Bengal Cat Lovers in Australia Targeted by Gootloader Malware
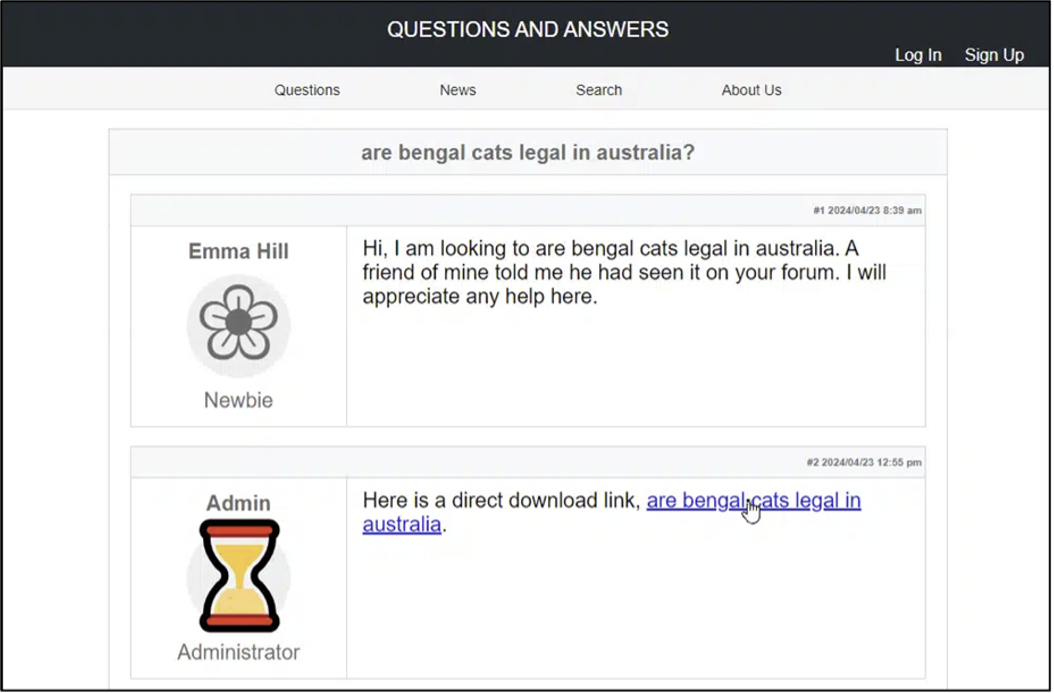
Bengal cat enthusiasts in Australia have become the latest victims of a targeted Gootloader campaign that uses SEO poisoning to spread malware. According to a recent report by Sophos X-Ops, the attackers lured victims through search results related to Bengal cat ownership laws, a popular topic among Australian pet lovers.
The campaign leveraged GootLoader, a malware platform previously associated with the notorious Gootkit banking trojan and REVil ransomware. This platform has now evolved into an “initial access as a service” operation, allowing cybercriminals to plant various forms of malware, including post-exploitation tools and ransomware. As Sophos explained, “GootLoader is known for using search engine optimization (SEO) poisoning for its initial access.” Through strategic SEO, the attackers manipulated search engine rankings to push malicious sites related to Bengal cat laws in Australia. When users clicked these results, they were redirected to a compromised website and prompted to download a ZIP file disguised as relevant information, containing a JavaScript file that would execute malicious commands on their device.
The downloaded file initiates a multi-stage infection process. The initial JavaScript file executed by GootLoader drops a larger, heavily obfuscated JavaScript payload, which the attackers use to create a scheduled task—subtly named “Business Aviation”—to maintain persistence on the victim’s device. This scheduled task runs a script through Windows Script Host (wscript.exe), ensuring the malware can continue its operations in the background. This mechanism is essential to the GootLoader infection chain, enabling further payloads to download undetected.
During the investigation, Sophos X-Ops threat hunters identified several malicious domains to which the infected systems connected. They observed PowerShell commands sending Base64-encoded cookies containing directory and user information, allowing the attackers to gain insights into the victim’s environment. These domains have since been classified as malware callhome destinations, indicative of their role in maintaining ongoing contact with the compromised devices.
This campaign highlights a disturbing trend in the malware landscape: the ongoing exploitation of SEO poisoning as a vector for initial access. By targeting niche interests like pet ownership regulations, GootLoader demonstrates how highly specific content can be weaponized to reach unsuspecting audiences. As Sophos noted, “GootLoader is one of a number of continuing malware-delivery-as-a-service operations that heavily leverage search results as a means to reach victims.”
Related Posts:
- Indian Government Portal Exposes Residents’ Aadhaar Details and Fingerprints
- Unit 42 Research Exposes GootLoader’s Sophisticated Sandbox Evasion Tactics
- GOOTLOADER Malware Continues to Evolve: Google Researchers Uncover Advanced Tactics
- Over 300,000 citizen data may be abused, Australia investigates Facebook





