Critical Vulnerabilities in Kia’s Dealer Portal Expose Millions of Vehicles to Remote Hijacking
In a startling revelation that underscores the growing cybersecurity risks in the automotive industry, security researchers have uncovered critical vulnerabilities in Kia’s dealer portal that could allow attackers to stealthily steal and control parked vehicles remotely. The identified flaws make it possible to hack any Kia model released after 2013 using nothing more than the car’s license plate number.
This isn’t the first time the automotive sector has faced such threats. In 2022, a team of security researchers, including renowned vulnerability hunter Sam Curry, discovered severe flaws in the digital systems of over a dozen car manufacturers. Those vulnerabilities permitted attackers to remotely locate, lock, unlock, and even start the engines of more than 15 million premium vehicles, including luxury brands like Ferrari, BMW, Rolls Royce, and Porsche.
Building on that precedent, Curry and his team reported on June 11 of this year that breaches in the Kia Connect portal granted unauthorized access to control any Kia vehicle equipped with remote technology—even if the owner hadn’t activated the Kia Connect subscription.
Beyond the alarming possibility of vehicle theft, the vulnerabilities also exposed the sensitive personal data of Kia owners. Attackers could obtain names, phone numbers, email addresses, and physical addresses. Even more concerning, they could add themselves as secondary users in the system without the owner’s knowledge, gaining persistent access to the vehicle’s functions.
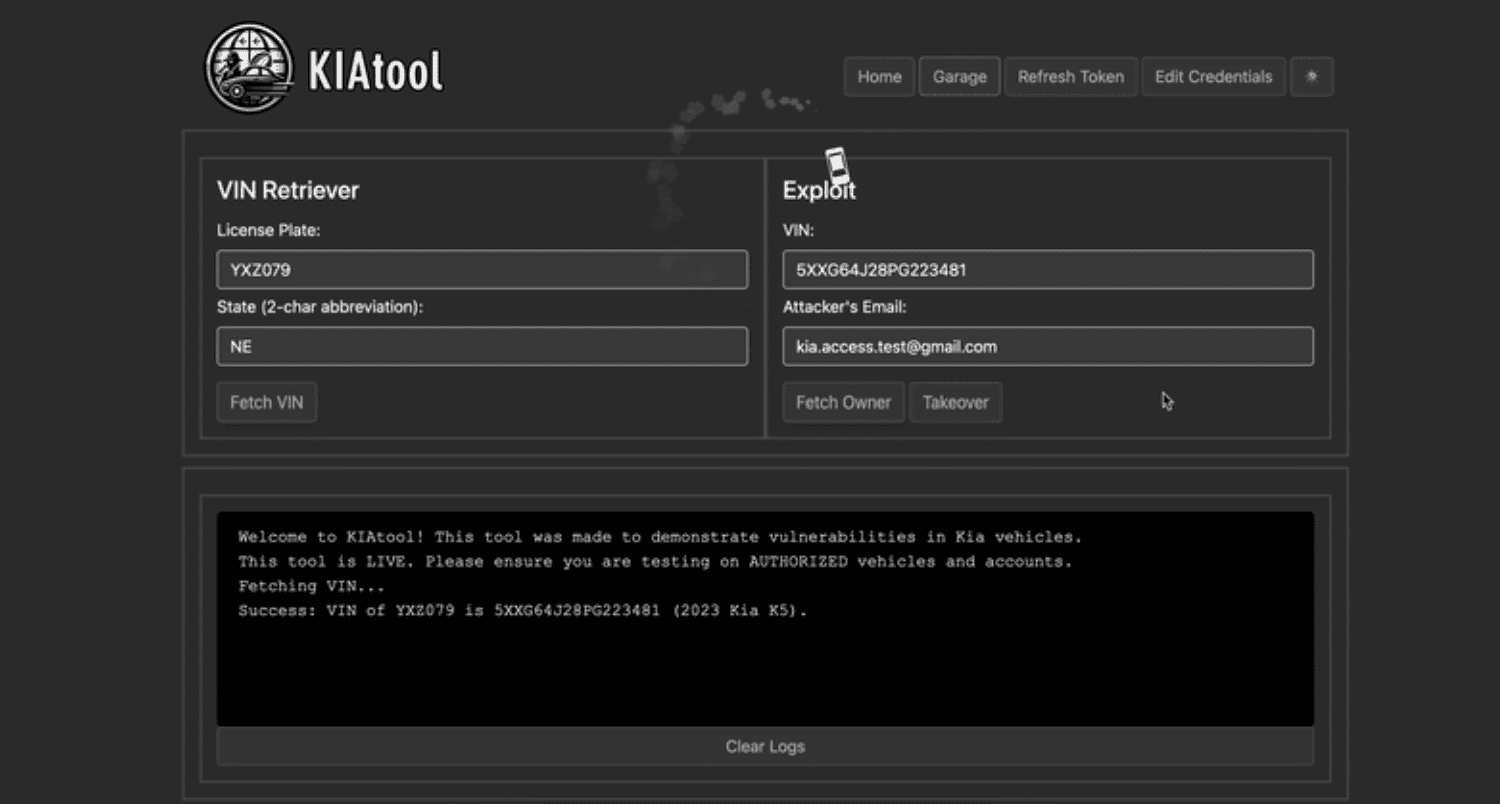
To highlight the severity of the issue, the research team developed a tool capable of adding vehicles to a “virtual garage” using only the license plate number. With this tool, they could remotely lock or unlock doors, start or stop the engine, honk the horn, and even pinpoint the car’s location on a map—all without any physical interaction with the vehicle.
By accessing the Kia dealer portal at kiaconnect.kdealer.com, the researchers registered a privileged account and generated a valid access token. This token allowed them to interact with the dealer backend API, granting them critical information about car owners and unfettered control over the vehicles’ remote functions.
Attackers exploiting this API could:
- Generate a Dealer Token: Retrieve it from the HTTP response to gain authorized access.
- Access Personal Owner Information: Including email addresses and phone numbers.
- Modify Access Rights: Using the acquired data to alter permissions without detection.
- Add Unauthorized Users: Insert their own email address into the vehicle’s account to control the car remotely.
The covert nature of these exploits meant that unauthorized access could occur without triggering any notifications or alerts to the vehicle’s owner. This silent manipulation posed a significant risk, as owners remained oblivious to the breach of their vehicle’s security and personal data.
Fortunately, all identified vulnerabilities have been patched promptly. Sam Curry confirmed that the tool developed to demonstrate the exploit was never released publicly, mitigating the risk of widespread malicious use. Kia’s security team also verified that the discovered flaws were not exploited for nefarious purposes in the wild.




