Commando Cat Cryptojacking Campaign Unleashed: Docker Users Under Threat
Cybersecurity researchers at Trend Micro have uncovered a novel cryptojacking campaign dubbed “Commando Cat,” actively targeting Docker Remote API servers. This sophisticated attack exploits exposed servers to deploy cryptocurrency miners, potentially draining resources and generating illicit profits for the attackers. This campaign has been active since the start of 2024.
The attack begins by deploying a benign Docker image named cmd.cat/chattr. Once deployed, the attacker creates a Docker container based on this image and uses chroot to break out of the container, gaining access to the host operating system. The attacker then uses curl or wget to download the malicious binary onto the host.
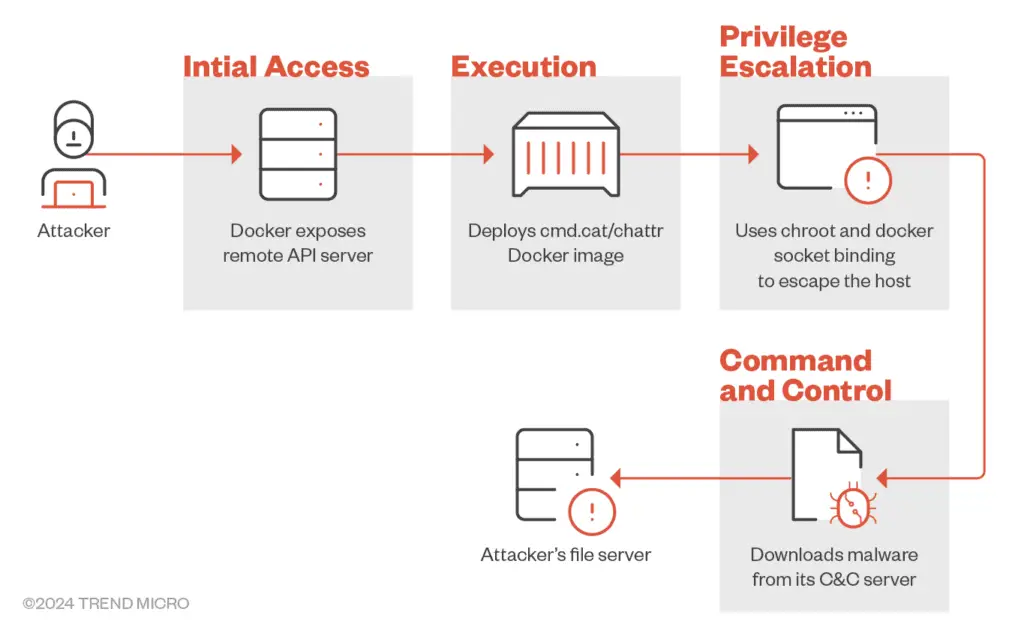
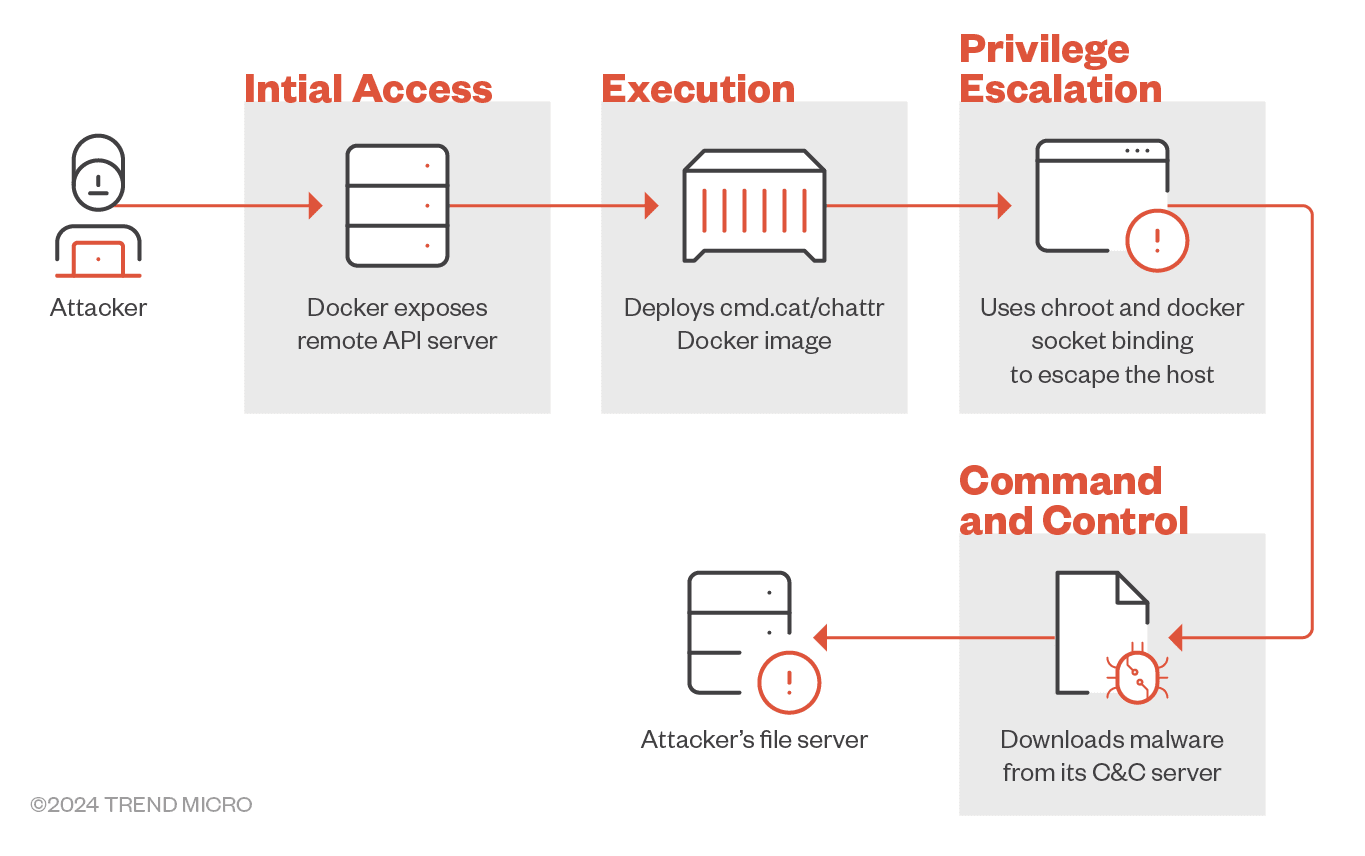
Commando Cat attack sequence
Let’s break down the attack sequence step-by-step:
- Probing the Docker Remote API Server The attack starts with a ping to the Docker Remote API server, initiating the subsequent chain of actions.
- Creating the Container Using cmd.cat/chattr Image After confirming the server’s status as “OK,” the attacker instantiates a container using the cmd.cat/chattr image. The attacker employs chroot and volume binding to escape the container, mounting the host’s root directory into the container’s /hs directory, thus gaining unrestricted access to the host file system. The Docker socket is also bound, giving the container direct access to the Docker daemon on the host.
- Image Creation in Absence If the container creation request returns a “No such image” response, the attacker pulls the chattr Docker image from the cmd.cat repository.
