Beware the Bite of Mamba 2FA: This Phishing Kit Bypasses 2FA
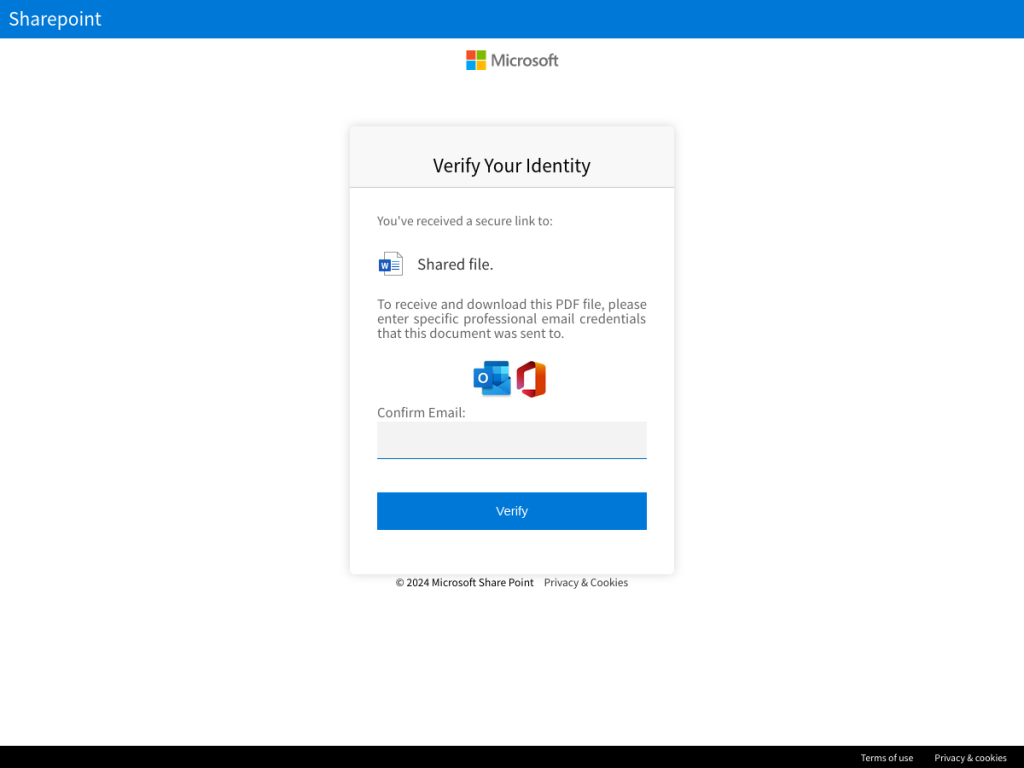
In the rapidly evolving world of phishing, a new player has emerged—Mamba 2FA. In late May 2024, Sekoia’s Threat Detection & Research (TDR) team uncovered this adversary-in-the-middle (AiTM) phishing kit, which specifically targets multi-factor authentication (MFA) systems. Mamba 2FA has quickly gained traction in the phishing-as-a-service (PhaaS) marketplace, making it easier for attackers to bypass non-phishing-resistant MFA methods such as one-time codes and app notifications.
First identified during a phishing campaign mimicking Microsoft 365 login pages, Mamba 2FA operates by relaying MFA credentials through phishing pages using the Socket.IO JavaScript library to communicate with a backend server. “At first, these characteristics looked like the Tycoon 2FA phishing-as-a-service platform, but further inspection found that the campaign leveraged a previously unknown AiTM phishing kit that Sekoia tracks as Mamba 2FA,” stated Sekoia’s report.
