Async DNS Brute v0.3.3 releases: DNS asynchronous brute force utility
Async DNS Brute
A Python 3.5+ tool that uses asyncio to brute force domain names asynchronously.
Speed
It’s fast. Benchmarks on small VPS hosts put around 100k DNS resolutions at 1.5-2mins. An amazon M3 box was used to make 1 mil requests in just over 3 minutes. Your mileage may vary. It’s probably best to avoid using Google’s resolvers if you’re purely interested in speed.
DISCLAIMER
- Your ISP’s and home router’s DNS servers probably suck. Stick to a VPS with fast resolvers (or set up your own) if you’re after speed.
- WARNING This tool is capable of sending LARGE amounts of DNS traffic. I am not responsible if you DoS someone’s DNS servers.
Changelog v0.3.3
- output bug fixes
Installation
$ pip install aiodnsbrute
Usage
Example
Run a brute force with some custom options:
$ aiodnsbrute -w wordlist.txt -vv -t 1024 domain.com
Run a brute force, suppress normal output and send only JSON to stdout:
$ aiodnbrute -f - -o json domain.com
…for an advanced pattern, use custom resolvers and pipe output into the awesome jq:
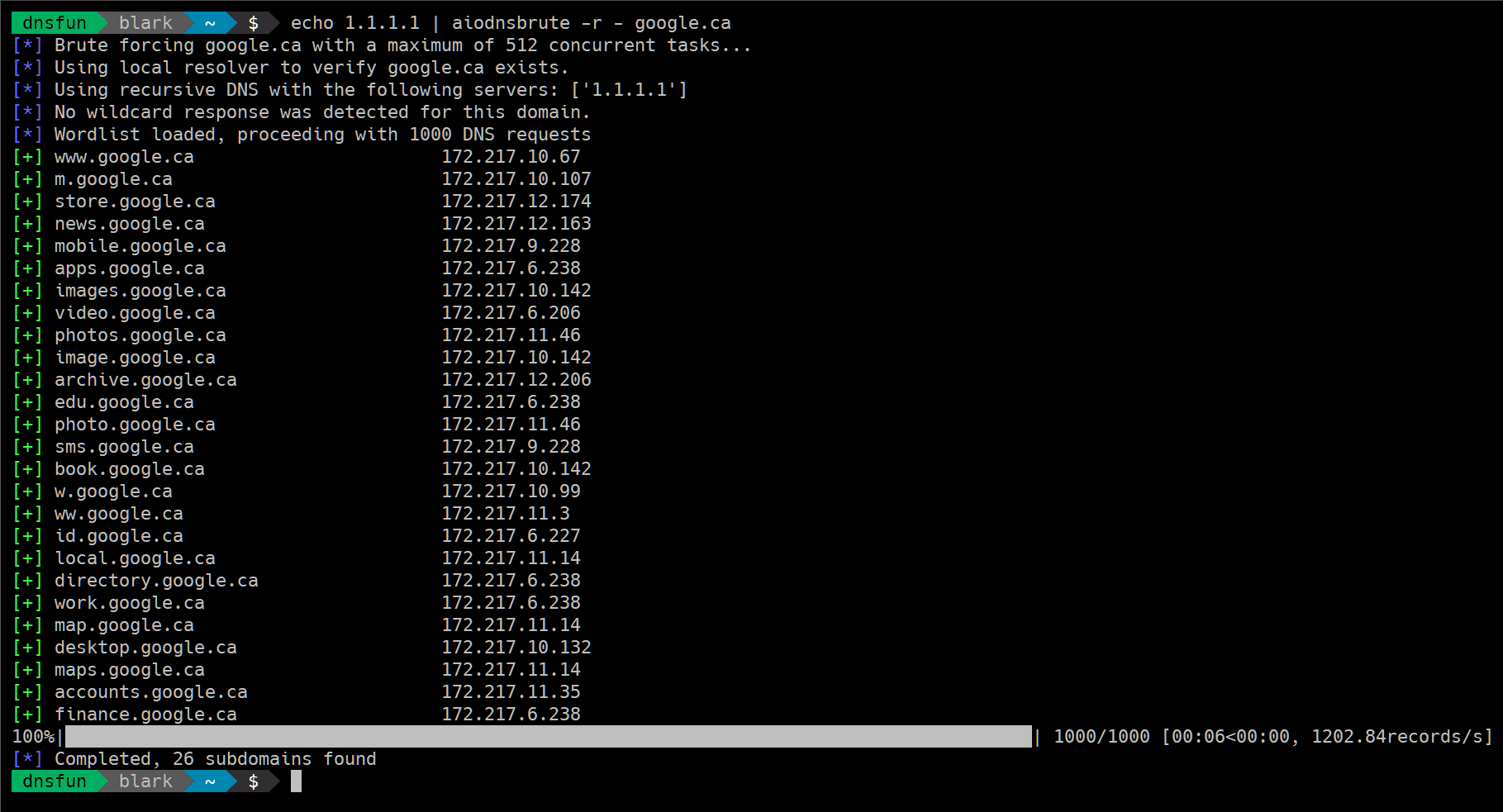
$ aiodnsbrute -r resolvers.txt -f – -o json google.com | jq ‘.[] | select(.ip[] | startswith(“172.”))’
Wildcard detection enabled by default (–no-wildcard turns it off):
NEW use gethostbyname (detects CNAMEs which can be handy for potential subdomain takeover detection)
$ aiodnsbrute --gethostbyname domain.com
Supply a list of resolvers from the file (ignoring blank lines and starting with #), specify -r – to read a list from stdin.
$ aiodnsbrute -r resolvers.txt domain.com
Copyright (C) 2019 blark
Source: https://github.com/blark/




