CISA warns of critical Red Hat JBoss RichFaces Framework RCE flaw exploited in attacks
The Cybersecurity and Infrastructure Security Agency (CISA) has added a critical severity vulnerability in the Red Hat JBoss RichFaces Framework to its catalog of security flaws exploited in the wild.
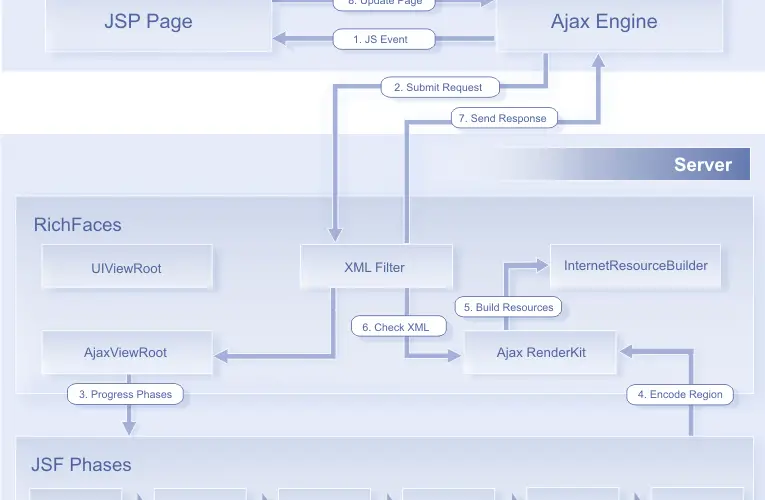
The JBoss RichFaces Framework, designed by Red Hat, is a component library that seamlessly integrates AJAX capabilities into pre-existing pages. Unlike traditional setups that require individual AJAX widgets or JavaScript code, RichFaces offers a holistic approach to AJAX support, allowing designers to designate specific areas of a webpage to be impacted by AJAX events.
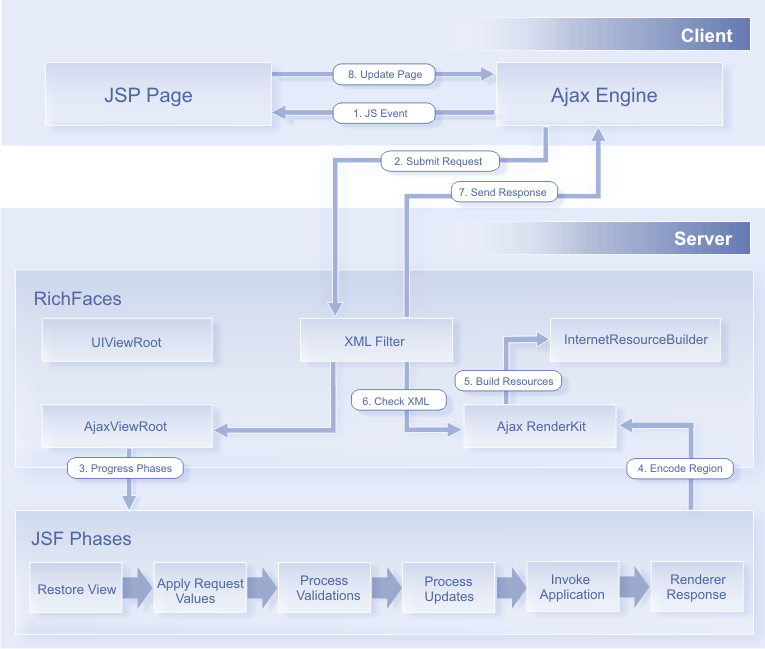
Image Credit: Red Hat
Tracked as CVE-2018-14667, this vulnerability has received an alarming severity score of 9.8/10 from Red Hat – a nearly perfect score that signals its potential danger. Versions 3.X through 3.3.4 of the RichFaces Framework are particularly vulnerable, prone to Expression Language (EL) injection through the UserResource resource. In more technical terms, this means that a remote attacker, without needing authentication, can exploit this flaw and execute arbitrary code using a chain of java serialized objects via org.ajax4jsf.resource.UserResource$UriData.
This flaw’s discovery was credited to Joao Filho Matos Figueiredo, who subsequently reported it to Red Hat, leading to the release of pertinent security updates.
Red Hat released security updates to address the CVE-2018-14667 flaw in November 2021, but CISA has now ordered U.S. federal agencies to secure their systems against attacks within three weeks, until October 19th, 2023.
CISA emphasized the gravity of the situation, noting that “These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise.” Such a statement underscores the urgency with which organizations should respond.
For those using the JBoss RichFaces Framework, it’s essential to take immediate action. Updating to the latest version and applying Red Hat’s security patches should be the top priority. Systems administrators and IT professionals should also remain vigilant, constantly monitoring their setups for any unusual activities or potential breaches.






