Attackers Hijack 360 Total Security to Deliver SSLoad

In a recent attack discovered by ANY.RUN researchers, cybercriminals exploited 360 Total Security antivirus software to distribute a Rust-based malware known as SSLoad. This was achieved through the use of a new, highly deceptive loader called PhantomLoader, which was cleverly disguised as a legitimate module of the antivirus program.
By embedding itself into trusted software, PhantomLoader allows attackers to bypass traditional security defenses and deliver SSLoad undetected.
Overview of the Attack
According to the research by ANY.RUN, PhantomLoader disguises itself as a legitimate module for 360 Total Security. This tactic allows PhantomLoader to evade detection while delivering SSLoad.
The analysis revealed that one common method of distributing SSLoad is phishing emails containing malicious Office documents. Once a user opens the document, it triggers the infection process.
We can see this process by uploading a malware sample inside ANY.RUN’s sandbox.
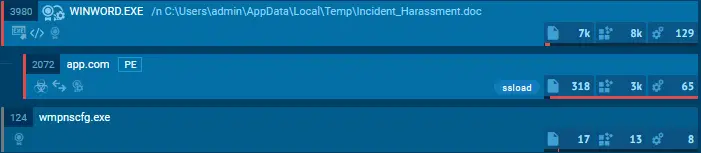
Malicious Word document in ANY.RUN’s sandbox
After the malicious Word document is executed, it initiates a new process, “app.com,” which is launched by “WINWORD.exe.” This indicates that a malicious macro embedded within the document has been executed, leading to the suspicious process.
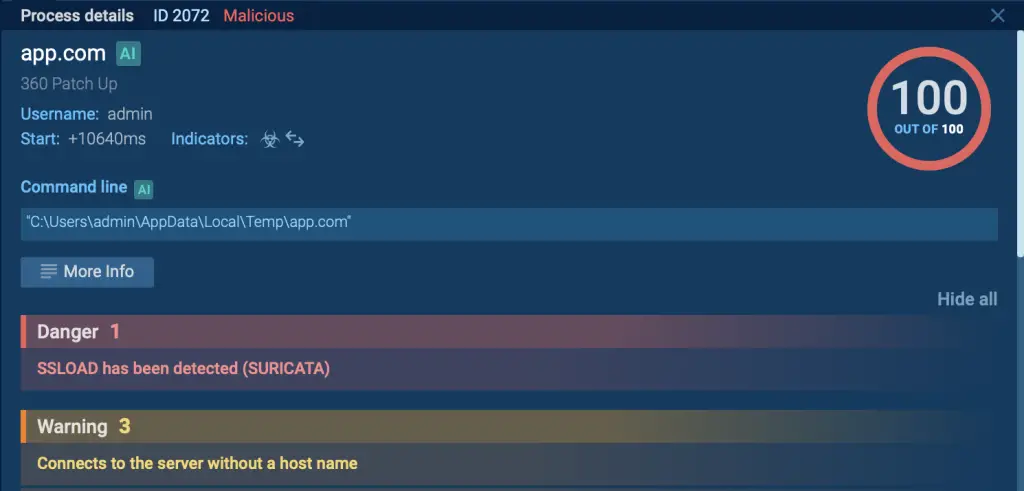
SSLoad malware detection inside ANY.RUN’s sandbox
After the process mentioned above, PhantomLoader starts decrypting and launching SSLoad.
| For more details on how PhantomLoader and SSLoad operate, read the full report on ANY.RUN’s blog. |
First Stage: PhantomLoader
In this analysis session, PhantomLoader disguises itself as “PatchUp.exe,” a legitimate module of 360 Total Security. This tactic is highly effective in avoiding detection by both the system and users. The malicious code runs before the legitimate software’s main function, which means that the module has been altered.
The loader employs XOR decryption to reveal its malicious payload, which is hidden within the legitimate software’s executable file.
The decrypted stub then resolves essential system functions like memory allocation and DLL loading, allowing PhantomLoader to deliver SSLoad into memory.
Second Stage: SSLoad
Once PhantomLoader completes its task, it decrypts and launches SSLoad, a Rust-based loader designed for stealth. SSLoad utilizes multiple evasion techniques to avoid detection.
