bucket stream: Find interesting Amazon S3 Buckets
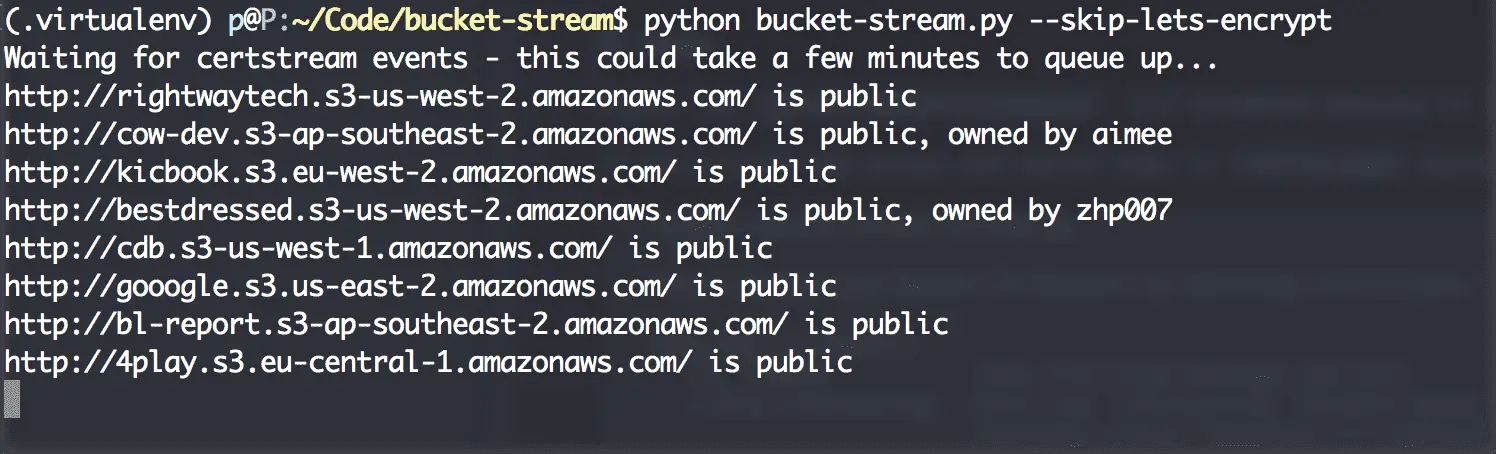
Bucket Stream
Find interesting Amazon S3 Buckets by watching certificate transparency logs.
This tool simply listens to various certificate transparency logs (via certstream) and attempts to find public S3 buckets from permutations of the certificates domain name.
Be responsible. I mainly created this tool to highlight the risks associated with public S3 buckets and to put a different spin on the usual dictionary-based attacks. Some quick tips if you use S3 buckets:
- Randomise your bucket names! There is no need to use company-backup.s3.amazonaws.com.
- Set appropriate permissions and audit regularly. If possible create two buckets – one for your public assets and another for private data.
- Be mindful of your data. What are the suppliers, contractors, and third parties doing with it? Where and how is it stored? These basic questions should be addressed in every infosec policy.
Installation
Python 3.4+ and pip3 are required. Then just:
- git clone https://github.com/eth0izzle/bucket-stream.git
- (optional) Create a virtualenv with pip3 install virtualenv && virtualenv .virtualenv && source .virtualenv/bin/activate
- pip3 install -r requirements.txt
- python3 bucket-stream.py
Usage
Simply run python3 bucket-stream.py.
If you provide AWS access and secret keys in config.yaml Bucket Stream will attempt to identify the buckets owner.
Copyright (c) 2017 eth0izzle





