CrossBarking Vulnerability in Opera Browser Allows Malicious Extensions to Hijack User Accounts
Guardio Labs has unveiled a critical security flaw in the Opera browser, dubbed “CrossBarking,” which allows malicious extensions to bypass security protocols and exploit Private APIs. This vulnerability grants attackers the capability to capture screens, alter browser settings, and even hijack user accounts. The findings, led by Nati Tal, Head of Guardio Labs, expose a serious threat to users and emphasize the growing tension between user productivity and security in modern browsers.
In their report, Guardio Labs explains how browsers, particularly Chromium-based ones like Opera, integrate Private APIs to enhance user experience. These APIs facilitate specific features, such as Opera’s Pinboard and Wallet services, by giving them privileged access to browser functionalities. Nati Tal notes, “Modern websites function like fully-fledged applications… your browsing context must be completely sandboxed — isolated from the rest of your system”. However, these Private APIs, meant to be securely contained, are exploitable due to over-permissive domain access.
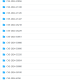
To showcase the vulnerability’s impact, Guardio Labs researchers developed a proof-of-concept extension featuring adorable puppy imagery—a seemingly innocent add-on that hid malicious capabilities. According to the report, “All we need is to open a tab to a page under [a permissive] domain, inject our specially crafted code, and call chrome.settingsPrivate.setPref()”. This exploit altered users’ DNS settings without their knowledge, paving the way for phishing attacks and more.
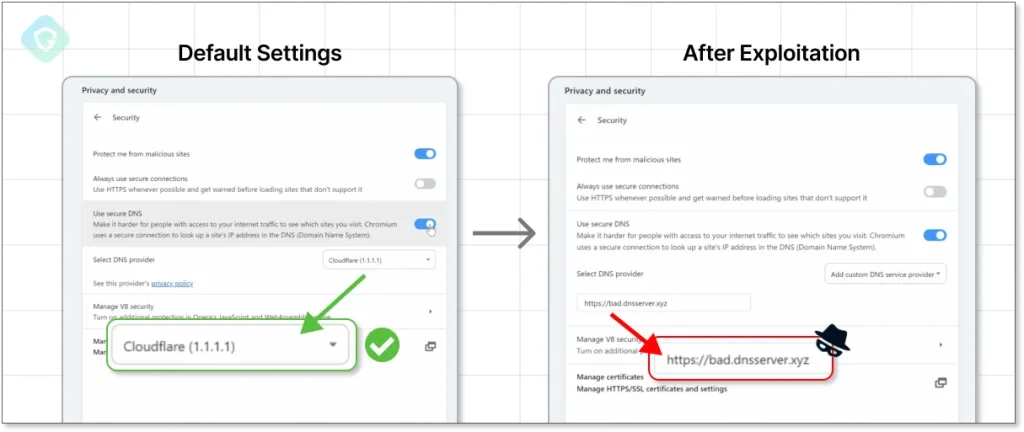
How the exploit changes the DNS over HTTPs setting | Image: Guardio Labs
While Opera has stringent extension reviews, it also allows users to install Chrome extensions, bypassing Opera’s review process. Guardio’s team revealed, “To illustrate the unfortunate ease of bypassing extension store security measures… we were able to stash our malicious, private-API-exploiting Opera extension inside the official Chrome Store”. This cross-store vulnerability highlights a potential threat to millions of users, given the Chrome Store’s widespread reach.
Upon being alerted, Opera collaborated with Guardio Labs to implement a fix. Opera emphasized, “This highlights the importance of a robust review process… and the power extensions can wield”. Thanks to Guardio’s proactive reporting, the vulnerability was patched on September 24th, ensuring that no users fell victim to the attack.