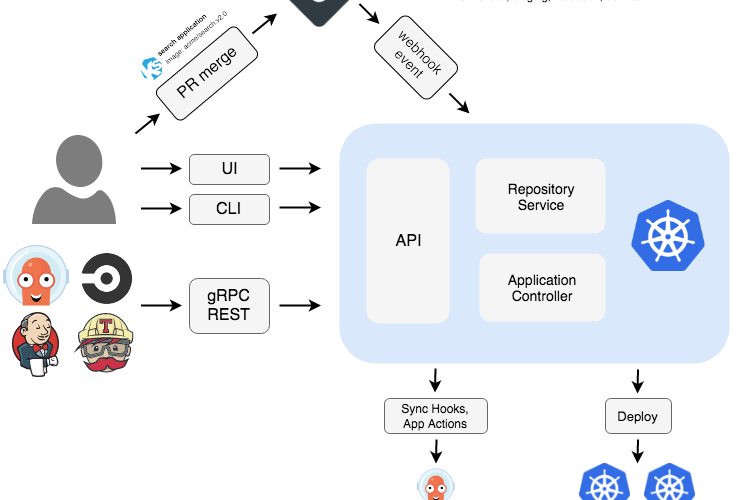
A serious cross-site scripting (XSS) vulnerability (CVE-2024-28175, CVSS 9.0) has been discovered in Argo CD, the widely used continuous delivery tool for Kubernetes. If left unpatched, attackers could exploit this flaw to inject malicious scripts into the Argo CD interface, potentially taking control of Kubernetes deployments with devastating consequences.
What’s at Risk
Successful exploitation of this XSS vulnerability could allow attackers to:
- Hijack User Sessions: Execute code with the permissions of the victim user (potentially up to full admin rights).
- Modify Deployments: Create, change, or delete Kubernetes resources.
- Steal Sensitive Data: Access confidential information within deployments.
- Launch Further Attacks: Use the compromised system as a launchpad.
The Exploit
The danger lies in the way Argo CD handles links defined using the link.argocd.argoproj.io annotation. Improper filtering opens a door for attackers to inject malicious javascript: links into the application summary. An unsuspecting user who clicks such a link would unwittingly trigger the attacker’s script.
RyotaK (@Ry0taK) is thanked for discovering and reporting this vulnerability.
Who’s Affected
All Argo CD users running versions before the following are vulnerable to CVE-2024-28175:
- v2.10.3
- v2.9.8
- v2.8.12
Immediate Action Required
Argo CD developers have released patches. Organizations relying on Argo CD must prioritize the following:
- Update Immediately: Deploy the appropriate patches as soon as possible.
- Review Permissions: If an immediate update isn’t feasible, limit who can edit Kubernetes resource manifests to minimize the attack surface.
Important Note: There are no foolproof workarounds. The safest alternative, if upgrading is not possible, would be to create a Kubernetes admission controller to reject any resources with an annotation starting with link.argocd.argoproj.io
or reject the resource if the value uses an improper URL protocol. This validation will need to be applied in all clusters managed by ArgoCD.