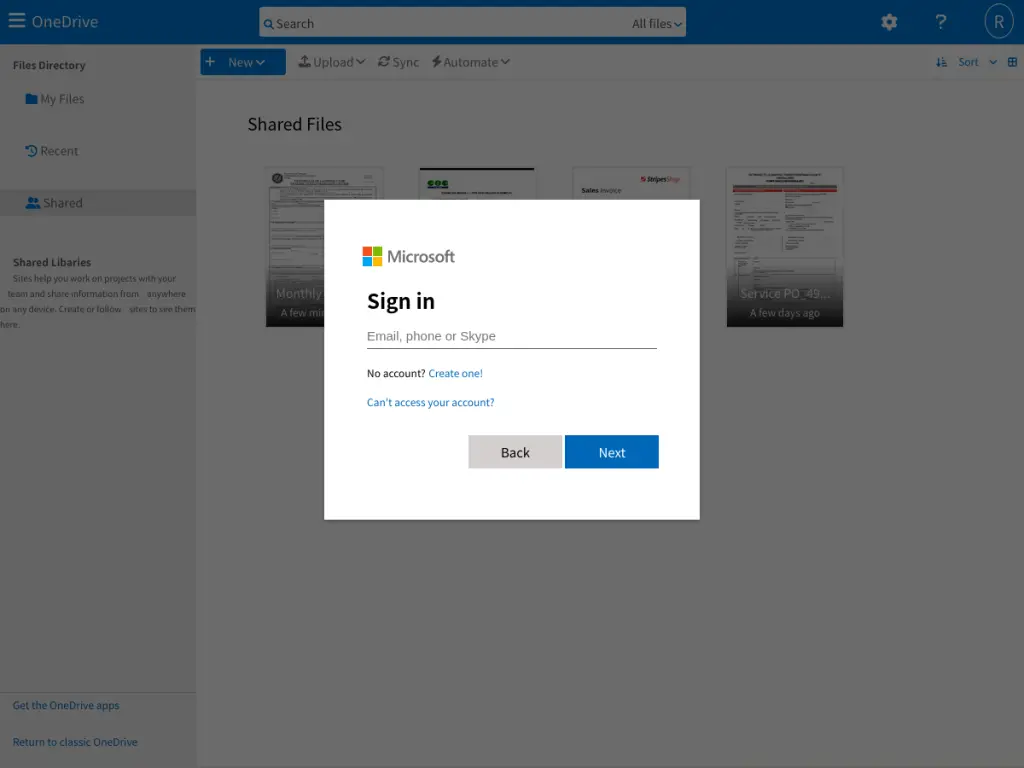
Phishing page variants of Mamba 2FA. | Image: Sekoia’s
Mamba 2FA’s infrastructure has been seen targeting Entra ID, third-party single sign-on providers, and consumer Microsoft accounts. The stolen credentials are sent directly to attackers via Telegram, providing them with near-instant access to compromised accounts.
One of the defining features of Mamba 2FA is its ability to dynamically adapt to its targets. For example, in enterprise accounts, the phishing page can reflect an organization’s custom branding, including logos and background images, making the attacks even more convincing. “For enterprise accounts, it dynamically reflects the organization’s custom login page branding,” the report revealed.
Mamba 2FA’s capabilities extend beyond basic MFA interception. The platform handles various MFA methods and updates the phishing page based on user actions. This adaptability makes it an attractive tool for cybercriminals seeking to exploit even the most sophisticated MFA implementations.
Mamba 2FA is available on Telegram for $250 per month, making it accessible to a wide array of attackers. Customers can generate phishing links and HTML attachments on demand, and the infrastructure is shared among several users. The kit has been actively advertised since March 2024, and its continued evolution signals an ongoing threat.
Sekoia’s research highlighted the kit’s rapid development: “The phishing kit and associated infrastructure have undergone several significant changes.” With its relay servers hosted on commercial proxy services, Mamba 2FA ensures that its real infrastructure remains hidden, reducing the risk of detection.
Related Posts:
- PyPI’s New Rule: 2FA Verification for All Project Maintainers
- Tycoon 2FA: The Evolving Threat Bypassing Multi-Factor Authentication
- France Leads International Effort to Eradicate PlugX Trojan from 3,000 Systems
- Phishing Campaign Bypasses MFA to Target Meta Business Accounts, Putting Millions at Risk





