Beware of chalk-node: Malicious Package Steals Developer Data
A new threat lurking in the npm repository is exploiting the common typosquatting technique to trick developers into installing malware designed to siphon off sensitive data.
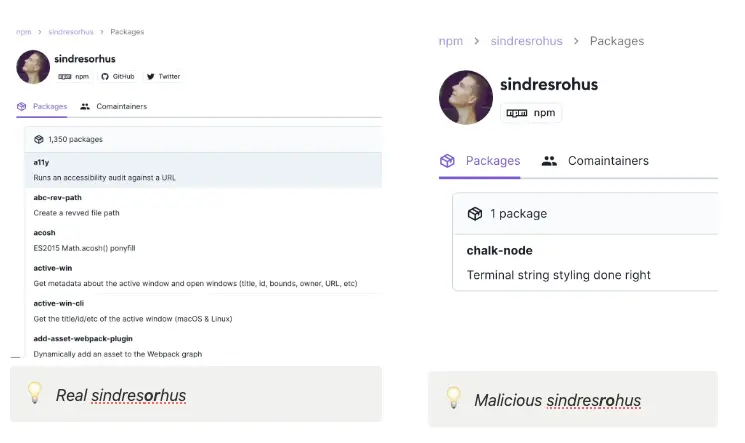
Security researchers at Socket have uncovered a malicious package named “chalk-node,” masquerading as the popular “chalk” library used for terminal text styling. The perpetrator, using the subtly misspelled “sindresrohus” username (a play on the legitimate developer Sindre Sorhus’s “sindresorhus” username), crafted this counterfeit package to deceive unsuspecting developers.
This “chalk-node” package is a malicious code. Hidden within its code is a malicious script that reads files from the victim’s computer and transmits them to external servers via the Sentry service. The malware cleverly replaces the standard “console.log” function with a modified version that can extract sensitive data whenever it’s called.
The malicious code leverages Node.js’s fs module functions (readFileSync and readdirSync) to locate and pilfer sensitive files, including authentication credentials and configuration data. While the package has been downloaded over 600 times – a small number compared to the authentic “chalk” package’s massive user base – it poses a significant risk, particularly to less experienced developers who may be more susceptible to typosquatting attacks.
Socket has reported the malicious package to npm and recommended its immediate removal. However, as of this writing, “chalk-node” remains available on the platform.
To protect themselves, developers are strongly urged to:
- Scrutinize package names: Pay close attention to spelling and verify the authenticity of packages before installation.
- Utilize security tools: Employ security analysis tools that can detect suspicious code and prevent supply chain attacks.
- Install a CLI tool: Consider using a CLI tool like Socket’s, which provides an extra layer of defense against malicious npm dependencies.