Check Point Exposes Outlook’s Silent Attack Vectors

Outlook, a cornerstone of enterprise communication, is more than just an email client. It’s a hub of activity, connecting people across organizations. However, beneath its user-friendly surface lies a battlefield where cyber threats lurk in the shadows, exploiting vulnerabilities to infiltrate the secure walls of enterprises. Security researchers from Check Point delve into the sophisticated world of Outlook attack vectors, revealing the silent but deadly threats that could be just a click away.
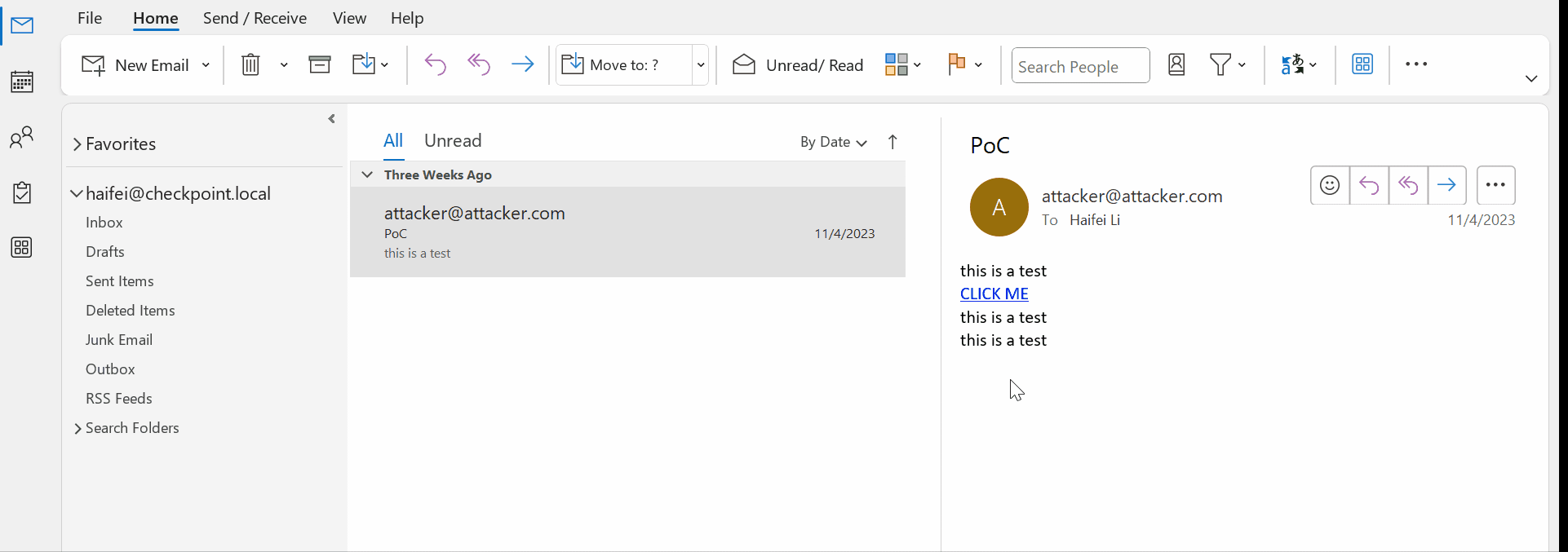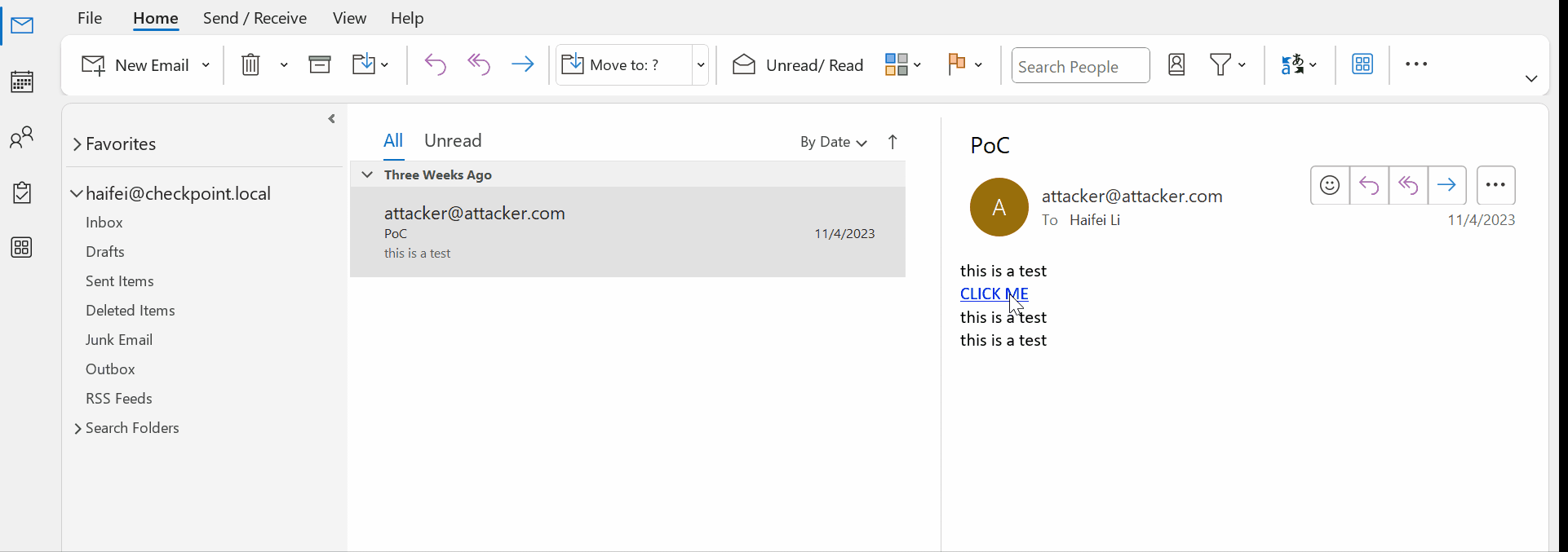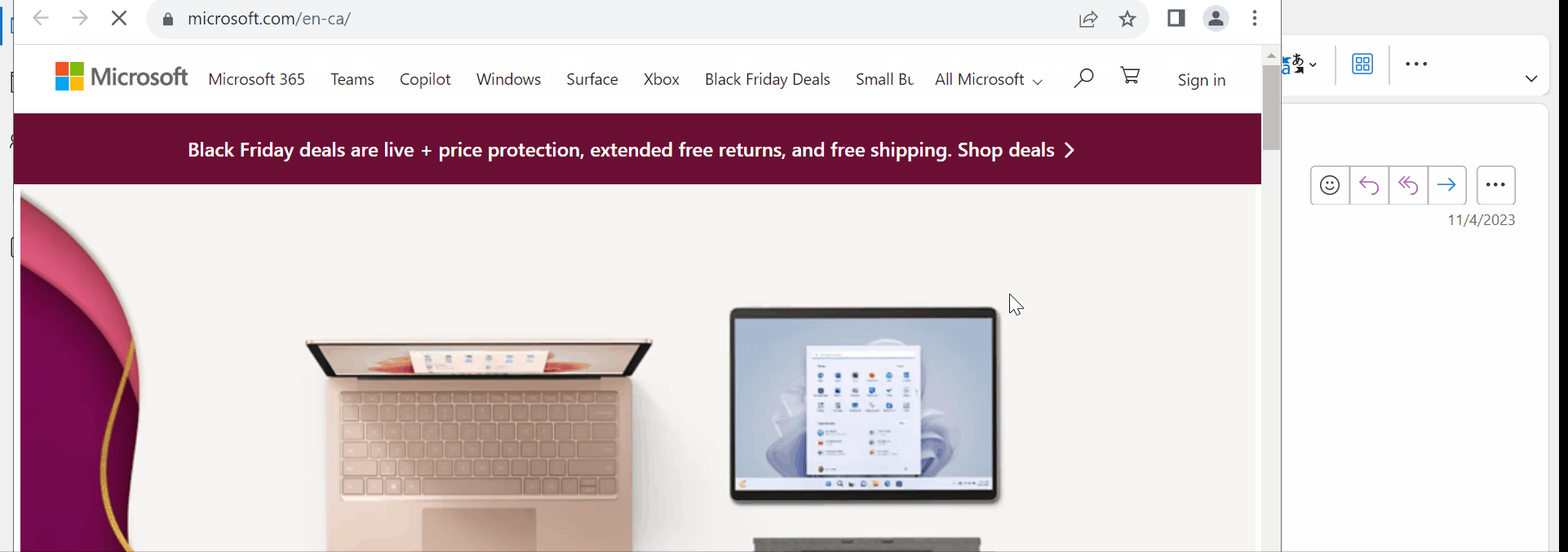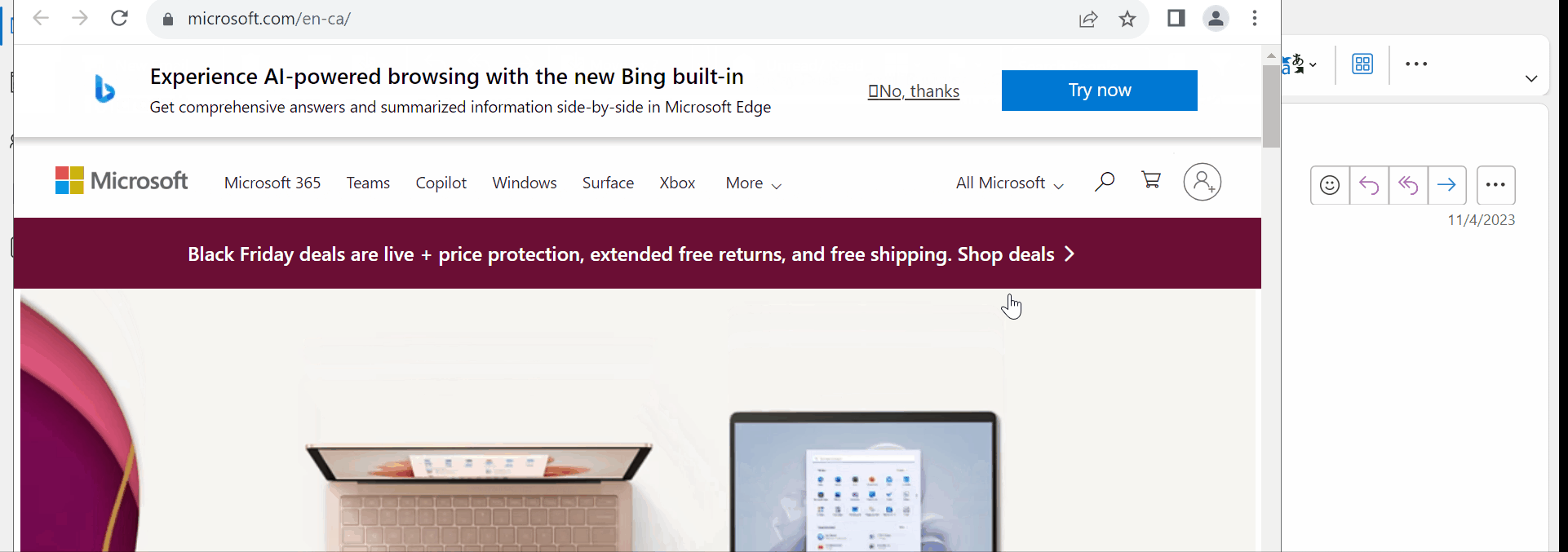
gif showing web links in Outlook email | Image Credit: Check Point
