Check Point released February 2018’s Top 10 ‘Most Wanted’ Malware
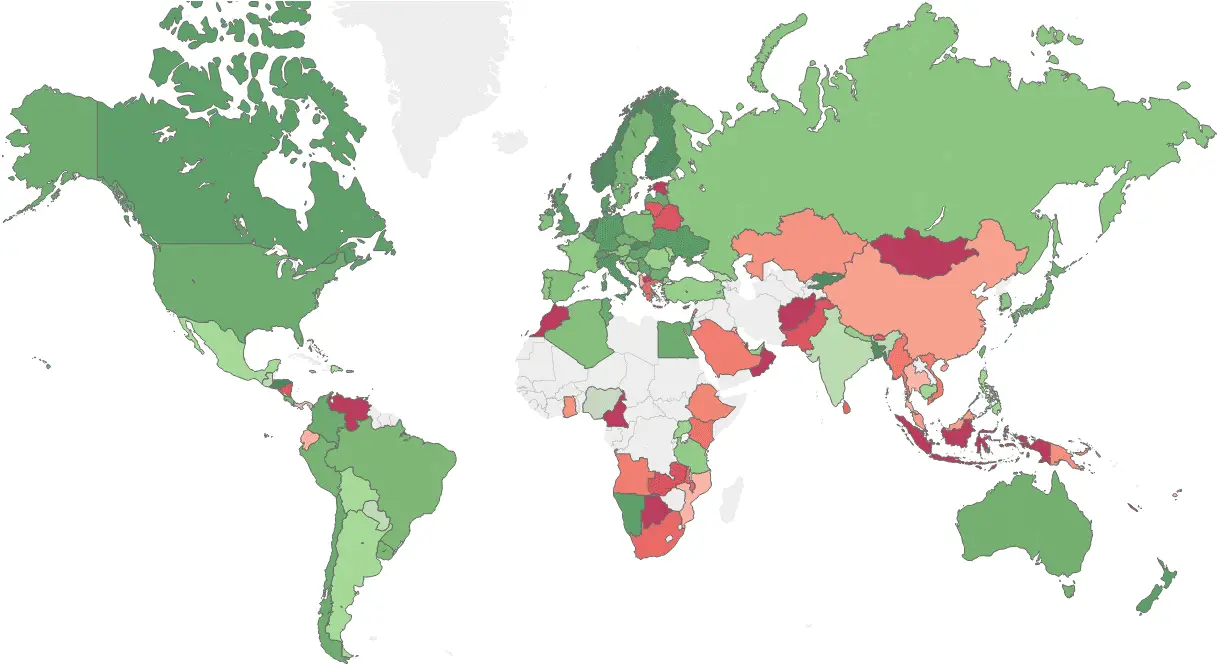
The latest report from checkpoint, the security company, the Global Malware Threat Impact Index, online released the top 10 malware of February 2018, most popular with cybercriminals.
Since February of this year, cryptocurrency mining malware has continued to affect global companies. According to Check Point statistics, 42% of companies worldwide are affected.
Coinhive is still the most popular malware, affecting 20% of the world’s companies, followed by Cryptoloot 16% and Rigek 15%.
Cryptoloot entered the top three for the first time. In order to compete with Coinhive, Cryptoloot has been trying to expand its customer base through “benefit” to reverse the situation in the encryption market. As a result, its global influence this month more than doubled, from 7% in January to 16% in February.

Image: checkpoint
In the past four months, cryptocurrency mining malware has continued to increase. Because for cybercriminals, it is more profitable than other malware.
It is worth noting that, in addition to slowing the speed of computers or servers, cryptocurrency mining malware can also carry out other malicious activities within the infected system. It is imperative for companies and other organizations to develop appropriate solutions to this type of malicious software to prevent new large-scale cyber attacks.
February 2018’s Top 10 ‘Most Wanted’ Malware:
- ↔ Coinhive – Crypto-Miner designed to perform online mining of Monero cryptocurrency when a user visits a web page without the user’s approval.
- ↑ Cryptoloot – Crypto-Miner that uses the victim’s CPU or GPU power and existing resources for crypto mining – adding transactions to the blockchain and releasing new currency.
- ↔ Rig ek – Rig delivers Exploits for Flash, Java, Silverlight and Internet Explorer
- ↑ JSEcoin – JavaScript miner that can be embedded in websites.
- ↓ Roughted – Large scale Malvertising used to deliver various malicious websites and payloads such as scams, adware, exploit kits and ransomware.
- ↓ Fireball – Browser-hijacker that can be turned into a full-functioning malware downloader.
- ↑ Necurs – Botnet used to spread malware by spam emails, mainly Ransomware and Banking Trojans.
- ↓ Andromeda – Modular bot used mainly as a backdoor to deliver additional malware on infected hosts.
- ↑ Virut – Botnet known to be used for cybercrime activities such as DDoS attacks, spam, fraud, data theft, and pay-per-install activities.
- ↓ Ramnit – Banking Trojan that steals banking credentials, FTP passwords, session cookies and personal data.
February’s Top 3 ‘Most Wanted’ mobile malware:
- Triada – Modular Backdoor for Android which grants superuser privileges to downloaded malware.
- Lokibot – Android banking Trojan and info-stealer, which can also turn into a ransomware that locks the phone.
- Hiddad– Android malware which repackages legitimate apps then releases them to a third-party store.