Bitdefender Releases Decryptor for ShrinkLocker Ransomware
In a world where ransomware has evolved to use complex encryption algorithms, ShrinkLocker—a newly discovered ransomware variant—takes a retro approach. Martin Zugec, a security researcher at Bitdefender, recently analyzed ShrinkLocker and found that it combines “old-school” scripting with a unique twist: it uses Microsoft’s own BitLocker encryption to lock down systems. Discovered in May 2024, ShrinkLocker’s approach is surprising yet effective, leveraging VBScript and Windows features rather than advanced cryptographic methods.
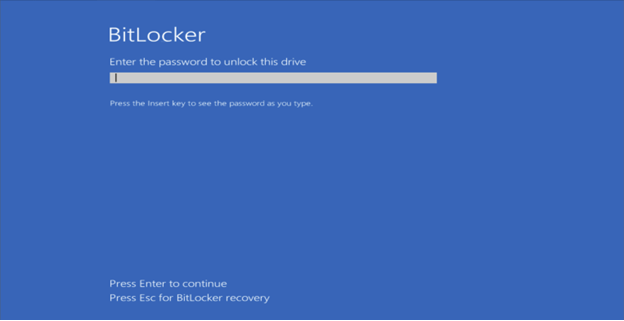
ShrinkLocker’s method is simple but potent. The ransomware starts by checking if BitLocker is installed. If not, it installs and configures it, then proceeds to re-encrypt the system’s drives using a randomly generated password, which is uploaded to a server controlled by the attacker. Upon reboot, the infected system displays a prompt for a BitLocker password, with the attacker’s contact details on the screen, leaving victims with a simple choice: pay the ransom or lose access.
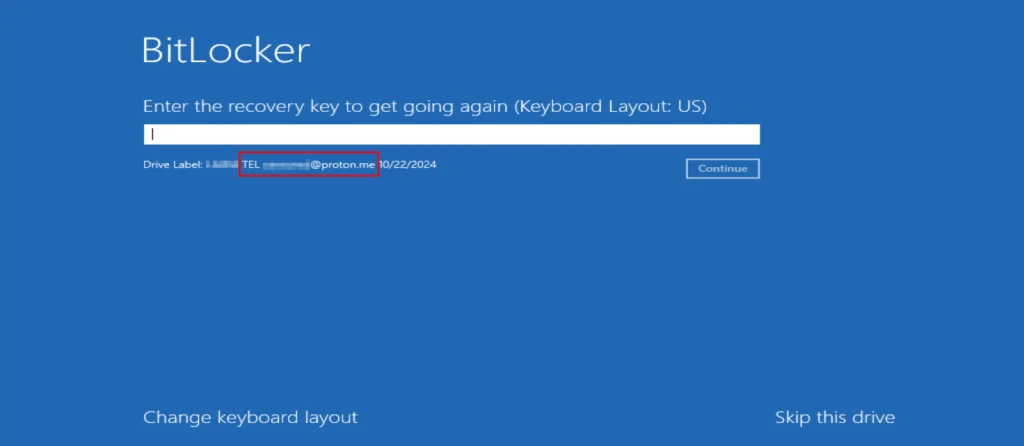
Image: Bitdefender
“By using a combination of Group Policy Objects (GPOs) and scheduled tasks, [ShrinkLocker] can encrypt multiple systems within a network in as little as 10 minutes per device,” Zugec notes. This quick spread is especially dangerous in corporate environments, where ransomware can compromise entire domains with minimal effort.
In his analysis, Zugec reveals that ShrinkLocker’s code may have roots going back over a decade. The ransomware was likely adapted from older, benign code, creating a “digital time capsule repurposed for malicious intent.” Some features, such as the use of VBScript, date back to an era when VBScript was common in Windows environments. Now, however, Microsoft has scheduled VBScript for deprecation starting with Windows 11 H2 2024.
Unlike many ransomware strains, which are sold as part of Ransomware-as-a-Service (RaaS) ecosystems, ShrinkLocker is accessible to individual actors. The simplicity of ShrinkLocker’s design, coupled with its effectiveness, makes it an appealing option for lone attackers or smaller cybercriminal groups.
ShrinkLocker poses a substantial risk for supply chains as well. In one case involving a healthcare company in the Middle East, the attack started on an unmanaged system and moved laterally through the network. “Approximately 70% of incidents investigated by our MDR team have begun on unmanaged devices,” Zugec shares, underlining the critical need for tighter supply chain security and management of connected devices.
Bitdefender has developed and released a decryptor for ShrinkLocker, providing a temporary solution. This tool, available on Bitdefender’s website, enables users to recover their data but is reactive, relying on the immediate detection of the ransomware to work effectively. Bitdefender warns that “decryptor tools are inherently reactive,” and while helpful, they don’t prevent attackers from attempting similar attacks in the future.
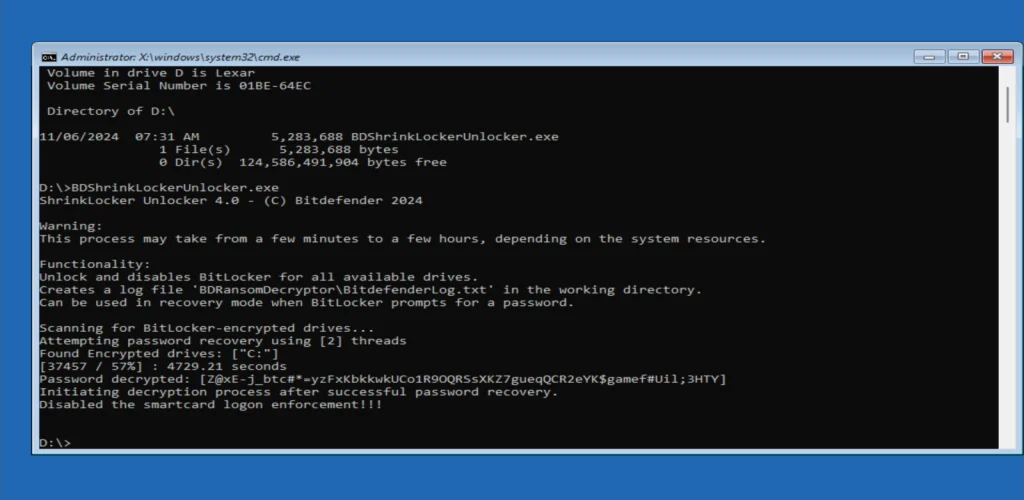
Image: Bitdefender
To strengthen defenses, Bitdefender recommends that organizations implement proactive monitoring and BitLocker configurations that require recovery keys to be stored in Active Directory Domain Services (AD DS). This policy “ensures that BitLocker encryption cannot be started unless the necessary recovery information is securely stored in Active Directory,” providing an additional layer of defense against ShrinkLocker.