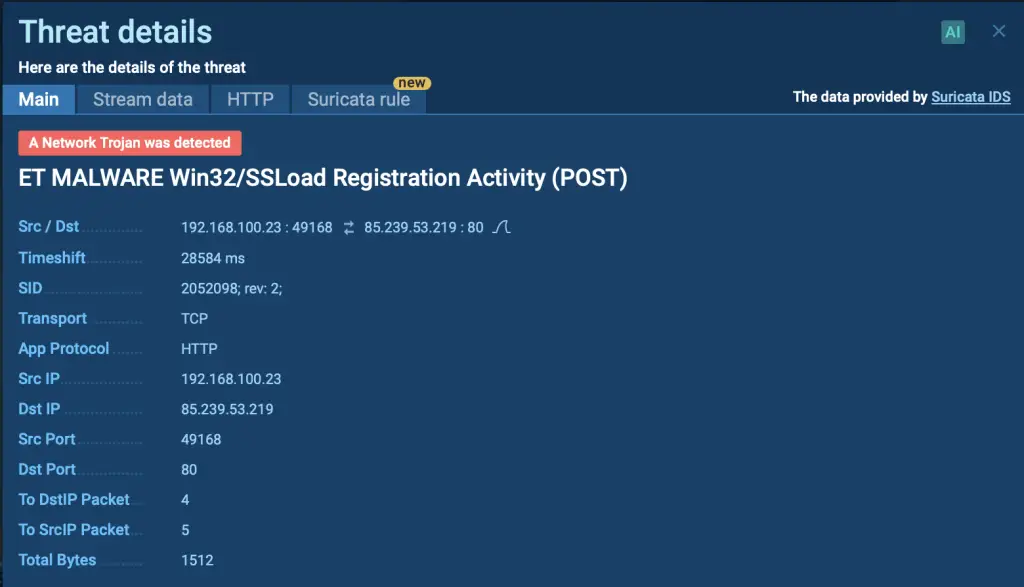
SSLoad malware detected by Suricata rule in ANY.RUN’s sandbox
It begins by decrypting several layers of strings to conceal its operations and uses a mutex object to ensure that only one instance of the malware runs on the infected system, preventing conflicts or reinfection.
SSLoad also gathers key system details, such as the operating system version and architecture, making it easier to adapt to the environment.
To further protect itself, SSLoad employs anti-analysis techniques, including anti-debugging measures that check if it’s being monitored. If debugging is detected, the malware may change its behavior or terminate to avoid analysis.
By using these sophisticated techniques, SSLoad is able to hide its presence and carry out its malicious activities without raising suspicion. This makes themalware detection challenging for traditional security solutions.
MITRE ATT&CK Tactics Employed by Attackers to Deliver SSLoad
In a recent malware analysis conducted by ANY.RUN, several MITRE ATT&CK tactics were identified in an attack involving PhantomLoader and SSLoad.
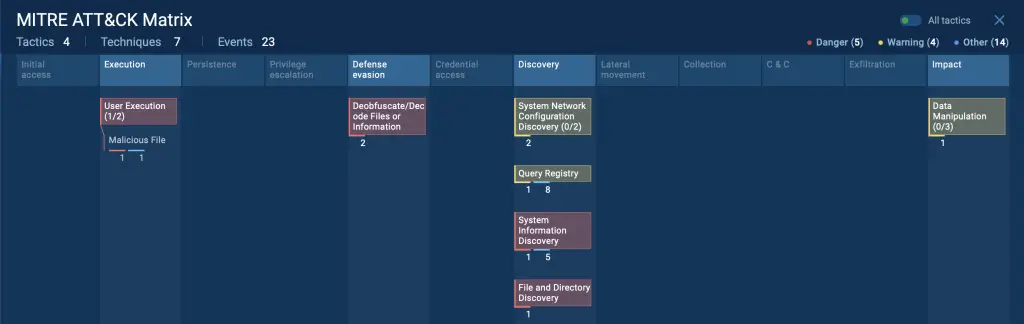
MITRE ATT&CK techniques and tactics used by attackers to deliver SSLoad
- User execution: The infection starts when a victim opens a phishing email containing a malicious Word document. Once opened, it triggers embedded macros that initiate the malware download.
- Deobfuscate/decode files or information: PhantomLoader employs deobfuscation techniques to decode embedded code stubs, which are then used to load SSLoad into memory, allowing it to remain hidden until the final stage of the attack.
- Query registry: SSLoad queries the system registry to gather security and configuration settings.
- System information discovery: SSLoad collects information about the system, including OS version, system architecture, and user details, allowing it to tailor its actions.
- File and directory discovery: PhantomLoader and SSLoad search the system for specific files or directories that can aid in infection or help the malware hide within legitimate processes.
- Data manipulation: SSLoad modifies system data or processes to conceal its presence, disrupt normal functions, and maintain persistence on the infected system.
Start Analyzing Malware with ANY.RUN’s Interactive Sandbox
Curious to see how malware like SSLoad operate? With ANY.RUN’s interactive sandbox, you can safely analyze emerging threats in real time, without risking your systems. Sign up for a 14-day free trial of ANY.RUN’s interactive sandbox to see how it can enhance your organization’s cybersecurity defenses.





