CVE-2022-31474: 0-day WordPress BackupBuddy plugin affects 140,000 websites

A high-severity vulnerability in the BackupBuddy WordPress plugin can allow an unauthenticated attacker to obtain website backups that could contain sensitive information.
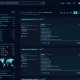
BackupBuddy is a WordPress premium plugin that has a lot of great features for backing up and restoring websites. It has a very easy-to-use interface and is one of the best WordPress full-site backup plugins available. This plugin has been around since 2010 and is very well known and respected. This plugin has around 140,000 active installations.

Image: ithemes
On September 2, the plugin’s developers released an update to address CVE-2022-31474 (CVSS score of 7.5), a security error that allows “an attacker to view the contents of any file on your server that can be read by your WordPress installation. This could include the WordPress wp-config.php file and, depending on your server setup, sensitive files like /etc/passwd.”
According to Wordfence, an unauthenticated attacker can exploit the flaw to download arbitrary files from the affected site which can include sensitive information.
When discovered, the flaw was being actively exploited, and Wordfence warned WordPress website administrators that the plugin had been updated with a new version, urging them to upgrade it immediately.
Over the past two weeks, Wordfence has seen a massive surge in the number of attack attempts targeting the vulnerability, with 4,948,926 attacks. The top 10 Attacking IP Addresses are as follows:
- 195.178.120.89 with 1,960,065 attacks blocked
- 51.142.90.255 with 482,604 attacks blocked
- 51.142.185.212 with 366770 attacks blocked
- 52.229.102.181 with 344604 attacks blocked
- 20.10.168.93 with 341,309 attacks blocked
- 20.91.192.253 with 320,187 attacks blocked
- 23.100.57.101 with 303,844 attacks blocked
- 20.38.8.68 with 302,136 attacks blocked
- 20.229.10.195 with 277,545 attacks blocked
- 20.108.248.76 with 211,924 attacks blocked
A majority of the attacks we have observed are attempting to read the following files:
- /etc/passwd
- /wp-config.php
- .my.cnf
- .accesshash
The CVE-2022-31474 vulnerability only impacts sites running BackupBuddy versions 8.5.8.0 through 8.7.4.1. A complete patch was released last week when BackupBuddy version 8.7.5 was rolled out. WordPress admins are advised to update to a patched version of the plugin as soon as possible.