Critical Vulnerabilities in Kakadu JPEG 2000 Library Expose Systems to Remote Attacks
Researchers from the Google Chrome Vulnerability Rewards (CVR) team have identified a series of critical vulnerabilities within the Kakadu image library, a widely deployed software component used for processing JPEG 2000 images. These vulnerabilities, if exploited, could permit malicious actors to execute arbitrary code on affected servers and gain unauthorized access to sensitive information.
JPEG 2000, a popular image compression standard, is supported by the Kakadu library, making it a common component in various applications and systems. The CVR team’s findings reveal a series of vulnerabilities within the library’s image-processing mechanisms, opening the door for remote exploitation.
Novel Attack Technique: Conditional Corruption
One of the major challenges in exploiting such vulnerabilities is the unknown nature of the runtime environment, which typically renders traditional attack preparation methods ineffective. However, the CVR researchers devised an innovative technique called “Conditional Corruption.” This technique enables them to modify an image in a way that triggers the conditions for a successful attack upon processing.
Vulnerabilities and their Impact:
-
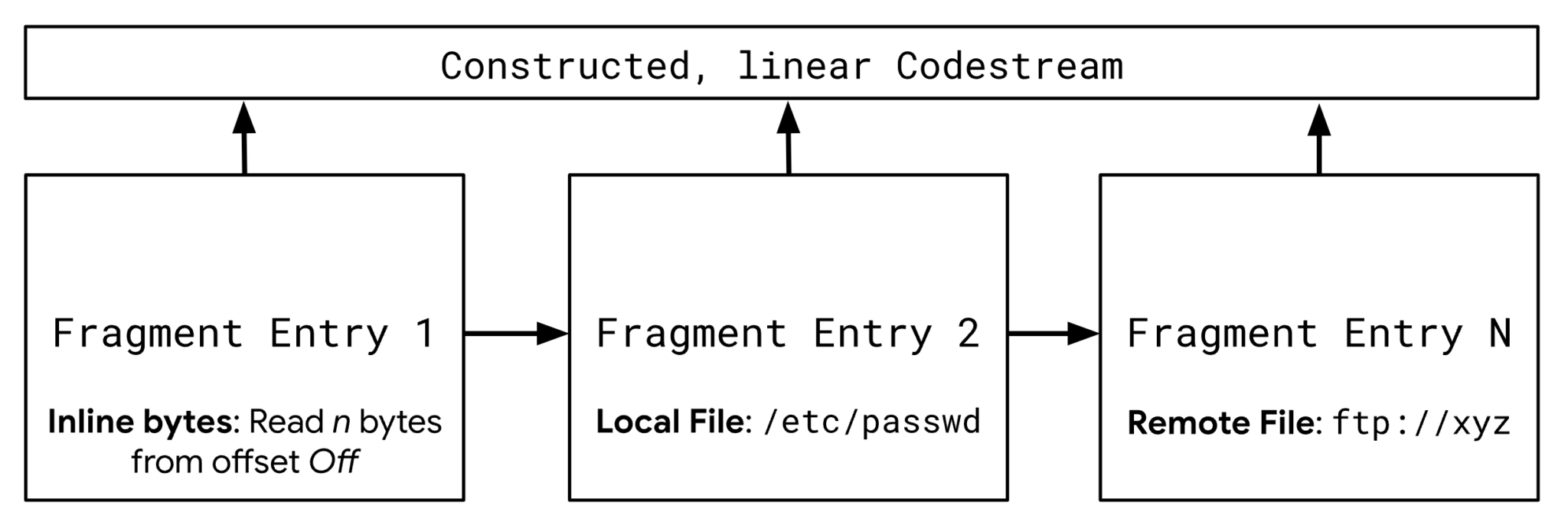
Arbitrary File Read: One of the identified flaws allows attackers to read arbitrary files on the server. Due to the specific data fragmentation in JPEG 2000, attackers can replace image fragments with bytes from local files, potentially gaining access to critical data like memory card files and process environment information.
-
Heap Overflow: Another vulnerability stems from errors in number multiplication within the library’s code, leading to data being written outside of allocated memory space. This “Heap Overflow” condition can be exploited to execute malicious code on the server.
Overcoming Exploitation Challenges
Exploiting these vulnerabilities in a distributed environment is further complicated by the inability to ensure that the same server will handle repeated requests. To overcome this, the CVR team leveraged the unique characteristics of the Kakadu library to identify servers running it, allowing for more targeted attacks.
Additionally, the researchers developed a mechanism to bypass common protection methods like Address Space Layout Randomization (ASLR), which makes it difficult to predict memory addresses used during code execution. This was achieved by reading memory contents in real time and adapting the attack based on the gathered information.
Urgent Call to Action
This research underscores the serious threat of seemingly minor vulnerabilities in widely used libraries. Users of the Kakadu library are strongly urged to update to the latest version immediately to mitigate the risk of potential attacks exploiting these discovered vulnerabilities.





