CData Products Targeted: Path Traversal Vulnerability Opens Door to Sensitive Data

A newly uncovered path traversal vulnerability in the Java-based deployments of several CData business integration products poses a significant threat to organizations, security researchers at Tenable warn. This vulnerability, if left unpatched, could allow unauthenticated attackers to steal sensitive data or potentially take complete control of affected applications.

Image: CData
The Vulnerability’s Roots
The problem stems from a dangerous combination:
-
Unexpected Interactions: CData’s servlets and the embedded Jetty web server handle requests in a way that inadvertently weakens the intended security restrictions.
-
Lax Filtering: Jetty fails to reject \ characters in URIs in URIs as other web servers might. CData’s servlets still process these URIs, opening a path for malicious actors to exploit.
-
Missing Checks: Many endpoints within the CData applications fail to explicitly check for valid user sessions, making them ripe targets for an attacker using the path traversal technique.
Severity and Impact
The potential fallout from this vulnerability is severe. Let’s break down the CVEs:
- CVE-2024-31848, CVE-2024-31849 (CVSS 9.8): “Critical” rating. Attackers could gain complete administrative control of CData API Server or CData Connect.
- CVE-2024-31850, CVE-2024-31851 (CVSS 8.6): “High” rating. Opens up sensitive information and limited actions on CData Arc and CData Sync.
Proof of Concept
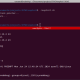
A simple test to demonstrate the vulnerability involves accessing /src/getSettings.rsb on the vulnerable server. The response could reveal highly sensitive data about the target system.
The Fix Is In, but Are You Safe?
CData has thankfully released hotfixes for each affected product. Organizations are strongly urged to apply these updates immediately. If you rely on these tools for critical business processes, patching is not optional.