Bifrost Malware: Linux Beware! New Variant Leverages Deceptive Domain for Evasion
The cybersecurity landscape is constantly shifting, and a new, more insidious Linux variant of the Bifrost RAT has emerged, underscoring the importance of heightened vigilance. Discovered by Palo Alto Networks’ Unit 42 Incident Response team, this strain employs cunning tactics to undermine security measures and stealthily infiltrate vulnerable systems.
The Danger of Typosquatting
First unearthed in 2004, Bifrost is not new to the scene of cyber espionage. This remote access Trojan (RAT) has been notoriously utilized by attackers to infiltrate systems, gathering critical information such as hostnames and IP addresses, which are gateways to further exploitation.

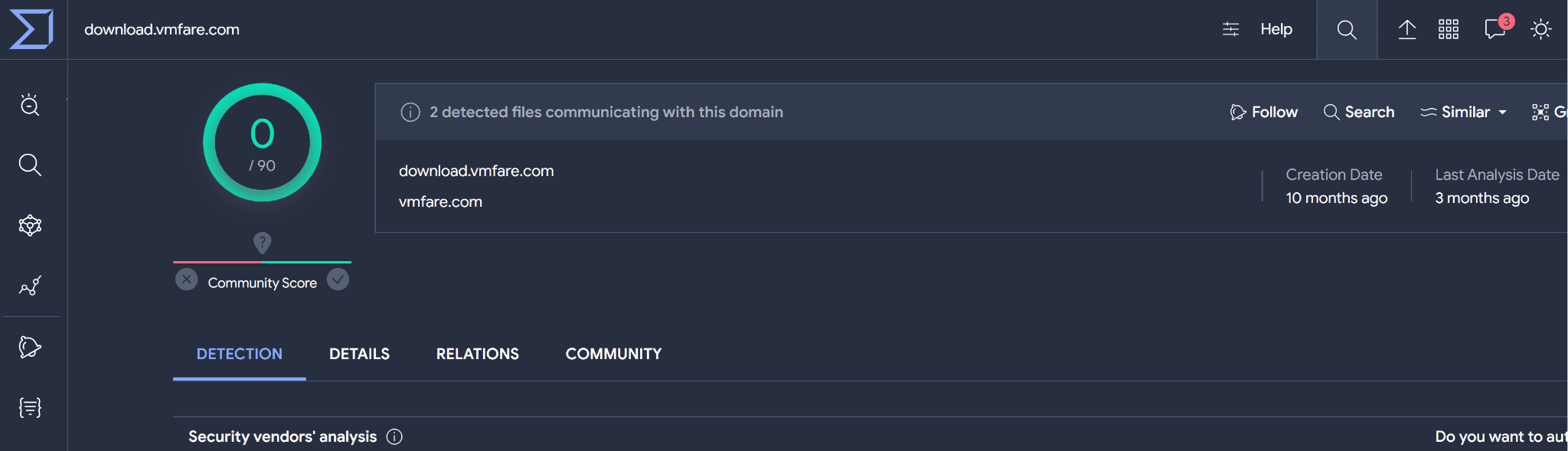
VirusTotal score for download.vmfare[.]com. | Image: Unit 42
At the heart of this variant’s evasive nature lies a deceptive command and control (C2) domain – download.vmfare[.]com. This domain is strategically designed to mimic the legitimate VMware website, a practice known as typosquatting. The attackers’ goal is simple: trick unsuspecting users into trusting the malicious domain, hoping they’ll overlook minor spelling discrepancies in their haste or inattention.
By successfully deceiving victims and filtering malicious traffic through this seemingly legitimate domain, Bifrost’s operators hope to significantly enhance their chances of flying under the radar of traditional security defenses.
Behind the Scenes: How Bifrost Operates
Let’s delve into how this Linux variant of Bifrost functions:
- Obfuscation Techniques: The attackers have stripped the malware binary of its debugging information and symbol tables. Think of this as removing the blueprints that security researchers would normally use to analyze the malware’s structure and logic. This deliberate obfuscation makes reverse engineering and tracing the malware’s origins more challenging.
- Information Gathering: Once Bifrost infects a system, it embarks on a reconnaissance mission. It stealthily gathers sensitive details such as the machine’s hostname and IP address. This initial data harvesting enables attackers to customize their attack techniques for maximum impact.
- Encryption in Transit: To further protect its operations, Bifrost encrypts the stolen data before sending it back to its C2 server. It employs the RC4 encryption algorithm, which acts like a digital lockbox, shielding the contents from prying eyes during transmission. This makes it much more difficult for defenders to monitor the network and decipher the stolen information.
- Targeting ARM Systems: A particularly concerning aspect of this Bifrost variant is the inclusion of an ARM-based version. ARM architecture is dominant in mobile devices, embedded systems, and the burgeoning world of IoT. This development indicates that attackers are expanding the malware’s potential attack surface, seeking to exploit the wide range of devices that sometimes lack the same robust security as traditional laptops and desktops.
The Bifrost Threat Escalates

Advanced WildFire report of Bifrost sample detections from October through January 2024. | Image: Unit 42
The threat landscape is dynamic, as evidenced by Palo Alto Networks’ observations of a recent spike in Bifrost-related activity. Over the past few months, they have detected an alarming increase in the number of distinct malware samples, clearly demonstrating that Bifrost remains a favored tool amongst cybercriminals.
A Word of Caution
The Linux landscape is increasingly becoming a preferred target for cybercriminals. Organizations and individuals alike need to take proactive measures to safeguard their networks from the advanced capabilities of modern malware like Bifrost.





