ATLAS LION Cybercriminal Group Persists in Targeting Gift Card Issuing Systems

A sophisticated cybercriminal group known as ATLAS LION (aka THIRSTY CAMELS, STORM-0539) continues to pose a significant threat to organizations, particularly those in the retail and consumer goods sectors. Since 2021, this group has specialized in compromising gift card issuing systems, resulting in substantial financial losses for targeted companies.
ATLAS LION employs a range of sophisticated tactics to infiltrate corporate networks, including phishing and smishing campaigns that leverage adversary-in-the-middle (AITM) phishing pages. These pages enable the group to steal credentials and session tokens, effectively bypassing multifactor authentication (MFA) protections. Additionally, the group demonstrates a deep understanding of cloud infrastructure and identity providers, allowing them to navigate complex environments and exploit vulnerabilities.
The group’s adaptability is evident in their frequent changes in phishing kits and infrastructure reuse. They often register long, fully qualified domain names (FQDNs) incorporating keywords related to their targets, and they have shown a preference for compromising existing domains rather than registering new ones. This dynamic approach makes detection and mitigation efforts more challenging for security teams.
Between February 2023 and June 2024, Intel471 identified 222 phishing sites linked to ATLAS LION. These sites were designed to harvest usernames, passwords, and MFA tokens, granting the threat actors access to virtual desktop infrastructures (VDIs). The phishing kits used varied, including themes mimicking Okta, Microsoft, Salesforce, and even Telegram. This diversity in phishing kits, often changing within a single week, contrasts with the more static approaches of other groups, such as the English-speaking Com cluster.
The image depicts the providers hosting suspected ATLAS LION infrastructure from Sept. 1, 2023, to June 6, 2024.
ATLAS LION is known for reusing infrastructure and deploying multiple phishing kits from the same IP address or compromised domain. For instance, they frequently use hosting providers like SERVERCENTRAL, DIALHOST, and ZAM LTDA, and register domains through services like PublicDomainRegistry.com, NameCheap, and GoDaddy. The group often takes over existing domains using compromised cPanel credentials, uploading phishing kits disguised as compressed archive files.
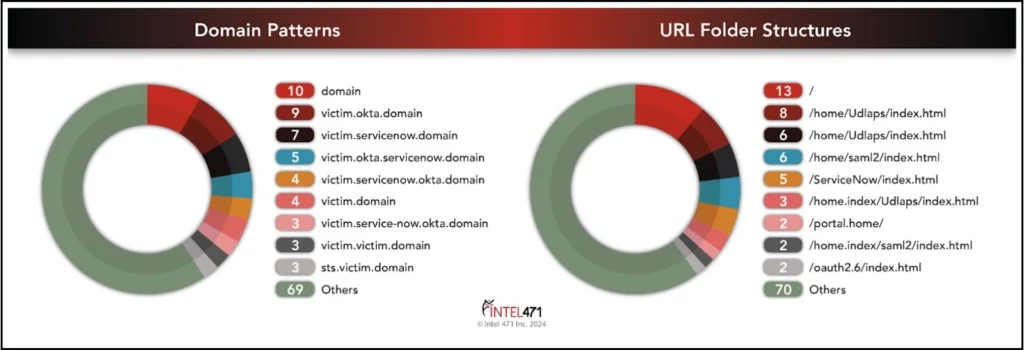
Their domain naming conventions frequently incorporate keywords related to their targets, such as Okta, ServiceNow, and SharePoint. This tactic helps them blend their malicious activities with legitimate services, further deceiving potential victims. The repeated use of “index.html” at the end of their URLs is a notable pattern observed in their campaigns.
Analysis of ATLAS LION’s activities reveals a strong focus on targeting entities in the consumer and industrial products sector, aligning with their primary objective of gift card fraud. However, the group has also been observed targeting organizations in other sectors, including professional consulting and financial services. The financial impact of their attacks can be significant, as stolen gift cards are easily monetized through resale on cybercriminal forums and marketplaces.





