AWS IAM Roles Anywhere: A Potential Backdoor for Attackers?
In a recent publication, cybersecurity engineer Adan explores a potentially underappreciated security risk in Amazon Web Services (AWS) through the IAM Roles Anywhere feature. Introduced in July 2022, IAM Roles Anywhere was designed to allow external workloads to obtain temporary security credentials in AWS by verifying against an organization’s Certificate Authority (CA) as a trust anchor. While beneficial for flexibility, Adan points out that this configuration can “clearly allow attackers to gain persistence in AWS,” a vulnerability yet to be widely exploited in the wild.
IAM Roles Anywhere enables workloads running outside AWS to assume roles within an AWS account, provided they use X.509 certificates issued by a trusted Certificate Authority. “An attacker with sufficient permissions,” Adan notes, “could exploit IAM Roles Anywhere to gain persistent access to an AWS account.” This persistence could be achieved through the following steps:
- Creating a Malicious CA and Trust Anchor: An attacker generates a CA certificate and registers it in the target AWS account using the CreateTrustAnchor API, establishing a foothold within the account.
- Backdooring an IAM Role: The attacker either creates a new IAM role or modifies an existing one’s trust policy to accept assumptions via the malicious trust anchor.
- Profile Creation: A profile is established in IAM Roles Anywhere, defining which roles can be assumed via the malicious trust anchor.
- Obtaining Temporary Credentials: Using the malicious CA, the attacker signs a client certificate and gains temporary AWS credentials, securing long-term access to the account.
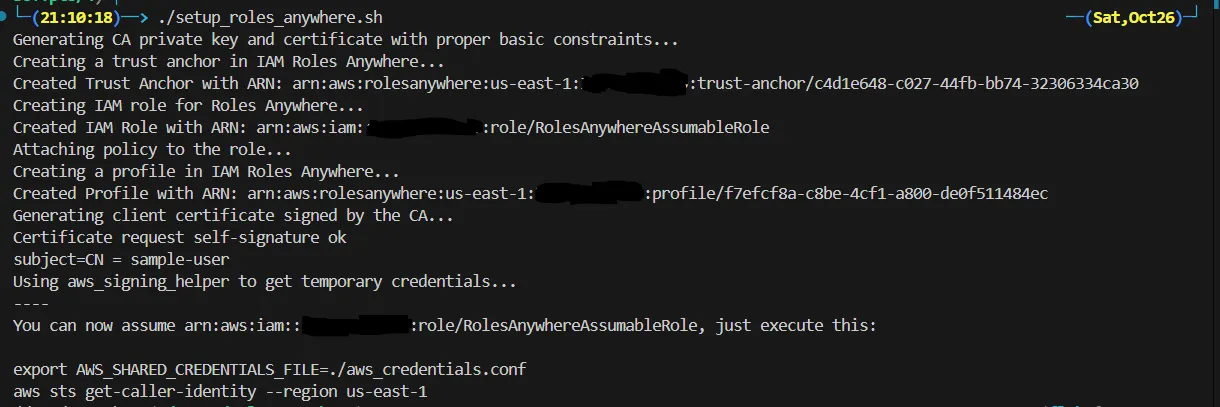
Adan’s research also includes a script, “setup_roles_anywhere.sh,” which automates these steps, underscoring the ease with which persistence could be set up in IAM Roles Anywhere
To defend against this persistence technique, Adan recommends closely monitoring CloudTrail logs for CreateProfile and CreateTrustAnchor events, as “adding new trusts and profiles is probably not a frequent operation,” making it easier to spot anomalies. Limiting permissions for creating or updating trust anchors and profiles is also advised to minimize exposure to this risk.
Related Posts:
- CVE-2024-43047 & CVE-2024-43093: Android Zero-Days Demand Immediate Patching
- Pygmy Goat Malware: A Sophisticated Network Device Backdoor Targets Firewalls
- GOOTLOADER Malware Continues to Evolve: Google Researchers Uncover Advanced Tactics
- Century Systems Routers Vulnerable to Remote Exploitation – CVE-2024-50357 (CVSS 9.8)





