Broken Promises: E2EE Cloud Storage Vulnerabilities Exposed
In a world where data privacy is a growing concern, end-to-end encryption (E2EE) cloud storage systems promise to keep your information secure, even from the very providers managing the storage. But as a recent report from Jonas Hofmann and Kien Tuong Truong from ETH Zurich reveals, this promise is often broken. Their analysis of five major E2EE cloud storage providers—Sync, pCloud, Icedrive, Seafile, and Tresorit—uncovers critical vulnerabilities, exposing users to risks far beyond what they may expect.
E2EE cloud storage ensures that even if the storage provider’s servers are compromised, your data remains secure, encrypted by keys only you, the user, control. Major providers like Sync and pCloud claim to offer such “zero-knowledge encryption,” meaning that they theoretically can’t access your data. However, Hofmann and Truong’s research paints a different picture, showing that these systems can be easily broken.
As Hofmann points out, “many of our attacks affect multiple providers in the same way, revealing common failure patterns in independent cryptographic designs“. These vulnerabilities allow attackers to inject files, tamper with data, and even gain access to encrypted content.
Hofmann and Truong’s study focuses on what happens when the provider’s server is compromised, analyzing whether the cryptographic systems in place can still protect users. For four out of the five systems, the results are alarming:
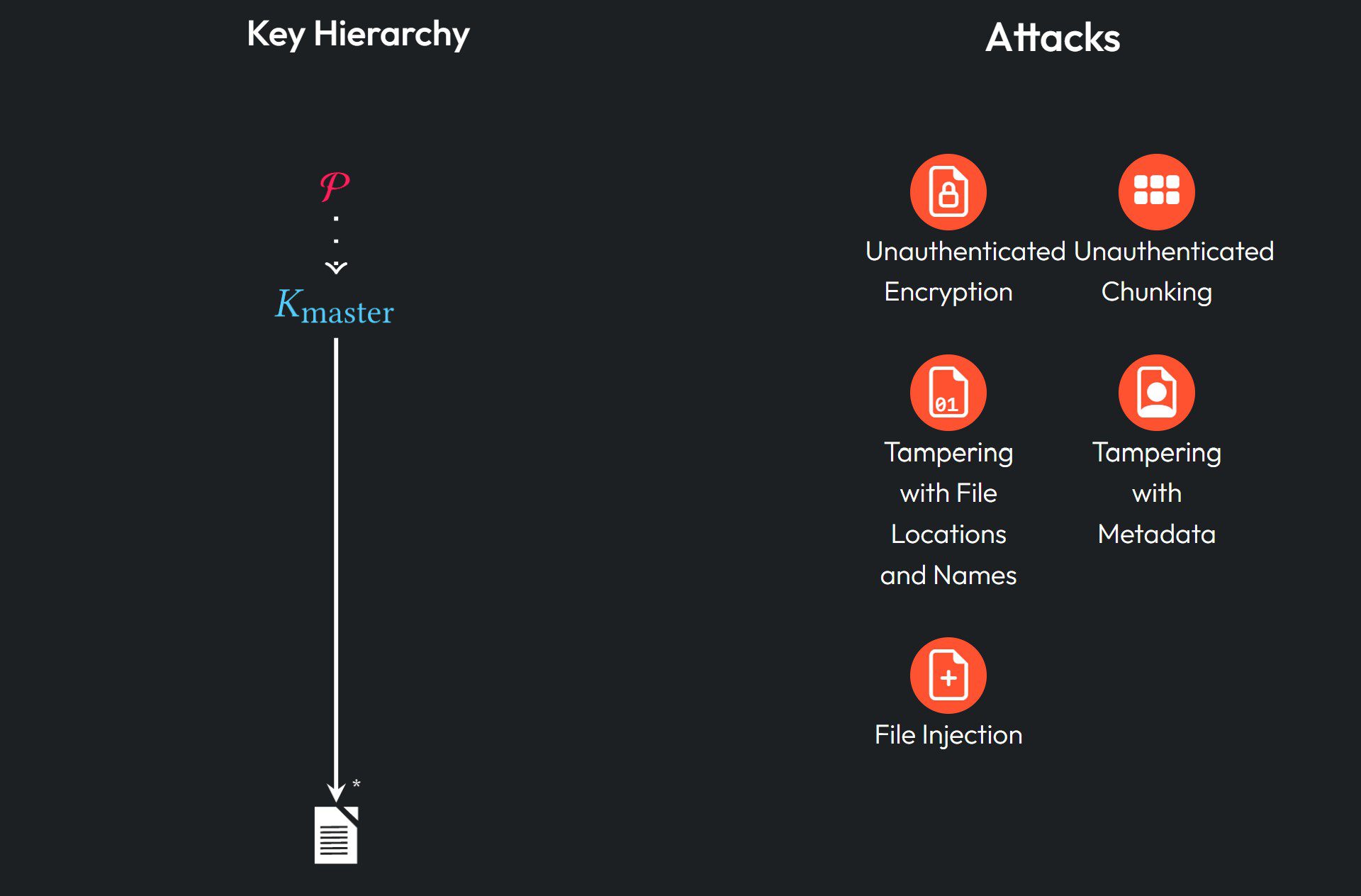
- Lack of Key Authentication: In Sync and pCloud, the researchers discovered that attackers could inject rogue keys into the system, tricking users into encrypting their data with attacker-controlled keys. This essentially allows the attacker to decrypt any future uploads.
