Babylon RAT Unleashed: Malaysian Politicians Under Cyber Siege
A recent investigation by Cyble Research and Intelligence Lab (CRIL) has uncovered a sophisticated cyber espionage campaign targeting high-profile political figures and government officials in Malaysia. The campaign, which has been active since July 2023, employs malicious ISO files designed to deliver the powerful Babylon Remote Access Trojan (RAT), a tool commonly used for covert surveillance and data theft.
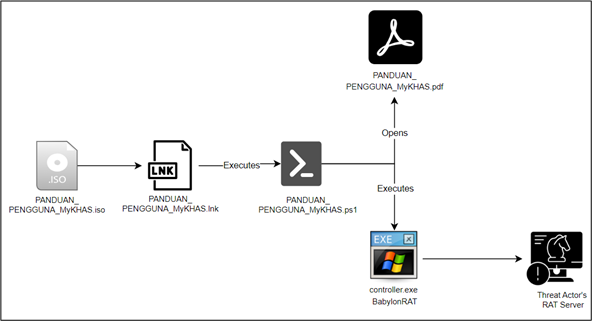
The campaign’s infection method begins with the distribution of ISO files disguised as legitimate documents, tricking recipients into believing they are accessing official or politically sensitive files. Each ISO file contains a shortcut mimicking a PDF document, alongside a hidden malicious executable, a decoy PDF, and a concealed PowerShell script. Once the shortcut is opened, the PowerShell script silently executes in the background, launching the decoy PDF to avoid suspicion while simultaneously copying the malicious executable to the victim’s system.
The script then creates a registry entry to ensure that the malicious executable—identified as “controller.exe”—runs automatically upon system startup, effectively planting the Babylon RAT on the victim’s device.
Babylon RAT is an open-source tool designed for comprehensive surveillance and data exfiltration. Once installed, the RAT gives attackers complete control over the victim’s machine, allowing them to execute commands remotely, capture keystrokes, monitor the clipboard, and steal sensitive data such as passwords. The malware’s persistence mechanisms ensure it survives system reboots by modifying registry settings.
One of the most alarming features of Babylon RAT is its ability to communicate with a command-and-control (C2) server, allowing attackers to remotely manage compromised systems, deliver additional payloads, and harvest critical information. In this campaign, the RAT connects to C2 servers over port 443, facilitating seamless control and data exfiltration.
CRIL’s analysis revealed that the attackers used at least three distinct ISO files, each tailored to specific targets. One file contained a politically charged document, suggesting the campaign is aimed at politically engaged individuals. Another file targeted officials associated with Malaysia’s Majlis Amanah Rakyat (MARA), while a third ISO file, named “PANDUAN_PENGGUNA_MyKHAS.iso,” appeared to target users of the MyKHAS platform, which is widely used by Malaysian government entities.
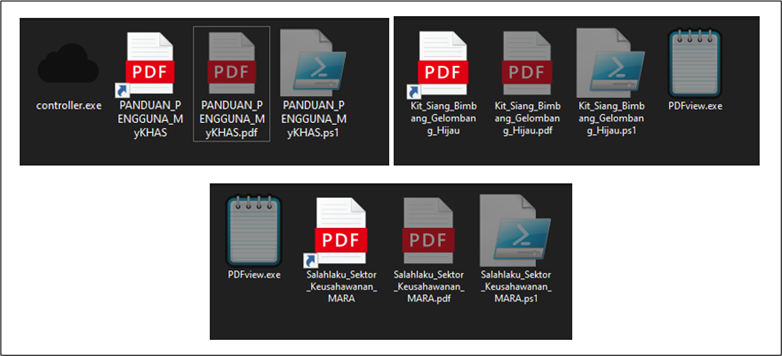
Inside iso file once mounted | Image: CRIL
The campaign’s specific focus on political and governmental figures indicates that the threat actors (TAs) behind the attack are conducting targeted cyber espionage operations, aiming to gather sensitive information from influential individuals within Malaysia.
The attackers behind this campaign demonstrated advanced techniques to ensure their malware goes undetected. The malicious executable, “controller.exe,” contains a large data overlay—approximately 300MB—designed to evade detection by security products. Additionally, the PowerShell script used to execute the malware creates a startup entry in the Windows registry, ensuring the RAT runs persistently across reboots.
Further analysis revealed that the malware employs sophisticated encryption techniques, using the AES-256 algorithm to decrypt its payload. This added layer of obfuscation makes it even more difficult for traditional antivirus solutions to detect the threat.
The Babylon RAT samples observed in this campaign communicate with two known C2 servers—149.28.19[.]207 and 64.176.65[.]152—over encrypted channels. This connection enables the TAs to exfiltrate sensitive data and issue further commands to compromised systems. The attackers’ use of encrypted communication further complicates detection and analysis by cybersecurity tools.
This is not the first time Malaysian entities have been targeted. CRIL’s intelligence suggests that previous campaigns have employed similar tools, such as Quasar RAT, further emphasizing the persistent nature of these attacks. As threat actors continue to evolve their tactics, Malaysian organizations must adopt robust security measures and remain vigilant against these evolving cyber threats.





