bodhi: Client-Side Vulnerability Playground
Bodhi – Client-Side Vulnerability Playground
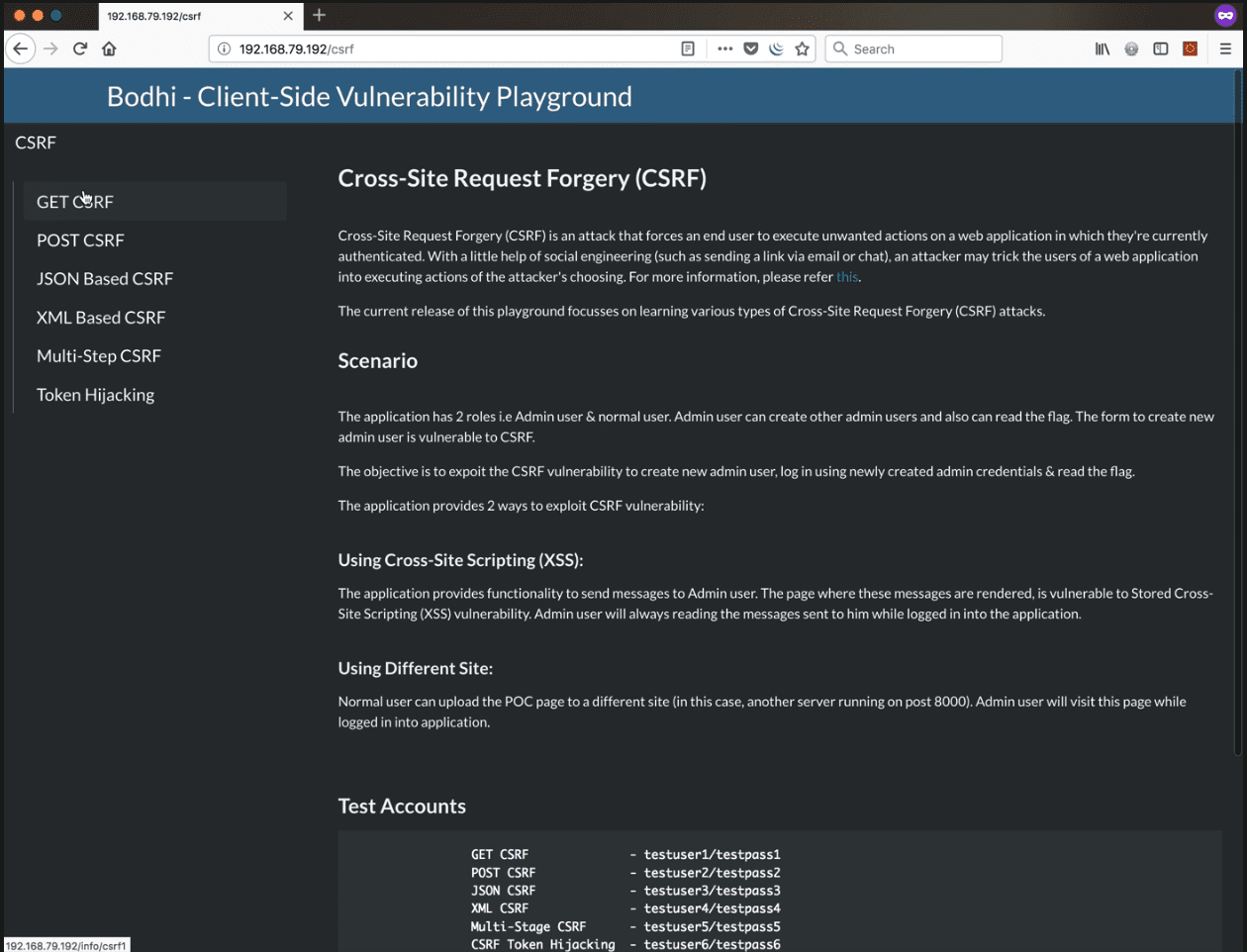
Bodhi is a playground focused on learning the exploitation of client-side web vulnerabilities. The playground has a vulnerable application & a bot program which simulates the real-world victim. An attacker will have knowledge of the vulnerability and will send crafted payload which will be accessed by the victim. The attacker needs to complete objective by exploiting these vulnerabilities.
The playground is a CTF style application where the objective is to read the flag available for each vulnerability. Main vulnerability page has detailed information about scenarios & test accounts to be used.
Setup Instructions
-
Docker
There is a docker available for this. Follow below commands to set it up:
$ docker pull amolnaik4/bodhi_app
$ docker run -p 80:80 -p 8000:8000 amolnaik4/bodhi_appOnce docker is running, access the application at http://<your_machine_ip>
-
Using Code
Browse to http://<your_machine_ip>
Demo
Author: @amolnaik4
Source: https://github.com/amolnaik4/




