Bluetooth Eavesdropping Threat Exposed: New “BlueSpy” Exploit Targets Popular Headsets
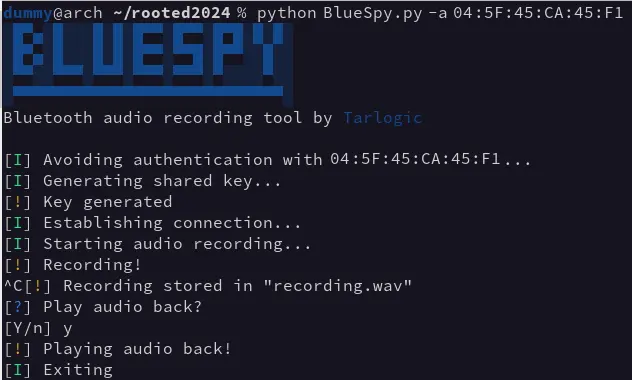
A cybersecurity research team has shaken the Bluetooth world at the RootedCon Madrid 2024 conference. Tarlogic Security unveiled “BlueSpy,” a proof-of-concept exploit that demonstrates how popular Bluetooth headsets can be silently turned into eavesdropping devices, exposing private conversations to potential hackers.
The BlueSpy exploit highlights how the widespread use of insecure pairing methods in consumer Bluetooth headsets poses a significant privacy risk. Using Linux and a readily available Python script, researchers showed how attackers could gain unauthorized access to headsets, silently activate their microphones, and record conversations without the victim’s knowledge.
How Does BlueSpy Work?

BlueSpy targets a common vulnerability in Bluetooth headsets that use the “JustWorks” pairing mechanism. Unlike more secure pairing methods, which require the user to enter a PIN for authentication, JustWorks offers little protection, allowing attackers in the vicinity to seamlessly connect to a vulnerable headset.
The exploit also relies on headsets that remain in discoverable mode and use easily identifiable MAC addresses.
The Need for Stronger Bluetooth Security
Tarlogic’s research, including the development of a comprehensive Bluetooth Security Assessment Methodology (BSAM), underscores the need for manufacturers to rethink Bluetooth security. The researchers have emphasized:
- The importance of secure pairing mechanisms: Manufacturers should encourage users to disable automatic pairing or at least require manual approval for each new device connection.
- User control over discoverability: Devices should have easily accessible controls to toggle discoverability mode, reducing the window for potential exploitation.
What Can Bluetooth Headset Users Do?
While waiting for more secure Bluetooth devices, users should take precautions:
- Be choosy: Select headsets that offer secure pairing options by default.
- Stay vigilant: Don’t leave your headset in discoverable mode when not in use. Store it in its charging case when possible.
- Practice skepticism: Be wary of unexpected Bluetooth pairing requests.
Industry Must Step Up
“Bluetooth technology offers a simple form of communication for low-power devices, but many manufacturers have prioritized ease and convenience of use by users/customers over security,” says Jesús María Gómez Moreno, a researcher at Tarlogic Security. “Within companies, to maintain a complete and beneficial security policy, risk calculation must take into account all devices and systems connected to the infrastructure. Until now, risk calculation has focused mainly on devices connected by cable or WiFi, but research and tools such as BlueSpy show that it is essential to consider technologies such as Bluetooth as well.”
Tarlogic encourages Bluetooth device manufacturers to employ a rigorous security assessment methodology like BSAM to identify potential vulnerabilities and bolster their products against exploits like BlueSpy.