- Container Deployment With the image in place, the attacker creates a Docker container, executing a base64-encoded shell script. The script checks if a file named “z” exists in /usr/sbin/. If not, it downloads and executes a malicious binary from hxxp[:]/leetdbs[.]anondns[.]net/z, potentially ZiggyStarTux, an IRC bot based on the Kaiten malware. This binary is packed using the UPX packer.
During the analysis, the C&C server was found to be down. However, the following User-Agent strings in the binary can be used to detect the presence of this malware in the network:
- User-Agent: HackZilla/1.67 [en] (X11; U; Linux 2.2.16-3 x64)
- User-Agent: Mozilla/4.75 [en] (X11; U; Linux 2.2.16-3 i686)
The malware uses DropBear SSH, a small SSH server and client application on TCP port 3022. The deployed malware attempts to connect to its C&C server at 45[.]9[.]148[.]193 on port 1219, initiating IRC communication.
The Commando Cat campaign underscores the threat posed by abusing Docker images to deploy cryptojacking scripts on compromised systems. This tactic exploits vulnerabilities in Docker configurations while evading detection by conventional security software.
To safeguard against Commando Cat and similar attacks, organizations are advised to:
- Secure Docker Configurations: Ensure that Docker Remote API servers are not exposed to the public internet and are protected by strong authentication mechanisms.
- Follow Least Privilege Principle: Run containers with the minimum necessary privileges to limit the potential damage of a compromise.
- Validate Image Integrity: Employ image scanning and verification tools to identify and block malicious or unauthorized containers.
- Implement Continuous Monitoring: Regularly audit Docker environments for suspicious activity and unauthorized changes.





