CoinLurker Malware Targets Crypto Users via Fake Browser Updates

Morphisec researchers have uncovered CoinLurker, a sophisticated data-stealing malware that powers the latest wave of fake browser update campaigns. Leveraging advanced obfuscation, in-memory execution, and blockchain techniques, CoinLurker poses a significant threat to cryptocurrency users and businesses alike.
Fake updates are not new but have grown increasingly sophisticated. CoinLurker builds on strategies seen in campaigns like SocGolish and ClearFake. According to Morphisec: “Attackers now combine highly convincing fake update prompts with stealthy payloads like CoinLurker. These campaigns leverage innovative methods, such as EtherHiding and in-memory execution, to bypass traditional security defenses and obscure the malware’s origin.”
The infection chain relies on exploiting user trust through various vectors:
- Fake Software Updates: Websites prompt users to install fake updates for browsers or tools.
- Malvertising: Compromised ads redirect users to malicious download pages.
- Phishing Emails: Links in emails spoof legitimate update notifications.
- Fake CAPTCHA Prompts: Instead of verifying users, the prompts deliver malware.
- Social Media and Compromised Sites: Attackers use deceptive download links shared across platforms.
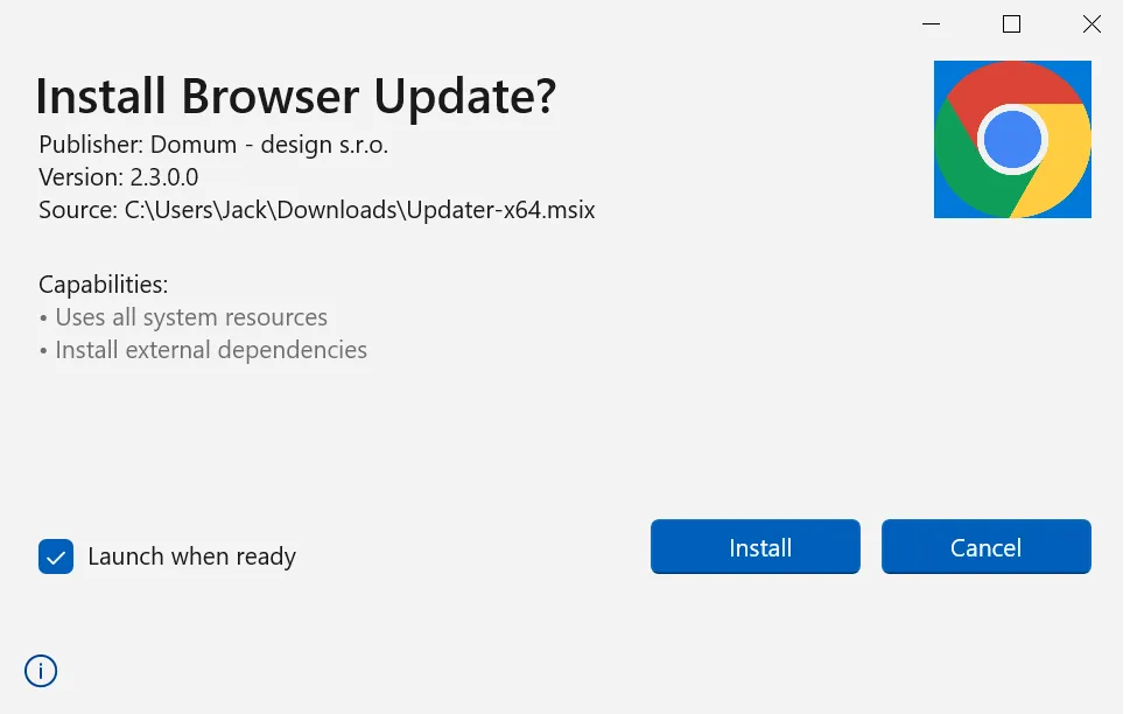
Chrome fake update Webview2 GUI | Source: Morphisec
CoinLurker takes advantage of Microsoft Edge Webview2, which mimics legitimate update windows. Morphisec explains: “Webview2’s dependency on pre-installed components and user interaction complicates dynamic and sandbox analysis. Sandboxes often lack Webview2 or fail to replicate user actions, allowing the malware to evade automated detection.”
CoinLurker employs a multi-stage delivery process that cleverly obscures its origin:
- Binance Smart Contract: The malware uses blockchain-based contracts to store encoded payload instructions. These decentralized platforms make removal difficult.
- Actor-controlled C2 Server: The smart contract directs the malware to a command-and-control (C2) server that dynamically fetches further payloads.
- Bitbucket Repository: Initially hosting clean executables, the repository later swaps them for malicious versions, leveraging Bitbucket’s trusted reputation.
Morphisec notes that filenames such as “Updater.exe” and “SecurityPatch.exe” align with the fake update theme. Moreover, these files are often signed with stolen Extended Validation (EV) certificates to appear legitimate.
CoinLurker employs a layered injector to ensure stealth:
- It dynamically injects payloads into legitimate msedge.exe processes.
- Command-line arguments like “WSCOGJJEZZWL” and “PEQDTHUEORHX” are obfuscated and decoded only at runtime, leaving no static traces for traditional detection tools.
CoinLurker zeroes in on cryptocurrency wallets and financial data, emphasizing its focus on harvesting sensitive user information. Key directories targeted include:
- Bitcoin Wallets:
Bitcoin\wallets - Ethereum:
Ethereum\keystore - Exodus Wallet:
exodus.wallet - Ledger Live:
Local Storage\leveldb
Beyond mainstream wallets, it scans for obscure alternatives like BBQCoin and MemoryCoin, highlighting its adaptability. Related applications such as Telegram Desktop, Discord, and FileZilla are also targeted for additional credential theft.
Morphisec adds: “CoinLurker’s comprehensive scanning underscores its primary goal of harvesting cryptocurrency-related data and user credentials, covering both mainstream and lesser-known wallets.”
Related Posts:
- Morphisec discovered a new watering hole attack based Flash flaw on Leading Hong Kong Telecom Site
- CVE-2024-38021: Zero-Click Vulnerability Discovered in Microsoft Outlook
- Researcher Details Microsoft Outlook Zero-Click Vulnerability (CVE-2024-38021)
- Apache HTTP Server Hit by Triple Vulnerabilities – Users Urged to Update