The simplest yet most deceptive threat comes from hyperlinks. A single click on a malicious link, and you’re trapped. These links serve as conduits to phishing attacks, browser exploits, and even zero-day vulnerabilities. The simplicity of this attack vector makes it a popular choice for attackers, leveraging the ease of a single click to launch a web-based attack.
Attachments, a routine aspect of emails, hide potential dangers. When double-clicked, Outlook calls upon the default application to open the attachment. The risk here depends on the security of that application. Even a single click on an attachment can initiate a preview within Outlook, subtly executing malicious code. These attachment-based attacks are a wolf in sheep’s clothing, exploiting our habit of opening documents without a second thought.
The most sophisticated and alarming attack vectors are those that require no user interaction. Merely receiving or previewing an email can trigger these attacks. These vectors exploit the core functions of Outlook, making them particularly insidious and challenging to detect.
When assessing the risk of these attack vectors, it’s crucial to consider the user’s role. Some attacks require active interaction, like clicking a link or an attachment, while others are more passive, leveraging the mere act of receiving or reading an email. The complexity of exploitation increases with the level of user interaction, shaping the landscape of cybersecurity defense strategies.
Understanding these attack vectors is crucial for both individuals and organizations. It emphasizes the need for constant vigilance and robust cybersecurity measures. From individuals being cautious about the links they click and the attachments they open to organizations employing comprehensive security solutions, the fight against these hidden threats is a collective effort.





