CVE-2022-24112: Apache APISIX Remote Code Execution Vulnerability Alert
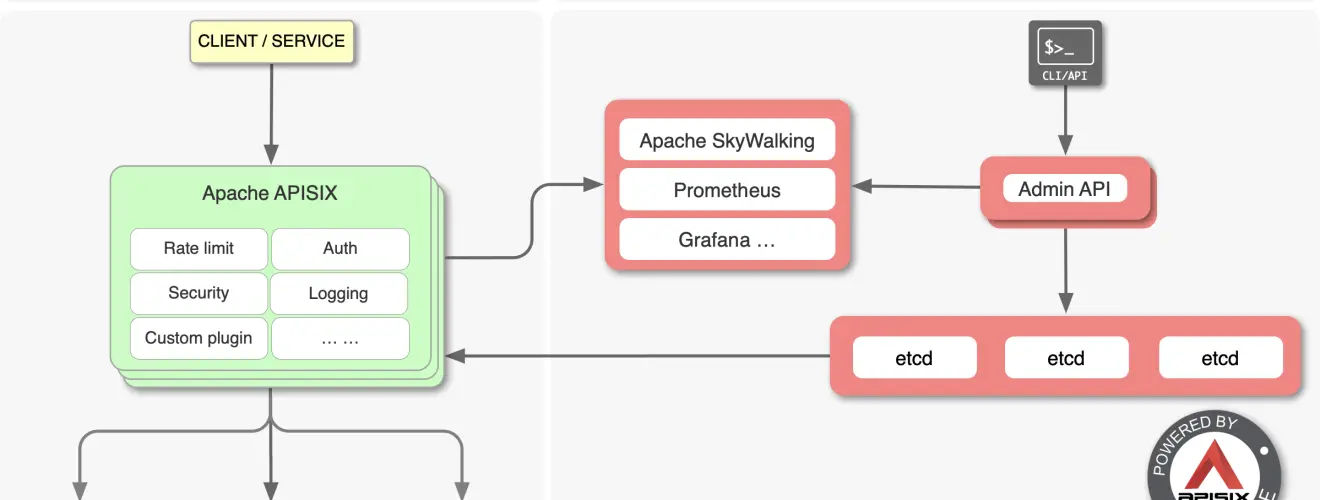
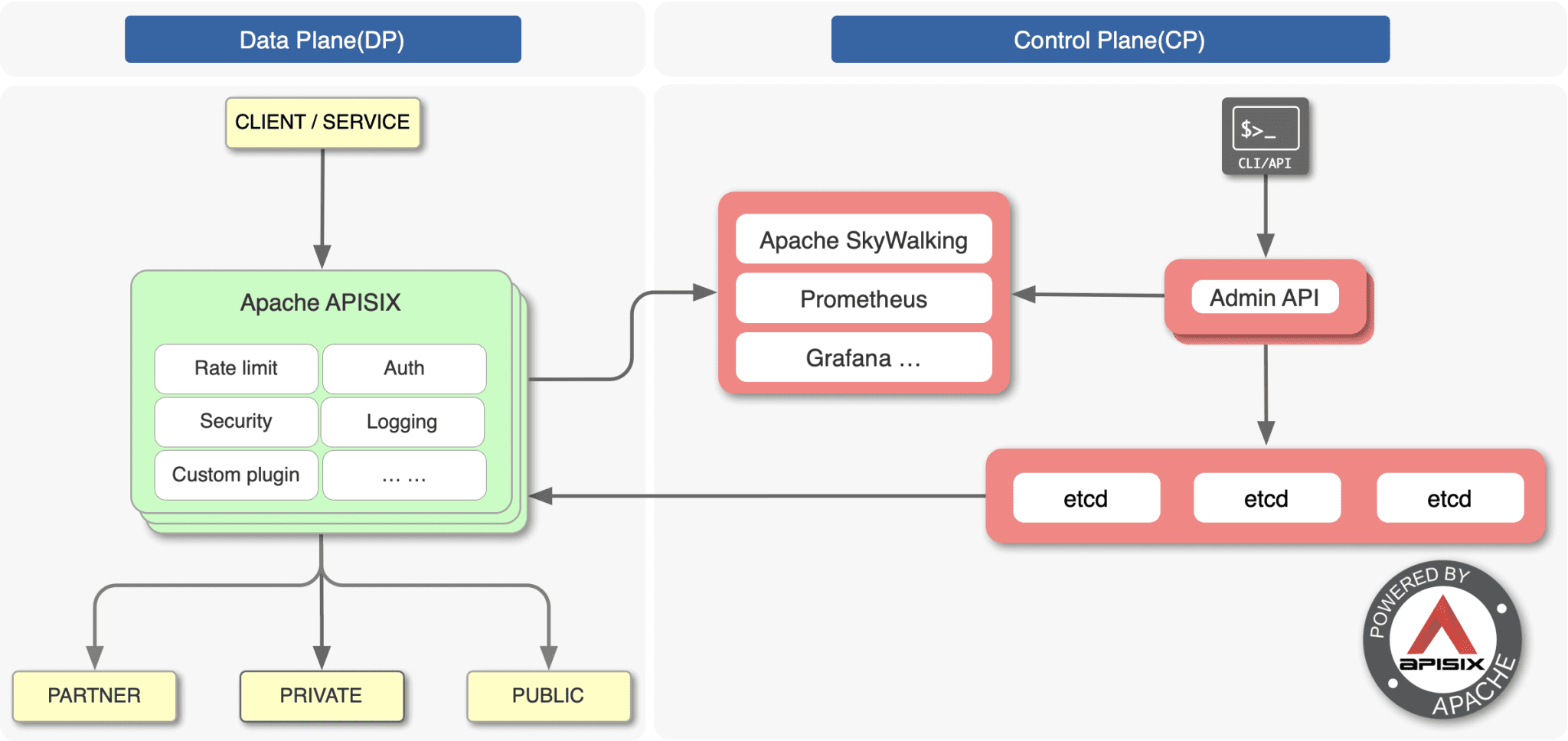
Apache APISIX is a dynamic, real-time, high-performance API gateway. APISIX provides rich traffic management features such as load balancing, dynamic upstream, canary release, circuit breaking, authentication, observability, and more. You can use Apache APISIX to handle traditional north-south traffic, as well as east-west traffic between services. It can also be used as a k8s ingress controller.
Affected version
- Apache APISIX 1.3 – 2.12.1
- Apache APISIX 2.10.0 – 2.10.4 LTS
Unaffected version
- Apache APISIX 2.12.1 (excluding 2.12.1)
- Apache APISIX 2.10.4 (LTS versions) (excluding 2.10.4)
Solution
Mitigation:
You can comment out batch-requests in the conf/config.yaml and conf/config-default.yaml files and restart Apache APISIX.






