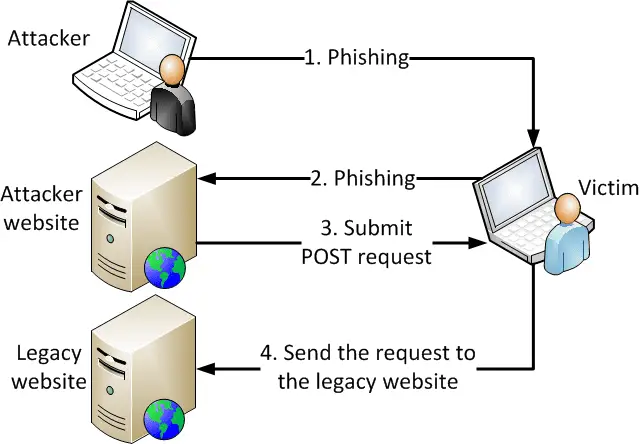
Understanding CSRF The Express team’s csrf and csurf modules frequently have issues popping up concerned about our usage of cryptographic functions....
Technique
Since May this year, WannaCry extortion software in the global outbreak, there have been Equifax experienced large-scale...
On this post, I am going to guide you how to install & upload your Kali Linux...
What is WebRTC? In the conventional video communication, people often need to use a third-party server as...
Install & Enable HTTPS on Apache Server First of all, you need to have a website that...
Browser Local Storage Overview Introduction cookie A cookie is a data (usually encrypted) that some websites store...
In our infiltration process, we usually need to send some files to the target host, to achieve...
DDOS attack DOS (denial of service) The purpose of the attack is to make the service normal...
The main basic differences: 1.GIT is distributed, SVN is not: This is the core difference between GIT and...
Get and Post are sent to the server a request, but the sending mechanism is different. 1. GET...
Google Authenticator OpenSource The Google Authenticator project includes implementations of one-time passcode generators for several mobile platforms....
What is Linux VPS hosting? If you have a high throughput site, or at least the expected...
A web search engine is a software system that is designed to search for information on the World Wide...
HTTP is short for HyperText Transfer Protocol, HTTP is a set of standards that allow users of...
Introduction to HTTP The HTTP protocol is an abbreviation for the Hyper Text Transfer Protocol (Hypertext Transfer...