Recently, VMware issued a security bulletin to
disclose a remote code execution vulnerability (CVE-2022-22947) in Spring Cloud Gateway. Applications using Spring Cloud Gateway can be exploited when Gateway Actuator endpoint is enabled, exposed, and unsecured, attackers can trigger remote arbitrary code execution by sending specially crafted malicious requests to applications using Spring Cloud Gateway. This vulnerability was discovered and responsibly reported by Wyatt Dahlenburg. The difficulty of exploitation is low, and the POC is currently
public.
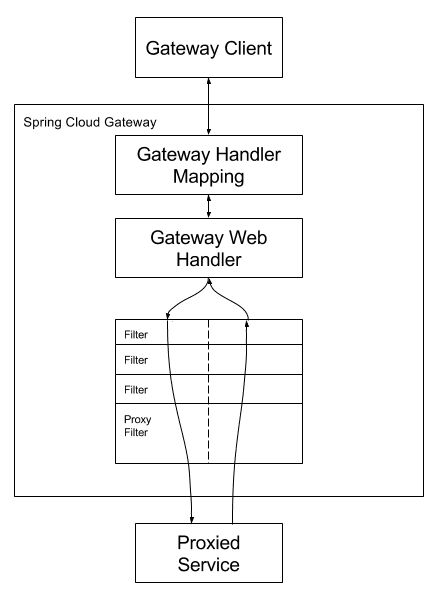
Spring Cloud Gateway aims to provide a simple, yet effective way to route to APIs and provide cross-cutting concerns to them such as security, monitoring/metrics, and resiliency.
Affected version
- Spring Cloud Gateway
- 3.1.0
- 3.0.0 to 3.0.6
- Older, unsupported versions are also affected
Unaffected version
Solution
At present, the new Spring Cloud Gateway version has been released to fix the CVE-2022-22947
vulnerability, please upgrade to the unaffected version as soon as possible. Users who cannot upgrade in time can refer to the repair suggestions for mitigation:
- If the Gateway actuator endpoint is not needed it should be disabled via management.endpoint.gateway.enabled: false
-
If you need an Actuator, use Spring Security to protect it. For details, please refer to the
official instructions.