Beware! TA450 Back with Salary Scam Emails
Cybersecurity researchers at Proofpoint have uncovered a new wave of targeted phishing attacks attributed to the Iran-aligned hacking group TA450. This campaign marks a shift in tactics for the group, with attackers now employing salary-related lures and compromised Israeli email accounts to target employees of multinational corporations in the manufacturing, technology, and information security sectors.
Phishing With a Payday Twist

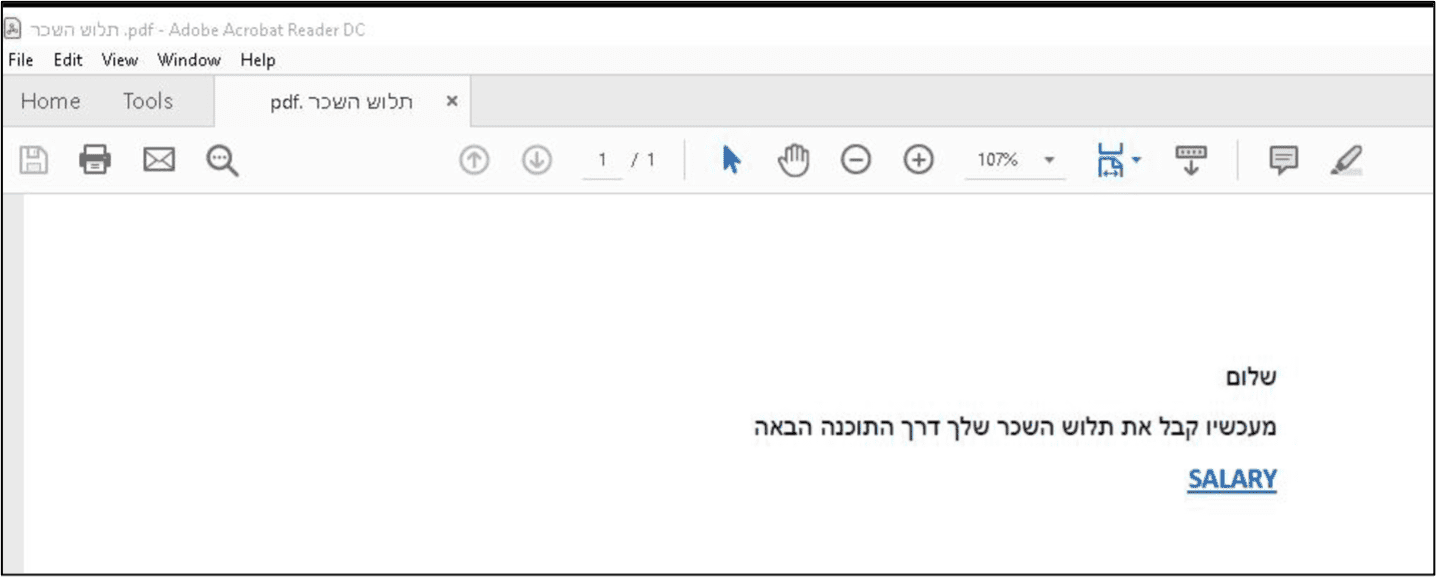
Opened PDF attachment with malicious link | Image: Proofpoint
The attacks, observed throughout March 2024, involve emails containing PDF attachments with malicious links disguised as salary information. This marks a departure from TA450’s recent preference for directly embedding malicious links in email bodies. Upon clicking the link, victims are led to file-sharing sites where they unwittingly download a ZIP archive containing malware.
The malware installs AteraAgent, legitimate remote administration software known to be abused by the TA450 hacking group. This enables the attackers to potentially gain control over the victim’s computer, exfiltrate sensitive data, or deploy additional malware.
Heightened Risk for Israeli Targets
TA450’s continued focus on Israeli individuals is a cause for concern, particularly in light of heightened regional tensions. The group has a history of targeting Israeli entities, with attacks intensifying since October 2023 alongside the Israel-Hamas conflict.
This campaign highlights the evolving nature of cyber threats and the lengths that adversaries will go to to infiltrate their targets. Organizations with ties to Israel, particularly in the technology and manufacturing sectors, need to be on high alert.
Protecting Against Targeted Attacks
- User Awareness: Educate employees about the dangers of phishing attacks, especially those with social engineering lures that play on current events or anxieties.
- Robust Email Security: Implement email filtering solutions that can detect and block suspicious emails and attachments.
- Endpoint Protection: Install up-to-date antivirus and anti-malware software on all company devices.
- Threat Intelligence: Stay informed about the latest tactics and techniques of threat actors like TA450 to proactively adjust your defenses.
Attribution and Implications
Proofpoint attributes this campaign to TA450 with high confidence, citing overlaps in techniques, targeting patterns, and malware used. This aligns with the U.S. Cyber Command‘s attribution of the group to Iran’s Ministry of Intelligence and Security, further highlighting the geopolitical dimensions of cyberwarfare.




