ArtiPACKED: A New GitHub Actions Vulnerability Exposes Critical Credentials
A recently uncovered vulnerability in GitHub Actions artifacts has the potential to compromise high-profile open-source projects and expose sensitive credentials, including GitHub tokens and third-party cloud service keys. Dubbed “ArtiPACKED” by Unit 42 researchers, the attack vector exploits a race condition in the handling of build artifacts, enabling unauthorized access and potential remote code execution.
At the heart of this vulnerability lies the misuse of GitHub Actions artifacts, a feature used to persist and share data across jobs within CI/CD workflows. Artifacts are typically generated during the build process and can include anything from compiled code to deployment packages. While these artifacts are essential for efficient workflow execution, they can also become a liability if not properly secured.
The ArtiPACKED vulnerability leverages a combination of misconfigurations and security oversights that result in sensitive tokens—such as GitHub tokens and third-party cloud service tokens—being inadvertently included in publicly accessible artifacts. This flaw allows malicious actors with read access to these artifacts to extract the tokens and use them to compromise the services they grant access to.
During their investigation, the Unit 42 team discovered that many popular open-source projects on GitHub were unknowingly exposing sensitive tokens through their artifacts. These tokens, particularly the GITHUB_TOKEN and ACTIONS_RUNTIME_TOKEN, are designed to authenticate and authorize actions against the repository. However, when these tokens are leaked, they can be used by attackers to push malicious code, access confidential data, or even gain high-level access to cloud environments.
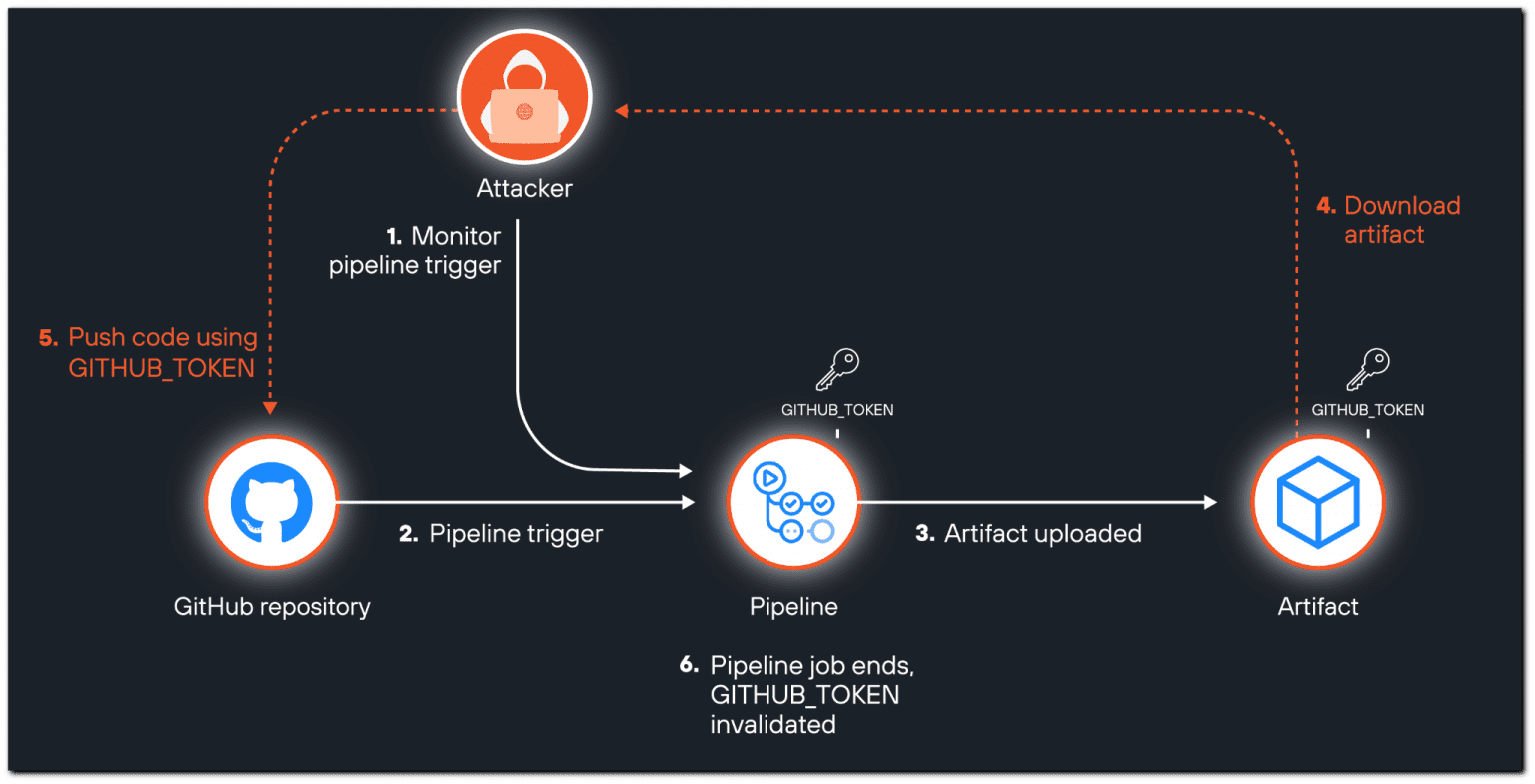
The race condition arises because GitHub’s recent update to the artifacts feature (version 4) allows artifacts to be downloaded while the workflow run is still in progress. This creates a narrow window of opportunity for attackers to download the artifact, extract the token, and use it to inject malicious code into the repository before the token expires.
In a demonstration by Unit 42, an attacker was able to exploit this race condition to create a branch in a popular open-source project maintained by Google, despite not having the necessary permissions. The potential impact of this vulnerability is enormous, as compromised repositories could lead to the deployment of malicious code in production environments, affecting millions of users.
The research conducted by Unit 42 revealed that several well-known organizations, including Google, Microsoft, Red Hat, Canonical, AWS, and OWASP, were affected by this vulnerability. Some of the high-profile projects that were found to be at risk included:
- firebase/firebase-js-sdk (Google)
- microsoft/TypeScript-repos-automation (Microsoft)
- adsys (Canonical)
- quay/clair (Red Hat)
- CycloneDX/cdxgen (OWASP)
These projects, which are used by millions of developers and organizations worldwide, could have been compromised if the vulnerability had been exploited before the maintainers patched their workflows.
To address this critical security gap, Unit 42 has developed a proof-of-concept custom action called upload-secure-artifact. This action integrates an open-source scanner into the artifact upload process, auditing the source directory for secrets and blocking the upload if any sensitive information is detected. By adopting this tool, organizations can significantly reduce the risk of accidental secret exposure in their CI/CD pipelines.
In addition to using tools like upload-secure-artifact, organizations should implement the following best practices to secure their GitHub Actions workflows:
- Minimize Token Permissions: Configure workflow tokens according to the principle of least privilege, ensuring they have the minimum permissions necessary to perform their tasks.
- Review Artifact Creation: Carefully review and sanitize the contents of artifacts before uploading them to ensure they do not contain sensitive information.
- Monitor and Audit: Regularly monitor and audit your CI/CD workflows for any signs of misconfiguration or potential security vulnerabilities.