- Protocol Downgrade: Seafile suffers from a protocol downgrade vulnerability. This allows attackers to weaken the encryption used, enabling brute-force attacks on user passwords.
- File Injection Attacks: In pCloud and Sync, the server can inject malicious files into a user’s storage, making it appear as though the user uploaded them. This poses a significant risk, especially in scenarios involving sensitive or incriminating files.
- Unauthenticated Encryption: In Icedrive and Seafile, files are encrypted using modes that do not ensure data integrity. This means an attacker can tamper with files without the user knowing.
While encryption can hide the content of files, Hofmann and Truong also highlight the importance of metadata, which includes file names, sizes, and directory structures. The report emphasizes, “metadata such as the file name can disclose much about the file itself“. None of the analyzed providers offer sufficient protection against metadata tampering or leakage, leaving users vulnerable to attacks that manipulate or expose file locations and names.
What’s even more concerning is how easy it is for attackers to exploit these flaws. As the researchers note, “our attacks are highly practical and can be carried out without significant resources“. In many cases, attackers do not need advanced cryptographic skills to break these systems. Instead, they can rely on the systems’ inherent design flaws to gain access to sensitive data.
End-to-end encrypted cloud storage systems promise to keep your data safe from prying eyes, but as this research reveals, these promises often fall short. The vulnerabilities uncovered in Sync, pCloud, Icedrive, Seafile, and Tresorit highlight fundamental flaws in the current state of E2EE cloud storage. As the report concludes, “cryptographic shortcomings are not limited to a few providers but are, instead, widespread in the broader ecosystem“. Users and organizations relying on these systems should remain cautious and advocate for stronger security measures before entrusting sensitive data to the cloud.
Update on October 30:
A statement from Peter Budai, CTO, Tresorit:
“The study of ETH Zürich’s world-class research team examined the possibility of ten classes of attacks on end-to-end-encrypted cloud storage systems, including confidentiality breaches and file injection vulnerabilities. The findings confirmed that Tresorit’s thoughtful design and cryptographic choices made our system largely unaffected by these attacks. While we are pleased with these results, we also recognize the untapped potential the research highlighted.
Presenting public key fingerprints to users when sharing folders is on our 2025 roadmap. This will completely prevent key replacement attacks by allowing out-of-band verification. We already do this for business invitations so the user can get cryptographic evidence about their future data administrator before joining. Our Common Criteria EAL4 + AVA_VAN.5 evaluated client software — a first among cloud storage services — requires out-of-band key authentication for folder sharing, too.
Even though some metadata, such as the file size, the time of last modification, and folder memberships are shared with the servers, these are also stored as cryptographically authenticated data to prevent tampering. This metadata is also needed to be known on the server side: for the proper bookkeeping of our customers’ storage quota, and to enforce server-side access rules as an additional layer of security.
At Tresorit, security is our top priority, and we are committed to continuous improvement, using these insights to strengthen our platform further. This research not only helps us evolve but also guides the broader industry toward more secure solutions. Security is the foundation of everything we build, and we are proud to collaborate with academic institutions like the Technical University in Budapest to ensure that we stay at the forefront of innovation in secure cloud storage.”