Chinese hackers use new malware to attack the U.K government

A hacker spy organization discovered last year was thought to be associated with the Chinese government and recently used a new type of malware to attack the British government. At the Kaspersky Security Summit held in Cancun last week, senior malware researcher Ahmed Zaki released the attack details. The attack is believed to be APT15 hackers launched, according to a recent analysis of the activities of the organization, it has a target for the company to provide a range of services for the U.K government.
The researchers believe the attacker targeted at different sectors of the British Government, other details revealed no more, Ahmed Zaki expressed APT15 hacker organizations are very active in East Asia. Since 2010 the organization has been using their malicious software, including Word, Adobe Reader, and Java vulnerabilities, looking for attacks on a global scale, will continue to update their hacking tools arsenal, it has recently been discovered two new backdoor program.
One of the backdoors is called RoyalCLI and is considered an upgraded version of the malware BS2005. It uses a similar encryption technology as BS2005 and uses IE browser’s IWebBrowser2 interface for remote communication. The program executes the command by opening the Windows command line program cmd.exe, and can also replace the system’s existing cmd.exe program to avoid being detected by the system.
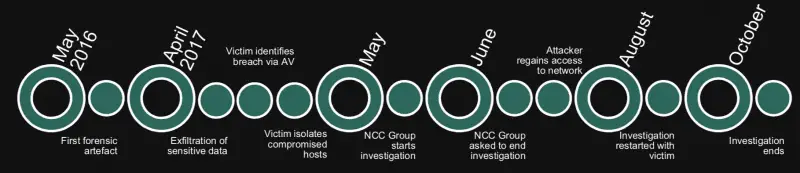
Another backdoor program is called RoyalDNS and uses DNS text file records for remote communication. In the case of researchers at the Security Summit, hackers have attacked more than 30 hosts, and the earliest attacks can be traced back to May 2016. In June 2017, the customer was asked to stop the investigation. However, since August 2017, the hacker re-attacked the customer’s network. Researchers concluded that the hackers had stolen a VPN certificate from a host to obtain the company’s VPN permissions.
Researchers discovered more than 200 commands used by hackers in the cache of the device being attacked and found a misspelled command in them, which concluded that the commands were entered by the person rather than the machine. In addition, the APT15 hacker group also used custom keyloggers, Microsoft SharePoint, Exchange server count, data transfer tools, Mimikatz, CSVDE, NetEnum, RemoteExec and other tools to implement the attack. You can also use the commands that come with the Windows operating system to perform attacks such as tasklist, ping, netstat, net, systeminfo, ipconfig, and bcp. The latest attack behavior is to use the net command to remotely copy files from the host. Therefore, it can be seen that the APT15 hacking organization is very powerful and can attack the target by writing specific hacking tools.
Source: securityweek





