CVE-2023-29552: CISA Warns of Actively Exploited SLP Vulnerability
In a chilling reminder of the ever-evolving cyber threat landscape, a critical vulnerability in the Service Location Protocol (SLP) has been discovered, leaving tens of thousands of devices vulnerable to devastating reflective Denial-of-Service (DoS) amplification attacks. This high-severity flaw, tracked as CVE-2023-29552, has already been added to the Known Exploited Vulnerabilities (KEV) catalog by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), highlighting the active exploitation of this vulnerability by threat actors.
The SLP vulnerability allows unauthenticated attackers to register arbitrary services on the vulnerable SLP server, manipulating the content and size of its reply to achieve a staggering amplification factor of 2,200x. This means that an attacker can send a small request to the vulnerable server, and in return, the server will send a massive response, amplifying the attack by 2,200 times.

Image: BitSight
With such a powerful amplification factor, attackers can easily overwhelm a target’s network with amplified traffic, rendering it inaccessible to legitimate users. This can have severe consequences for organizations, disrupting critical services, causing financial losses, and damaging reputations.
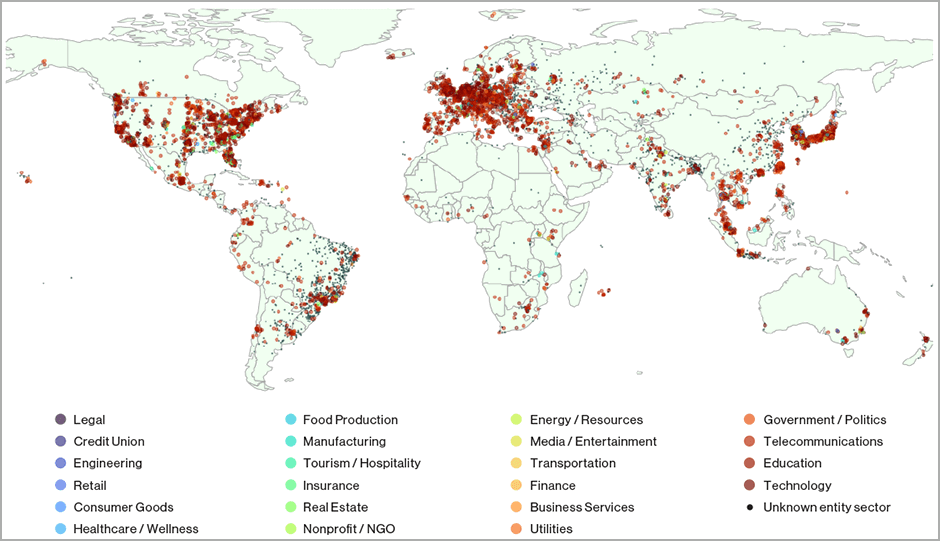
Researchers at BitSight and Curesec have cast a light upon a staggering number of over 2,000 organizations whose digital sentinels – ranging from the stalwart VMWare ESXi Hypervisors to the unassuming Konica Minolta printers, the robust IBM Integrated Management Modules, and the widespread Planex Routers – stand vulnerable, unwittingly offering about 54,000 exploitable SLP instances as gateways for havoc-wreaking DoS amplification onslaughts.
Making matters worse, many of these vulnerable instances are located in prominent countries like the United States, Great Britain, Japan, Germany, Canada, France, Italy, Brazil, the Netherlands, and Spain. This widespread exposure creates a tempting target for cybercriminals seeking to disrupt operations and cause widespread havoc.
Given the critical nature of the CVE-2023-29552 vulnerability, CISA has urged organizations to take immediate action to mitigate the risk of attack. Federal Civilian Executive Branch (FCEB) agencies are required to apply vendor-provided patches by November 29, 2023, to secure their networks against potential threats.
For other organizations, the onus lies on identifying and patching vulnerable devices as quickly as possible. Organizations should also consider implementing intrusion detection and prevention systems (IDS/IPS) to detect and block suspicious traffic, minimizing the impact of potential attacks.





