CORS misconfiguration vulnerable Lab
CORS misconfiguration vulnerable Lab
This Repository contains CORS misconfiguration related vulnerable codes. One can configure the vulnerable code on the local machine to perform practical exploitation of CORS related misconfiguration issues.
Challenges available in this lab
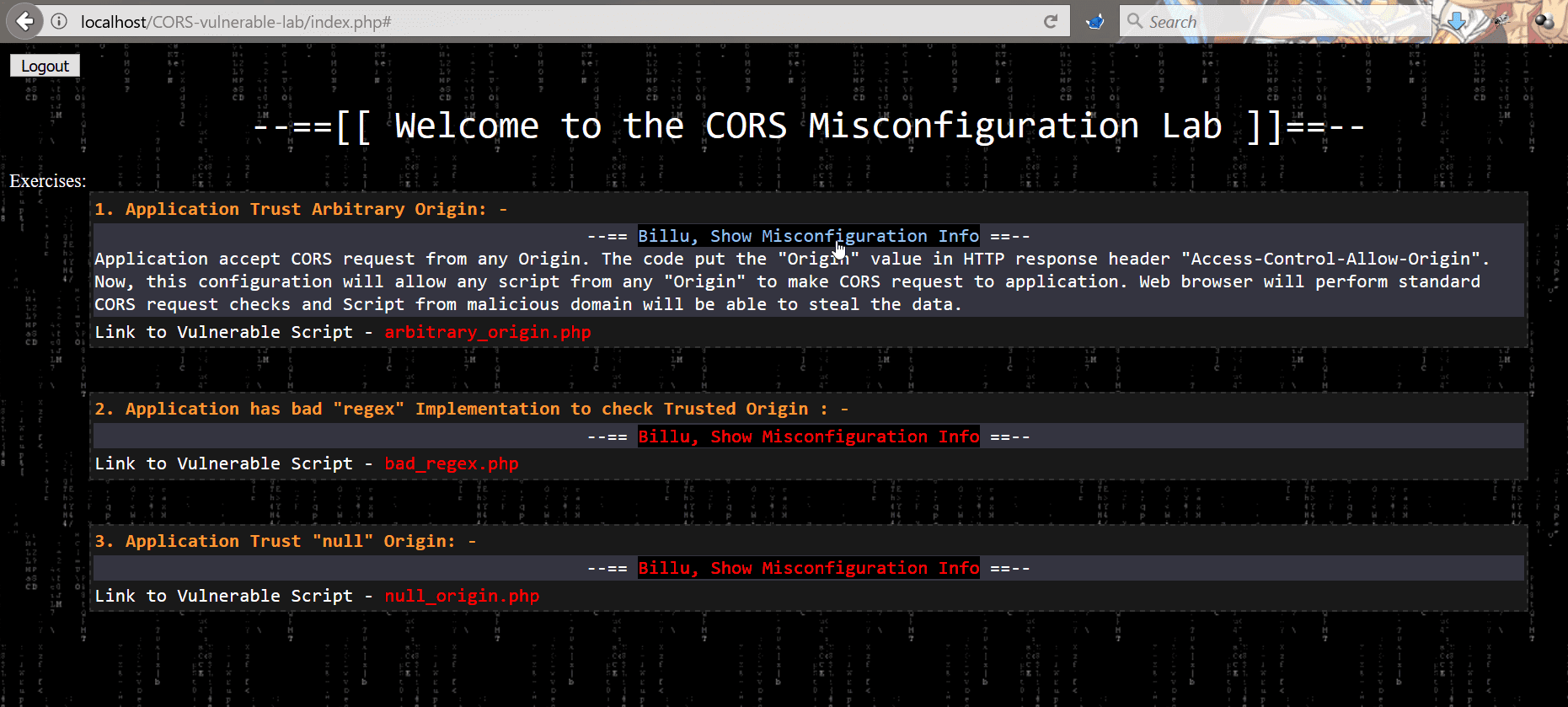
There is 3 misconfiguration which is simulated in this Lab.
Application Trust Arbitrary Origin
The application accepts CORS request from any Origin. The code put the “Origin” value in HTTP response header “Access-Control-Allow-Origin”. Now, this configuration will allow any script from any “Origin” to make CORS request to the application. A web browser will perform standard CORS request checks and Script from malicious domain will be able to steal the data.
Application has bad “regex” Implementation to check Trusted Origin
Application has CORS policy implemented and perform “Regex” check for whitelisted Domain/Sub-domains. In this scenario, the application has weak regex implementation in code which just checks for the presence of domain name “b0x.com” anywhere in HTTP request “Origin” header. If HTTP header “Origin” has value “inb0x.com” or b0x.comlab.com, the regex will mark it pass. This misconfiguration will lead to sharing of data over cross-origin.
Application Trust “null” Origin
In this scenario, application HTTP response header “Access-Control-Allow-Origin” is always set to “null”. When the user specifies any value other than null, the application does not process it and keep reflecting “null” in the HTTP response. There are few tricks which allow an attacker to perform exploitation and can ex-filtrate data of victim using CORS request.





