AVrecon RAT hidden in SOHO routers infected 70,000 devices in 20 countries in two years
Recently, telecommunications giant Lumen’s Black Lotus Labs proclaimed in a blog post that it had uncovered a long-standing, globally impacting router malfeasance. The nefarious activity—a novel botnet named “AVrecon”—has been operating inconspicuously for at least two years, compromising 70,000 routers worldwide.
Malicious attacks targeting internet routers are not a novelty; indeed, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) recently issued warnings that malefactors could exploit SOHO routers and similar network devices as global attack infrastructure to gain unfettered access to organizational networks. The infrequency of SOHO router updates exacerbates the severity of this issue.
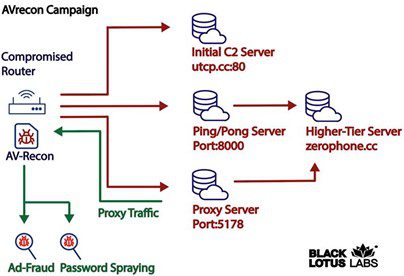
AVrecon campaign | Image Credit: Lumen Black Lotus Labs
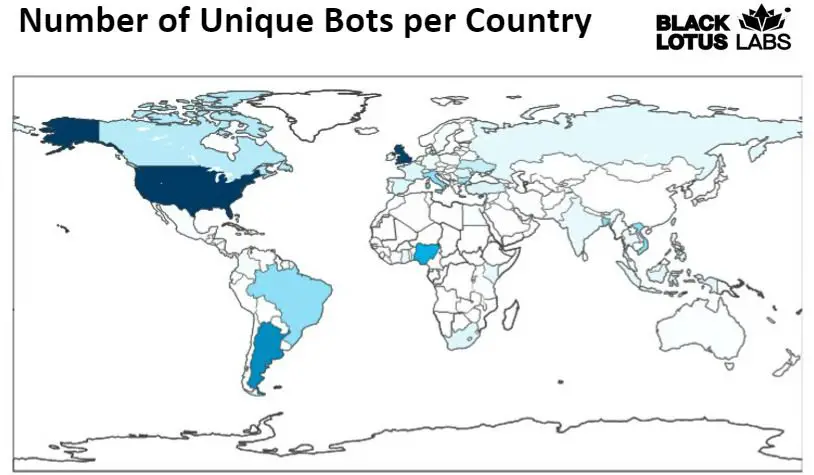
The botnet under investigation by Black Lotus Labs, for instance, has seen its AVrecon malware infect over 70,000 Linux-based routers, maintaining persistent control across more than 40,000 IP addresses in over 20 countries. According to Black Lotus Labs, AVrecon represents the third in a series of malicious software—after ZuroRAT and HiatusRAT—specifically designed to target SOHO routers, with primary targets located in the UK and the US.

Global distribution of the bots | Image Credit: Lumen Black Lotus Labs
Developed in the C programming language, AVrecon targets ARM-embedded devices, especially SOHO (Small Office/Home Office) routers. Black Lotus Labs asserts that these target devices typically lack standard endpoint security solutions, rendering them susceptible to extended attacks exploiting known vulnerabilities.
Once successful in compromising a router, AVrecon transmits information concerning the infected device to an embedded “first stage” Command and Control (C2) server, subsequently instructing the device to connect to a secondary set of C2 servers. Black Lotus Labs researchers uncovered at least 15 such servers in operation since October 2021. Communication between infected routers and the C2 servers is encrypted using x.509 certificates, rendering the success rate of cybercriminals’ “password spraying” attacks invisible to researchers. Moreover, compromised devices are utilized to click on various Facebook and Google ads.
Black Lotus Labs suggests that maintaining good practices, such as regularly rebooting routers and applying security updates, is crucial in countering such malicious activities.





